Q: 1
To complete the final step of a Security Fabric configuration, an administrator must authorize all the
devices on which device?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 2
Which two protocol options are available on the CLI but not on the GUI when configuring an SD-WAN Performance SLA? (Choose two.)
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 3
Consider the topology:
Application on a Windows machine FGT--> Telnet to Linux server.
An administrator is investigating a problem where an application establishes a Telnet session to a Linux
server over the SSL VPN through FortiGate and the idle session times out after about 90 minutes. The
administrator would like to increase or disable this timeout.
The administrator has already verified that the issue is not caused by the application or Linux server. This
issue does not happen when the application establishes a Telnet connection to the Linux server directly on
the LAN.
What two changes can the administrator make to resolve the issue without affecting services running
through FortiGate? (Choose two.)
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 4
An administrator wants to configure timeouts for users. Regardless of the user's behavior, the timer should start as soon as the user authenticates and expire after the configured value. Which timeout option should be configured on FortiGate?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 5
Which of the following statements is true regarding SSL VPN settings for an SSL VPN portal?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 6
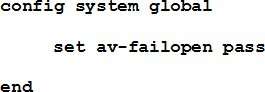
Examine this FortiGate configuration:
 Examine the output of the following debug command:
Examine the output of the following debug command:
 Based on the diagnostic outputs above, how is the FortiGate handling the traffic for new sessions that
require inspection?
Based on the diagnostic outputs above, how is the FortiGate handling the traffic for new sessions that
require inspection?
 Examine the output of the following debug command:
Examine the output of the following debug command:
 Based on the diagnostic outputs above, how is the FortiGate handling the traffic for new sessions that
require inspection?
Based on the diagnostic outputs above, how is the FortiGate handling the traffic for new sessions that
require inspection?Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 7
Refer to the exhibit. 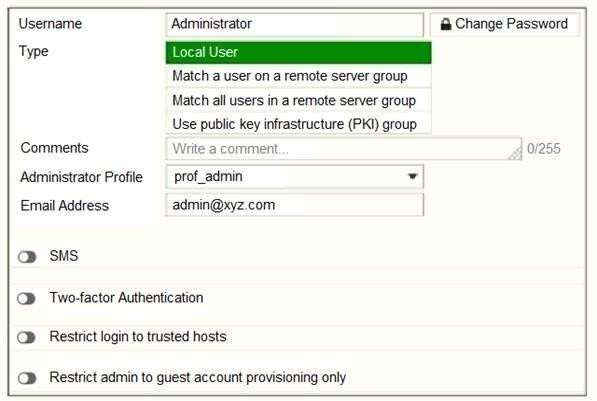
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 8
Which two statements are correct about SLA targets? (Choose two.)
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 9
Which security feature does FortiGate provide to protect servers located in the internal networks from
attacks such as SQL injections?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 1 of 20 · Page 1 / 2

