Q: 1
You want to enable Netskope to gain visibility into your users' cloud application activities in an inline
mode.
In this scenario, which two deployment methods would match your inline use case? (Choose two.)
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 2
Your organization has recently implemented Netskope Private Access. During an investigation, your
security team has asked you to provide a list of all hosts including domains and IP addresses that a
user accessed through Netskope Private Access for the past seven days.
Which two locations in the Netskope Web UI would allow you to obtain and export the requested
data? (Choose two.)
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 3
You need to create a service request ticket for a client-related issue using the Netskope client Ul. In
this scenario, you generate the client logs by right-clicking on the system tray icon and choosing
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 4
Exhibit
 A user is connected to a cloud application through Netskope's proxy.
In this scenario, what information is available at Skope IT? (Choose three.)
A user is connected to a cloud application through Netskope's proxy.
In this scenario, what information is available at Skope IT? (Choose three.)
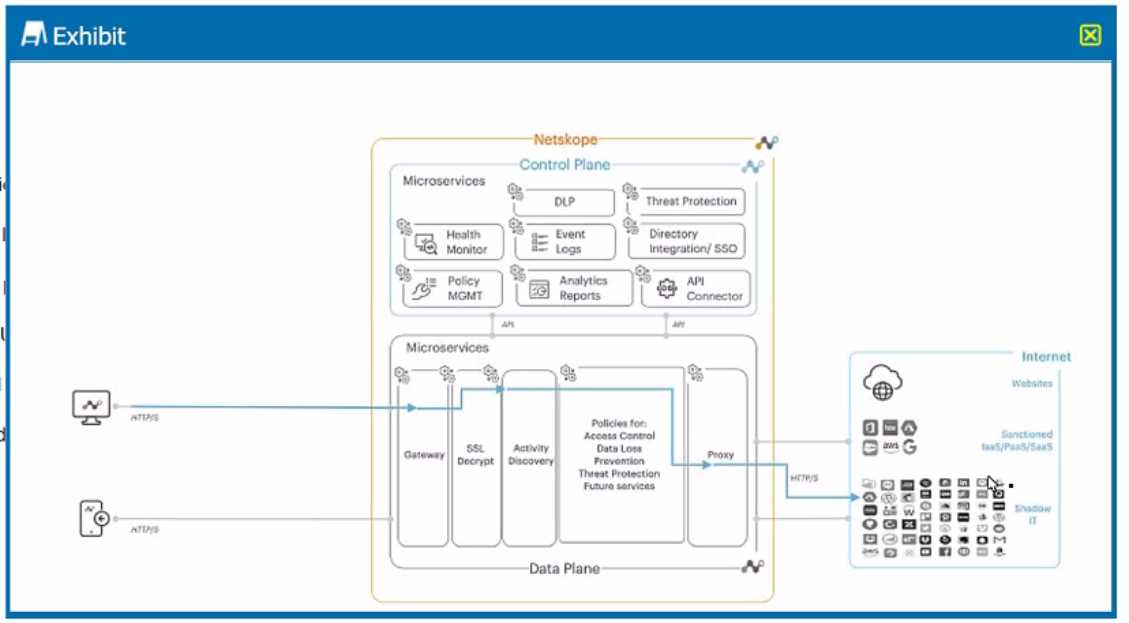 A user is connected to a cloud application through Netskope's proxy.
In this scenario, what information is available at Skope IT? (Choose three.)
A user is connected to a cloud application through Netskope's proxy.
In this scenario, what information is available at Skope IT? (Choose three.)Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 5
You have applied a DLP Profile to block all Personally Identifiable Information data uploads to
Microsoft 365 OneDrive. DLP Alerts are not displayed and no OneDrive-related activities are
displayed in the Skope IT App Events table.
In this scenario, what are two possible reasons for this issue? (Choose two.)
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 6
A company is attempting to steer traffic to Netskope using GRE tunnels. They notice that after the
initial configuration, users cannot access external websites from their browsers.
What are three probable causes for this issue? (Choose three.)
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 7
You are required to mitigate malicious scripts from being downloaded into your corporate devices
every time a user goes to a website. Users need to access websites from a variety of categories,
including new websites.
Which two actions would help you accomplish this task while allowing the user to work? (Choose
two.)
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 8
Which three security controls are offered by the Netskope Cloud platform? (Choose three.)
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 9
You consume application infrastructure (middleware) capabilities by a third-party provider. What is
the cloud service model that you are using in this scenario?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 1 of 20 · Page 1 / 2

