The Dell Services team suggest implementing a system that requires individuals to provide a PIN and
biometric information to access their device.
Which type of multifactor authentication should be suggested?
The Dell Services team suggest implementing a system that requires individuals to provide a PIN and
biometric information to access their device.
Which type of multifactor authentication should be suggested?Q: 1
A .R.T.I.E. has an evolving need, which was amplified during the incidents. Their complex and
dispersed IT environments have thousands of users, applications, and resources to manage. Dell
found that the existing Identity and Access Management was limited in its ability to apply expanding
IAM protection to applications beyond the core financial and human resource management
application. A .R.T.I.E. also did not have many options for protecting their access especially in the
cloud. A .R.T.I.E. were also not comfortable exposing their applications for remote access.
Dell recommended adopting robust IAM techniques like mapping out connections between
privileged users and admin accounts, and the use multifactor authentication.
 The Dell Services team suggest implementing a system that requires individuals to provide a PIN and
biometric information to access their device.
Which type of multifactor authentication should be suggested?
The Dell Services team suggest implementing a system that requires individuals to provide a PIN and
biometric information to access their device.
Which type of multifactor authentication should be suggested?
 The Dell Services team suggest implementing a system that requires individuals to provide a PIN and
biometric information to access their device.
Which type of multifactor authentication should be suggested?
The Dell Services team suggest implementing a system that requires individuals to provide a PIN and
biometric information to access their device.
Which type of multifactor authentication should be suggested?Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 2
The cybersecurity team must create a resilient security plan to address threats. To accomplish this,
the threat intelligence team performed a thorough analysis of the A .R.T.I.E. threat landscape. The
result was a list of vulnerabilities such as social engineering, zero-day exploits, ransomware, phishing
emails, outsourced infrastructure, and insider threats.
Using the information in the case study and the scenario for this question, which vulnerability type
exposes the data and infrastructure of A.R.T.I.E .?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 3
The security team recommends the use of User Entity and Behavior Analytics (UEBA) in order to
monitor and detect unusual traffic patterns, unauthorized data access, and malicious activity of A
.R.T.I.E. The monitored entities include A .R.T.I.E. processes, applications, and network devices
Besides the use of UEBA, the security team suggests a customized and thorough implementation
plan for the organization.
What are the key attributes that define UEBA?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 4
A Zero Trust security strategy is defined by which of the primary approaches?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 5
An A .R.T.I.E. employee received an email with an invoice that looks official for $200 for a one-year
subscription. It clearly states: "Please do not reply to this email," but provides a Help and Contact
button along with a phone number.
What is the type of risk if the employee clicks the Help and Contact button?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 6
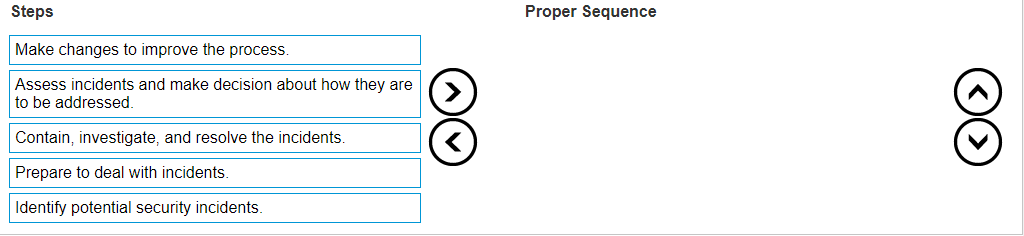
DRAG DROP The cybersecurity team created a detailed security incident management procedures training program to manage any probable incidents at A .R.T.I.E. Arrange the steps in the proper sequence to best manage cybersecurity incidents.
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 7
DRAG DROP Match the security hardening type with the hardening techniques.
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 8
DRAG DROP Dell Services team cannot eliminate all risks, but they can continually evaluate the resilience and preparedness of A .R.T.I.E. by using the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF). Match the core NIST CSF component functions with the description that the Dell Services team would have recommended to A .R.T.I.E.
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 9
To minimize the cost and damage of ransomware attacks the cybersecurity team provided static
analysis of files in an environment and compare a ransomware sample hash to known data.
Which detection mechanism is used to detect data theft techniques to access valuable information
and hold ransom?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 1 of 20 · Page 1 / 2