Q: 7
Refer to the exhibit.
 Based on the Security Fabric automation settings, what action will be taken on compromised
endpoints?
Based on the Security Fabric automation settings, what action will be taken on compromised
endpoints?
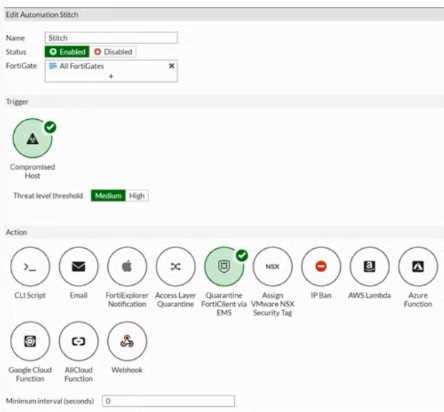 Based on the Security Fabric automation settings, what action will be taken on compromised
endpoints?
Based on the Security Fabric automation settings, what action will be taken on compromised
endpoints?Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.

