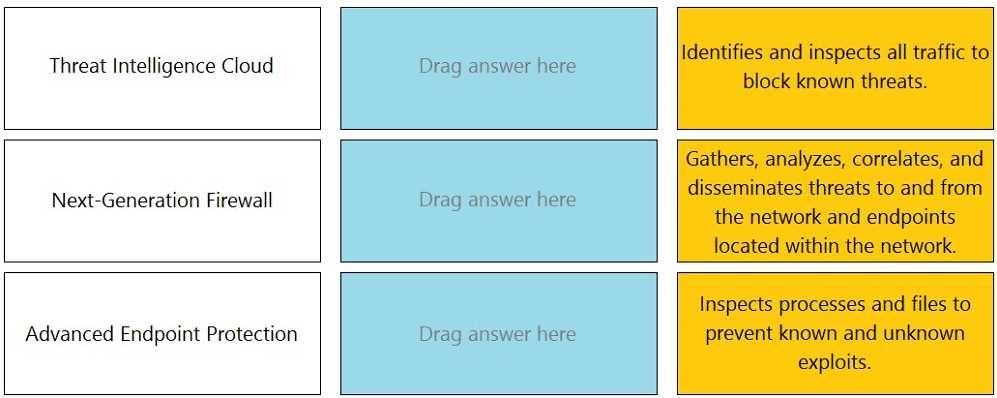
DRAG DROP Match the Palo Alto Networks Security Operating Platform architecture to its description. 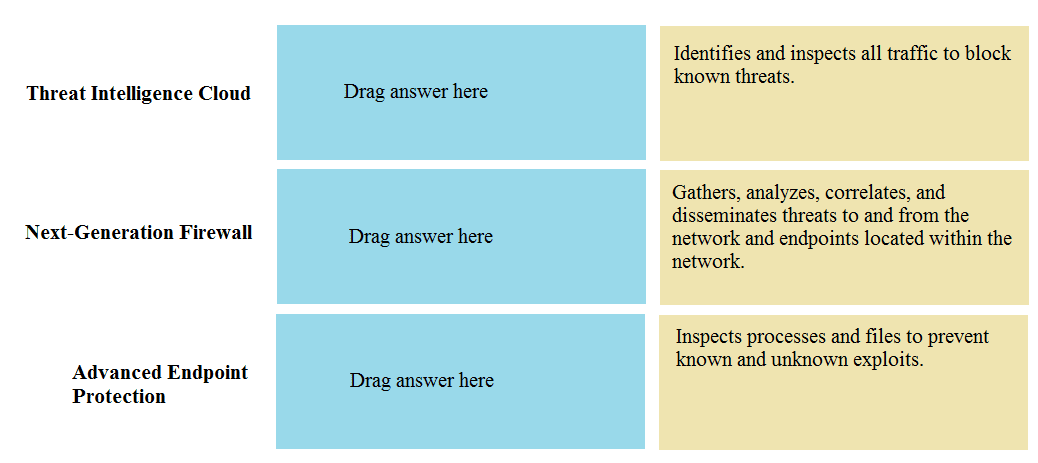
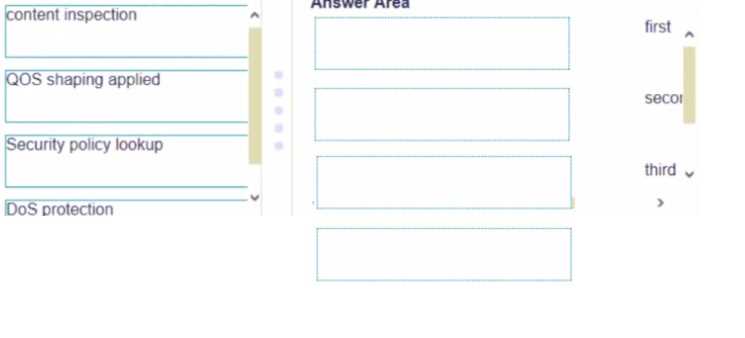
DRAG DROP Place the steps in the correct packet-processing order of operations. 
I don’t think it’s A here. App-ID is for identifying applications, not devices. Device-ID does the device discovery/classification, which is what IoT security profiles need. Sometimes easy to mix them up because both are core Palo Alto features! Pretty sure B is correct but open to other thoughts if I missed something.
Pretty sure it's A here since App-ID does all the application classification, and I think IoT profiles would use that to identify devices. Device-ID sounds more about user logins to me. If the question's really asking about device types on the network, seems like App-ID could fit too.
AMan, Palo loves making these sound trickier than they are. B imo, application filter is what you want since it auto-includes any new high-risk apps in future content updates. Static group (C) wouldn't keep up. Seen similar in practice tests so pretty confident here.
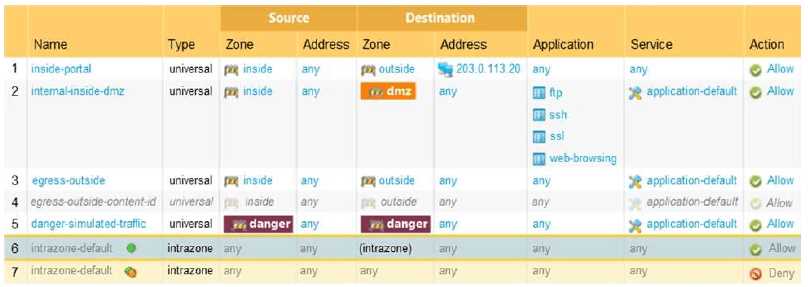
Anyone double-checked if "engress outside" (B) is actually first in policy order? Remember from a mock that ordering matters, since firewall applies rules top to bottom. Just want to confirm we're all reading the zones right.
Is the question asking about what gets inspected if SSL decryption is not enabled? That would rule out D, since decrypted traffic only matters if decryption's on. The "allowed" part is key here too-does the rule use allow or deny action?
Yeah, A and B here. MPLS and broadband internet are the usual SD-WAN transports you see for path selection. USB tethering and loopbacks aren’t really used in real deployments for this purpose. Pretty sure that's what they're after here, but let me know if I'm missing something obvious.
A and D make sense here. Custom apps in PAN firewalls are really about making sure you can identify internal apps that App-ID doesn't recognize (A), plus cutting down on unknown traffic entries in the logs (D). B is more about app categorization, not the main use. Pretty sure this is right, but happy to discuss if anyone disagrees.
Don't think B is right here. The real purpose of custom applications in PAN-OS is to properly identify internal or proprietary traffic (that's A), and also to cut down on all the unknown-tcp/udp noise (that's D). B looks like a trap since recategorizing isn't the main use case. Anyone else see it this way?
DRAG DROP Place the following steps in the packet processing order of operations from first to last.
DRAG DROP Match each feature to the DoS Protection Policy or the DoS Protection Profile.