Kurose, J. F., & Ross, K. W. (2021). Computer Networking: A Top-Down Approach (8th ed.). Pearson.
Firewalls: Section 8.6, "Network Security," describes firewalls as devices that filter packet traffic at the network perimeter (p. 718).
Switches: Section 6.3, "Link-Layer Switches," explains that switches forward frames selectively to output ports based on MAC addresses, thus isolating traffic between ports (p. 518).
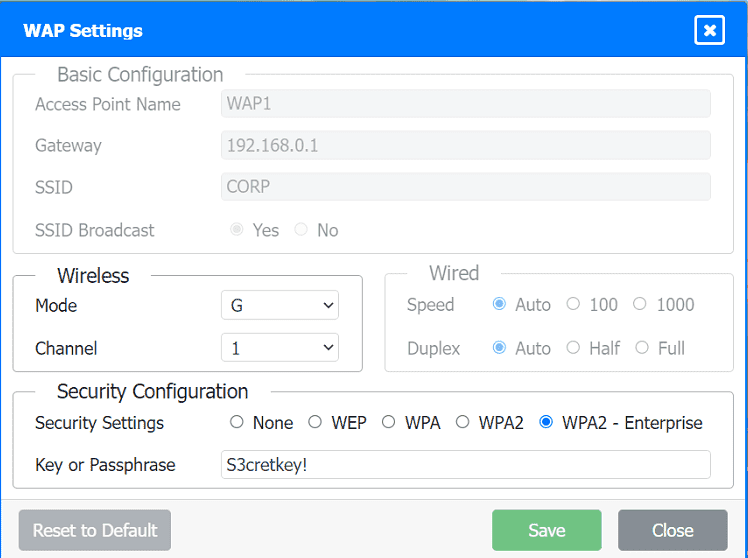
WAP Association: Section 7.3.3, "Associating with an AP," details that a wireless host must configure its network parameters, including the SSID and passphrase, to match the AP's configuration to associate with it (p. 605).
IEEE Std 802.11™-2020. (2020). IEEE Standard for Information Technology—Telecommunications and information exchange between systems Local and metropolitan area networks—Specific requirements - Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications.
Authentication: Section 12.3, "Authentication and association," specifies the procedures for a station to connect to an access point, which involves authenticating with shared credentials such as a Pre-Shared Key (PSK) for WPA2.
Lowe, D. (2018). Networking All-in-One For Dummies (7th ed.). John Wiley & Sons.
Range Extenders: Chapter 7, "Extending Your Network," explains that a wireless extender (or repeater) connects to an existing access point and rebroadcasts its signal, and for it to work, "the SSID, channel, and security settings on the repeater must be configured to match the settings on the main access point" (p. 581).