Q: 1
Bob is the CEO of Big Leaf Company and has a lot of sensitive data on his phone. The IT department
has advised Bob he should increase his security measures to protect unwanted people accessing his
phone, which he often leaves on his desk when he goes to Board Meetings. Which of the following
would be most useful to Bob?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 2
Data Processing includes which of the following steps?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 3
Fluffy Pillows Ltd has recently expanded its operations and has hired more staff. These staff will work
remotely and because of this Fluffy Pillows Ltd is in need of buying and upgrading their IT systems.
The CEO of Fluffy Pillows is examining the security of currently held data in preparation for the
expansion and has recently completed a document which looks into what data is stored where and
what the consequences would be if this data were to be stolen or corrupted. In his research he has
found multiple data entries for the same information, which he believes could lead to inaccuracies in
data reporting. He is also concerned that the data isn't being stored securely and is unsure whether
he should retain some of the confidential personal details on employees who have left the business.
He has decided that along with the introduction of new systems it is important that all members of
staff at Fluffy Pillows are aware of the responsibilities of storing data correctly and the risks of cyber
attacks.
What type of document has the CEO created?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 4
Zach is the Head of Procurement at a super secret military base. He does not want anyone outside of
the base to know what he is procuring or which suppliers he uses as this information could be critical
to national defence. He is aware that cyber criminals may be interested in stealing this information
so he has decided to disconnect critical machines and systems from the internet. What is this
approach to data security known as?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 5
Fluffy Pillows Ltd has recently expanded its operations and has hired more staff. These staff will work
remotely and because of this Fluffy Pillows Ltd is in need of buying and upgrading their IT systems.
The CEO of Fluffy Pillows is examining the security of currently held data in preparation for the
expansion and has recently completed a document which looks into what data is stored where and
what the consequences would be if this data were to be stolen or corrupted. In his research he has
found multiple data entries for the same information, which he believes could lead to inaccuracies in
data reporting. He is also concerned that the data isn't being stored securely and is unsure whether
he should retain some of the confidential personal details on employees who have left the business.
He has decided that along with the introduction of new systems it is important that all members of
staff at Fluffy Pillows are aware of the responsibilities of storing data correctly and the risks of cyber
attacks.
What should the CEO do with his wider team?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 6
Ramesh is Head of Procurement at Wiggle Waggle Ltd. He is using a tool for predictive modeling and
statistical analysis to inform upon future strategic business decisions. Which of the following is he
using?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 7
If data has been modified, which aspect of the Information Security triangle has been breached?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 8
Jammy Nuts Ltd is a retailer of electronic components that are commonly used in kitchen appliances.
It has a physical store, but 90% of its sales come through its website. For this reason, the CEO of
Jammy Nuts is keen to use data to benefit the business. In what way can Jammy Nuts use the data
collected to enhance business operations? Select ALL that apply
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 9
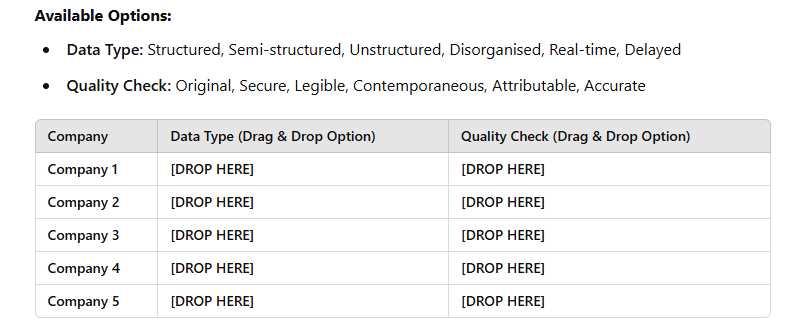
Below are details of 5 companies that use Big Dat a. Each company has a different type of data and applies different quality checks to ensure its accuracy. Instructions: Drag and drop the correct Data Type and Quality Check into the table for each company. Some options may not be used.
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 10
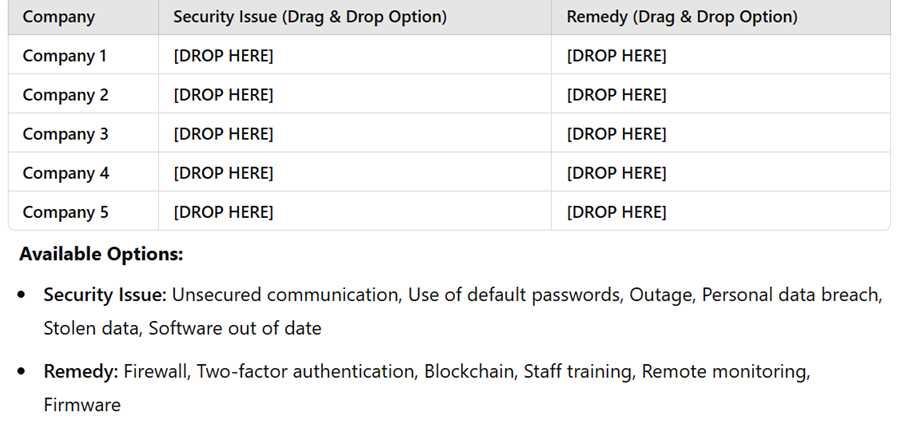
Below are details of five companies that have security issues related to their IT network or data storage. Each company is proposing a remedy to resolve the issue. Instructions: Drag and drop the correct Security Issue and Remedy into the table for each company. Some options may not be used.
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 1 of 20 · Page 1 / 2