Q: 11
Which of the following statements describe the main purposes of a Regulatory policy?
Each correct answer represents a complete solution. Choose all that apply.
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 12
You work as an analyst for Tech Perfect Inc. You want to prevent information flow that may cause a
conflict of interest in your organization representing competing clients. Which of the following
security models will you use?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 13
The DARPA paper defines various procedural patterns to perform secure system development
practices. Which of the following patterns does it include?
Each correct answer represents a complete solution. Choose three.
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 14
Software Development Life Cycle (SDLC) is a logical process used by programmers to develop
software. Which of the following SDLC phases meets the audit objectives defined below:
System and data are validated.
System meets all user requirements.
System meets all control requirements.
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 15
Which of the following strategies is used to minimize the effects of a disruptive event on a company,
and is created to prevent interruptions to normal business activity?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 16
You are responsible for network and information security at a large hospital. It is a significant concern
that any change to any patient record can be easily traced back to the person who made that change.
What is this called?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
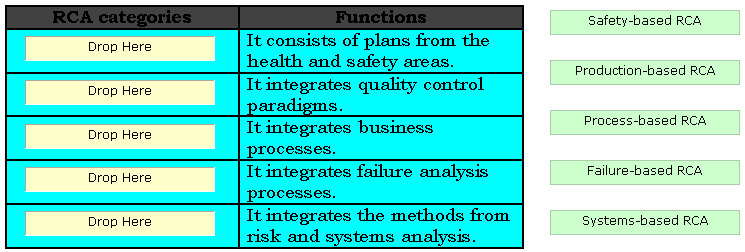
Q: 17
DRAG DROP
RCA (root cause analysis) is an iterative and reactive method that identifies the root cause of various
incidents, and the actions required to prevent these incidents from reoccurring. RCA is classified in
various categories. Choose appropriate categories and drop them in front of their respective
functions.

Your Answer
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 18
In which of the following DIACAP phases is residual risk analyzed?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 19
FILL IN THE BLANK Fill in the blank with an appropriate phrase. models address specifications, requirements, design, verification and validation, and maintenance activities.
Your Answer
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 11 of 20 · Page 2 / 2

