1. Kubernetes Official Documentation
"Ingress": This document details the structure of an Ingress resource
including the tls section for specifying the secret that contains the TLS private key and certificate. See the "TLS" subsection.
Source: Kubernetes Authors
Ingress Concepts
kubernetes.io.
Reference: kubernetes.io/docs/concepts/services-networking/ingress/#tls
2. Kubernetes Official Documentation
"Service": This page explains how a Service exposes an application running on a set of Pods. It covers the use of selector to match Pod labels and ports to define the service endpoint.
Source: Kubernetes Authors
Service Concepts
kubernetes.io.
Reference: kubernetes.io/docs/concepts/services-networking/service/#defining-a-service
3. Kubernetes Official Documentation
"Secrets": This documentation describes how to manage sensitive information. The "TLS secrets" section specifically outlines the creation and usage of secrets for TLS certificates.
Source: Kubernetes Authors
Secret Concepts
kubernetes.io.
Reference: kubernetes.io/docs/concepts/configuration/secret/#tls-secrets
4. UC Berkeley EECS Courseware
CS 162: Lecture slides from this operating systems course cover Kubernetes networking concepts
including the role of Ingress in managing external access to services in a cluster
often in conjunction with TLS for security.
Source: University of California
Berkeley
Department of Electrical Engineering and Computer Sciences.
Reference: CS 162
Lecture 22: "Cloud Computing"
Slide 67 "Kubernetes Ingress". (Available via course website archives).
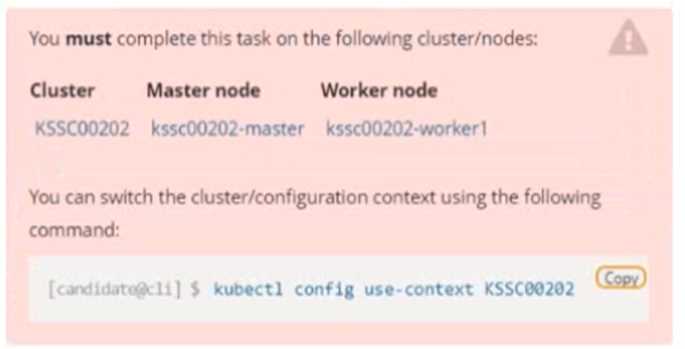 Context
A container image scanner is set up on the cluster, but it's not yet fully integrated into the cluster s
configuration. When complete, the container image scanner shall scan for and reject the use of
vulnerable images.
Task
Context
A container image scanner is set up on the cluster, but it's not yet fully integrated into the cluster s
configuration. When complete, the container image scanner shall scan for and reject the use of
vulnerable images.
Task
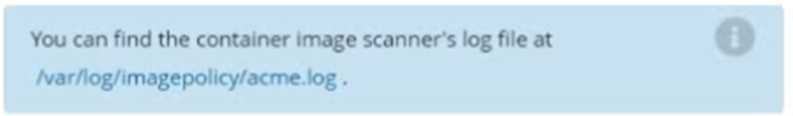
 Given an incomplete configuration in directory /etc/kubernetes/epconfig and a functional container
image scanner with HTTPS endpoint https://wakanda.local:8081 /image_policy :
1. Enable the necessary plugins to create an image policy
2. Validate the control configuration and change it to an implicit deny
3. Edit the configuration to point to the provided HTTPS endpoint correctly
Finally, test if the configuration is working by trying to deploy the vulnerable resource
/root/KSSC00202/vulnerable-resource.yml.
Given an incomplete configuration in directory /etc/kubernetes/epconfig and a functional container
image scanner with HTTPS endpoint https://wakanda.local:8081 /image_policy :
1. Enable the necessary plugins to create an image policy
2. Validate the control configuration and change it to an implicit deny
3. Edit the configuration to point to the provided HTTPS endpoint correctly
Finally, test if the configuration is working by trying to deploy the vulnerable resource
/root/KSSC00202/vulnerable-resource.yml.

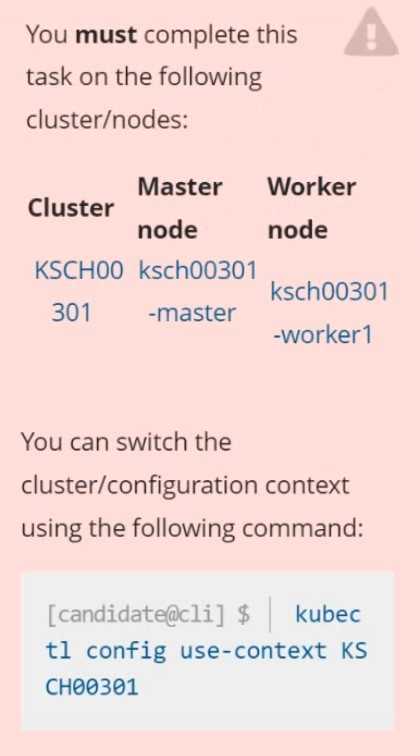 Context
Your organization’s security policy includes:
ServiceAccounts must not automount API credentials
ServiceAccount names must end in "-sa"
The Pod specified in the manifest file /home/candidate/KSCH00301 /pod-m
nifest.yaml fails to schedule because of an incorrectly specified ServiceAccount.
Complete the following tasks:
Task
1. Create a new ServiceAccount named frontend-sa in the existing namespace q
a. Ensure the ServiceAccount does not automount API credentials.
2. Using the manifest file at /home/candidate/KSCH00301 /pod-manifest.yaml, create the Pod.
3. Finally, clean up any unused ServiceAccounts in namespace qa.
Context
Your organization’s security policy includes:
ServiceAccounts must not automount API credentials
ServiceAccount names must end in "-sa"
The Pod specified in the manifest file /home/candidate/KSCH00301 /pod-m
nifest.yaml fails to schedule because of an incorrectly specified ServiceAccount.
Complete the following tasks:
Task
1. Create a new ServiceAccount named frontend-sa in the existing namespace q
a. Ensure the ServiceAccount does not automount API credentials.
2. Using the manifest file at /home/candidate/KSCH00301 /pod-manifest.yaml, create the Pod.
3. Finally, clean up any unused ServiceAccounts in namespace qa.