Q: 1
Security is a state of well-being of information and infrastructures in which the possibilities of
successful yet undetected theft, tampering, and/or disruption of information and services are kept
low or tolerable. Which of the following are the elements of security? Each correct answer
represents a complete solution. Choose all that apply.
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 2
Which of the following phases of NIST SP 800-37 C&A methodology examines the residual risk for
acceptability, and prepares the final security accreditation package?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 3
In which of the following testing methods is the test engineer equipped with the knowledge of
system and designs test cases or test data based on system knowledge?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 4
The Project Risk Management knowledge area focuses on which of the following processes?
Each correct answer represents a complete solution. Choose all that apply.
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 5
According to the NIST SAMATE, dynamic analysis tools operate by generating runtime vulnerability
scenario using some functions. Which of the following are functions that are used by the dynamic
analysis tools and are summarized in the NIST SAMATE? Each correct answer represents a complete
solution. Choose all that apply.
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 6
Which of the following steps of the LeGrand Vulnerability-Oriented Risk Management method
determines the necessary compliance offered by risk management practices and assessment of risk
levels?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
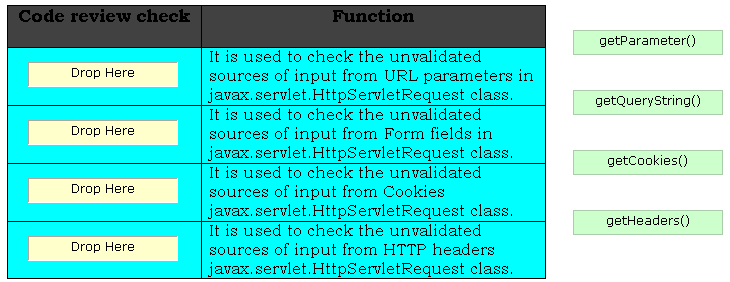
Q: 7
DRAG DROP
Security code review identifies the unvalidated input calls made by an attacker and avoids those calls
to be processed by the server. It performs various review checks on the stained calls of servlet for
identifying unvalidated input from the attacker. Choose the appropriate review checks and drop
them in front of their respective functions.

Your Answer
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 8
Which of the following are examples of passive attacks?
Each correct answer represents a complete solution. Choose all that apply.
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 9
An asset with a value of $600,000 is subject to a successful malicious attack threat twice a year. The
asset has an exposure of 30 percent to the threat. What will be the annualized loss expectancy?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 1 of 20 · Page 1 / 2

