Q: 1
When should soft multitenancy be used over hard multitenancy?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 2
On a client machine, what directory (by default) contains sensitive credential information?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 3
What was the name of the precursor to Pod Security Standards?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 4
How can a user enforce the Pod Security Standard without third-party tools?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 5
Which of the following statements correctly describes a container breakout?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 6
Which way of defining security policy brings consistency, minimizes toil, and reduces the probability
of misconfiguration?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 7
Which security knowledge-base focuses specifically on offensive tools, techniques, and procedures?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 8
A cluster is failing to pull more recent versions of images from k8s.gcr.io. Why may this be?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 9
Which of the following snippets from a RoleBinding correctly associates user bob with Role pod-
reader ?


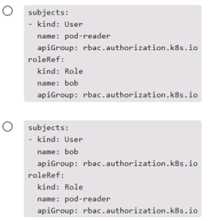
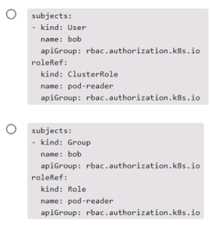
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 1 of 20 · Page 1 / 2

