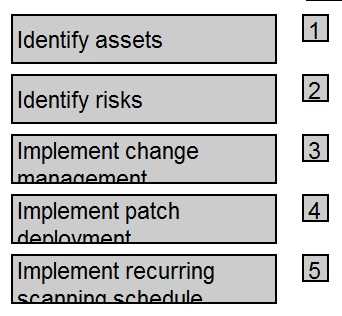
The MITRE Corporation. (2010). A Reference Architecture for Enterprise Vulnerability Management. Section 2.1, "Foundational Components," emphasizes that Asset Management is a prerequisite for the vulnerability management lifecycle, which consists of scanning, analysis, and remediation.
National Institute of Standards and Technology (NIST). (2020). Special Publication (SP) 800-53, Revision 5: Security and Privacy Controls for Information Systems and Organizations. Control RA-5 (Vulnerability Monitoring and Scanning) mandates scanning systems, which presupposes an inventory defined in CM-8 (System Component Inventory). Furthermore, remediation is governed by CM-3 (Configuration Change Control), reinforcing the need for change management before implementing fixes.
Enck, W., & Moyer, T. (2007). Towards a More Secure, Available, and Manageable Enterprise Infrastructure. MIT Lincoln Laboratory. The paper discusses the importance of a structured approach starting with asset discovery, followed by vulnerability assessment, and then controlled remediation, highlighting that "patch management is the primary mechanism for mitigating software vulnerabilities" (p. 2) and must be done in a controlled manner.
Al-Shaer, E., & El-Atawy, A. (2008). Network configuration in a box: A toolbox for building secure and available network configuration management systems. Proceedings of the 4th International Workshop on Security and Trust Management (STM '08). The work implicitly supports the sequence by discussing the necessity of knowing the network state (assets and configuration) before managing changes and vulnerabilities. DOI: 10.1007/978-3-540-85247-0_1