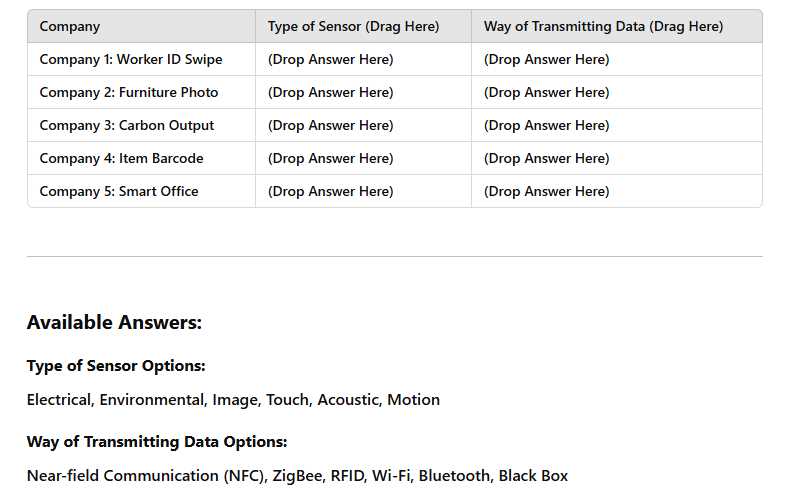
Below are details of five companies that use smart sensors in their operations. Each sensor has a different purpose and a different way of transmitting data. Instructions: Drag and drop the correct Type of Sensor and Way of Transmitting Data into the appropriate boxes for each company.
Q: 11
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 12
David works in the Accounts department of Touchdown Ltd. He has received an email from a sender
he is unfamiliar with. The email asks him to look at an invoice which the sender believes includes an
error. There is an attachment to the email. David has recently undergone Cyber Security training and
is suspicious of the email. What type of security threat does David think the email contains?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 13
In Data Analytics, what is the term 'black swan' used to describe?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 14
Fluffy Pillows Ltd has recently expanded its operations and has hired more staff. These staff will work
remotely, and because of this, Fluffy Pillows Ltd is in need of buying and upgrading their IT systems.
The CEO of Fluffy Pillows is examining the security of currently held data in preparation for the
expansion and has recently completed a document that looks into what data is stored where and
what the consequences would be if this data were to be stolen or corrupted. In his research, he has
found multiple data entries for the same information, which he believes could lead to inaccuracies in
data reporting. He is also concerned that the data isn't being stored securely and is unsure whether
he should retain some of the confidential personal details on employees who have left the business.
He has decided that along with the introduction of new systems, it is important that all members of
staff at Fluffy Pillows are aware of the responsibilities of storing data correctly and the risks of cyber
attacks.
How can Fluffy Pillows ensure data is accessible for the new staff members who work from home?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 11 of 20 · Page 2 / 2