Q: 11
A security analyst has discovered that an application has failed to run. Which of the following is the
tool MOST
likely used by the analyst for the initial discovery?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 12
Which of the following attacks involves sending a large amount of spoofed User Datagram Protocol
(UDP) traffic to a router’s broadcast address within a network?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 13
A company help desk is flooded with calls regarding systems experiencing slow performance and
certain Internet sites taking a long time to load or not loading at all. The security operations center
(SOC) analysts who receive these calls take the following actions:
-
Running antivirus scans on the affected user machines
-
Checking department membership of affected users
-
Checking the host-based intrusion prevention system (HIPS) console for affected user
machine alerts
-
Checking network monitoring tools for anomalous activities
Which of the following phases of the incident response process match the actions taken?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 14
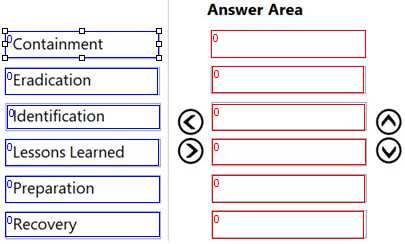
DRAG DROP What is the correct order of the DFIR phases?
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 15
Which of the following should normally be blocked through a firewall?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 16
After imaging a disk as part of an investigation, a forensics analyst wants to hash the image using a
tool that supports piecewise hashing. Which of the following tools should the analyst use?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 17
Which of the following backup strategies will result in the shortest backup time during weekdays and
use the least amount of storage space but incur the longest restore time?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 18
A common formula used to calculate risk is:
+ Threats + Vulnerabilities = Risk. Which of the
following represents the missing factor in this formula?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 19
An automatic vulnerability scan has been performed. Which is the next step of the vulnerability
assessment process?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 11 of 20 · Page 2 / 2