Q: 1
Which two capabilities does FortiAuthenticator offer when acting as a self-signed or local CA?
(Choose two.)
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 2
You are the administrator of a large network that includes a large local user database on the current
FortiAuthenticator. You want to import all the local users into a new FortiAuthenticator device.
Which method should you use to migrate the local users?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 3
Which FSSO discovery method transparently detects logged off users without having to rely on
external features such as WMI polling?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 4
What are three key features of FortiAuthenticator? (Choose three.)
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 5
An employee lost their assigned token and needs to authenticate to a resource which requires two
factor authentication. The user does not have access to SMS or email.
How can an administrator provide access for the user?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 6
When performing a remote LDAP server integration with FortiAuthenticator, how do server type
templates assist with the integration?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 7
Which two data items are not synchronized in an active-active HA deployment? (Choose two.)
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 8
An administrator wants users and devices that cannot be identified transparently, such as Android
BYOD devices, to be able to register and create their own credentials.
In this case, which FortiAuthenticator user identity discovery method can the administrator use?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 9
When configuring an active-passive HA deployment, what is the recommended data synchronization
path?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 10
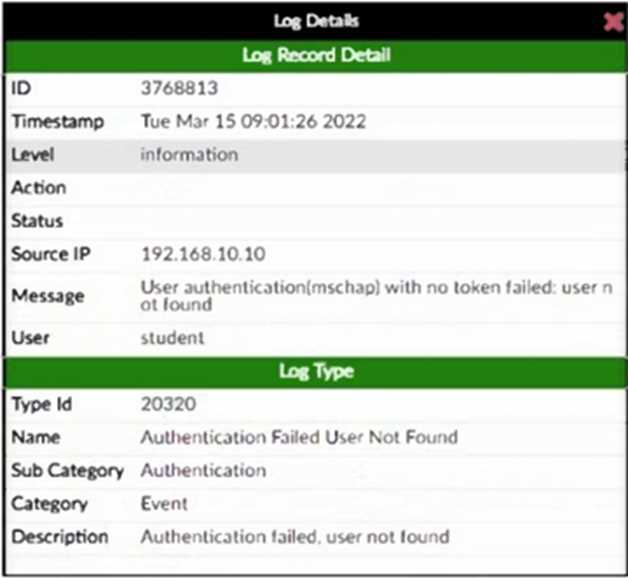
Refer to the exhibits.
Event Log
Event Detail
 An administrator has configured several wireless APs to use FortiAuthenticator as their RADIUS
server. One user is unable to successfully authenticate. The user record exists in the system, but the
FortiAuthenticator log shows Authentication failed, user not found.
What is the most likely cause of the problem?
An administrator has configured several wireless APs to use FortiAuthenticator as their RADIUS
server. One user is unable to successfully authenticate. The user record exists in the system, but the
FortiAuthenticator log shows Authentication failed, user not found.
What is the most likely cause of the problem?
 An administrator has configured several wireless APs to use FortiAuthenticator as their RADIUS
server. One user is unable to successfully authenticate. The user record exists in the system, but the
FortiAuthenticator log shows Authentication failed, user not found.
What is the most likely cause of the problem?
An administrator has configured several wireless APs to use FortiAuthenticator as their RADIUS
server. One user is unable to successfully authenticate. The user record exists in the system, but the
FortiAuthenticator log shows Authentication failed, user not found.
What is the most likely cause of the problem?Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 1 of 20 · Page 1 / 2

