1. FortiSIEM - Rule Writing Guide Version 7.2.0
Chapter: Rules > Correlation Rules
p. 111. This guide explains the structure of correlation rules
including the use of sub-patterns
conditions (COUNT)
and time windows to detect sequences of events. The configuration in the exhibit directly maps to the examples of building a multi-event correlation rule.
2. Microsoft Corporation
Official Security Documentation
"4625(F): An account failed to log on." This official documentation defines Windows Security Event ID 4625. It also specifies the meaning of the Logon Type field
confirming that Logon Type: 10 corresponds to a RemoteInteractive session
which is used for Terminal Services
Remote Assistance
and Remote Desktop connections.
3. FortiSIEM - Concepts Guide Version 7.2.0
Chapter: Real-time
In-memory Event Correlation
p. 16. This guide describes the purpose of the correlation engine
which is to link discrete events occurring over time into a meaningful incident pattern
such as a brute-force attack. The rule in the exhibit is a practical implementation of this concept.
 Which two conditions will match this rule and subpatterns? (Choose two.)
Which two conditions will match this rule and subpatterns? (Choose two.)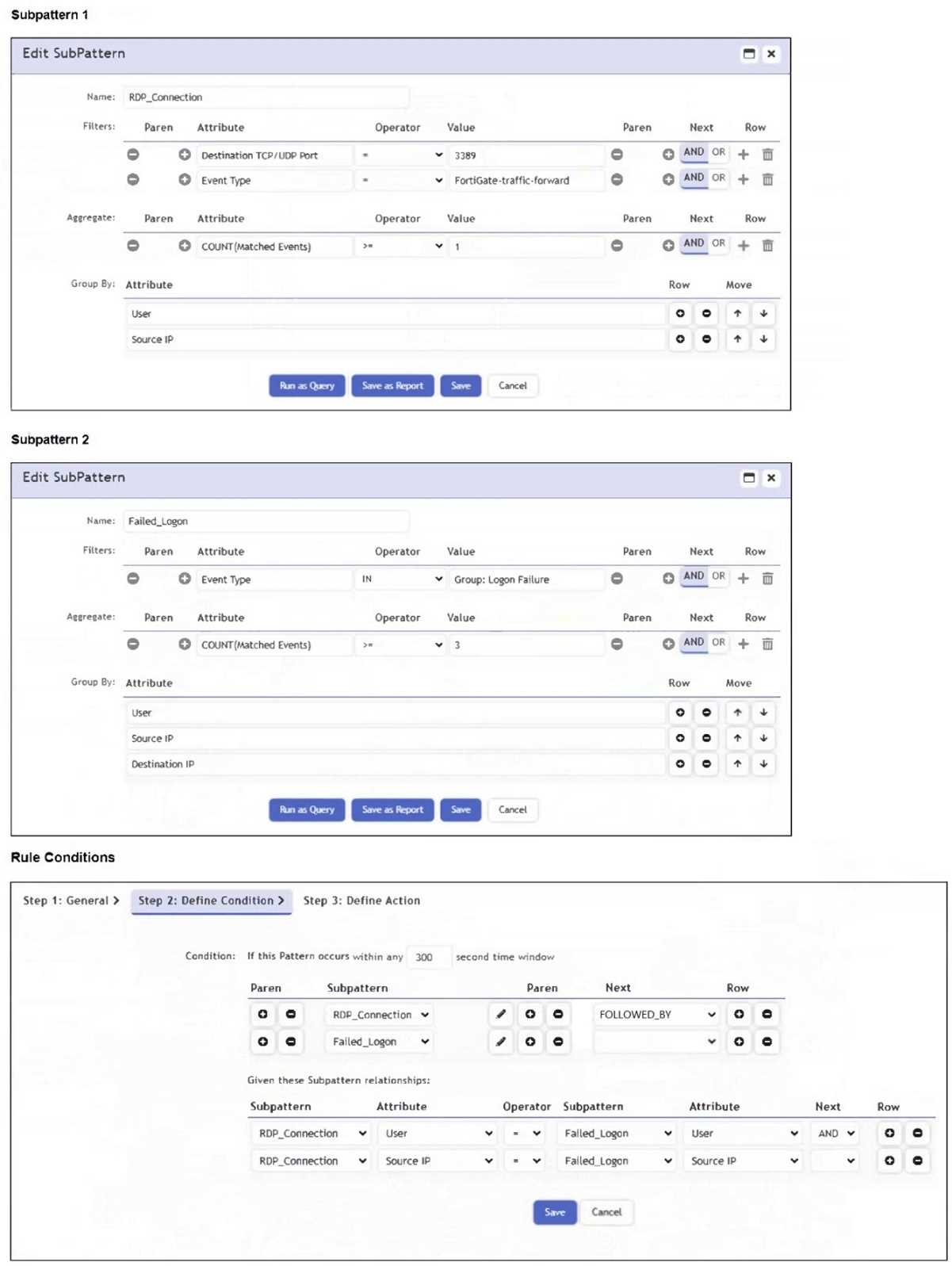 Which two conditions will match this rule and subpatterns? (Choose two.)
Which two conditions will match this rule and subpatterns? (Choose two.)
