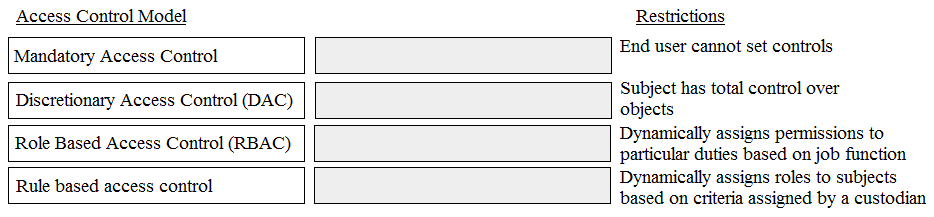
National Institute of Standards and Technology (NIST). (2017). NIST Special Publication 800-192: Verification and Test Methods for Access Control Policies/Models. Section 2.1, "Access Control Policies/Models Definitions". This document defines MAC as non-discretionary and DAC as allowing owners to specify access. DOI: https://doi.org/10.6028/NIST.SP.800-192
National Institute of Standards and Technology (NIST). (n.d.). Glossary: Role-Based Access Control. Computer Security Resource Center. Retrieved from https://csrc.nist.gov/glossary/term/role_based_access_control. This source defines RBAC as being "based on user roles...Role permissions may be inherited through a role hierarchy and typically reflect the permissions needed to perform defined functions within an organization."
Stallings, W., & Brown, L. (2018). Computer Security: Principles and Practice (4th ed.). Pearson. Chapter 4, "Access Control". This textbook provides foundational academic descriptions, explaining that with DAC, "an entity may be granted access rights that enable the entity, by its own volition, to enable another entity to access some resource" (p. 116), whereas with MAC, controls are "not subject to the object owner's discretion" (p. 120).
Hu, V. C., Ferraiolo, D., Kuhn, R., Friedman, A. R., Lang, A. J., et al. (2013). Guide to Attribute Based Access Control (ABAC) Definition and Considerations. NIST Special Publication 800-162. Section 2.3.4 discusses how ABAC (a form of rule-based control) can be used to implement dynamic role assignment, stating, "In some cases the subject's assigned role...may be determined dynamically from subject attributes." This directly supports the match for rule-based access control. DOI: https://doi.org/10.6028/NIST.SP.800-162