Analysis and Remediation Options for Each IoC:
IoC 1:
Evidence:
Source: Apache_httpd
Type: DNSQ
Dest: @10.1.1.1:53,@10.1.2.5
Data: update.s.domain, CNAME 3a129sk219r9slmfkzzz000.s.domain, 108.158.253.253
Analysis:
Analysis: The service is attempting to resolve a malicious domain.
Reason: The DNS queries and the nature of the CNAME resolution indicate that the service is trying
to resolve potentially harmful domains, which is a common tactic used by malware to connect to
command-and-control servers.
Remediation:
Remediation: Implement a blocklist for known malicious ports.
Reason: Blocking known malicious domains at the DNS level prevents the resolution of harmful
domains, thereby protecting the network from potential connections to malicious servers.
IoC 2:
Evidence:
Src: 10.0.5.5
Dst: 10.1.2.1, 10.1.2.2, 10.1.2.3, 10.1.2.4, 10.1.2.5
Proto: IP_ICMP
Data: ECHO
Action: Drop
Analysis:
Analysis: Someone is footprinting a network subnet.
Reason: The repeated ICMP ECHO requests to different addresses within a subnet indicate that
someone is scanning the network to discover active hosts, a common reconnaissance technique used
by attackers.
Remediation:
Remediation: Block ping requests across the WAN interface.
Reason: Blocking ICMP ECHO requests on the WAN interface can prevent attackers from using ping
sweeps to gather information about the network topology and active devices.
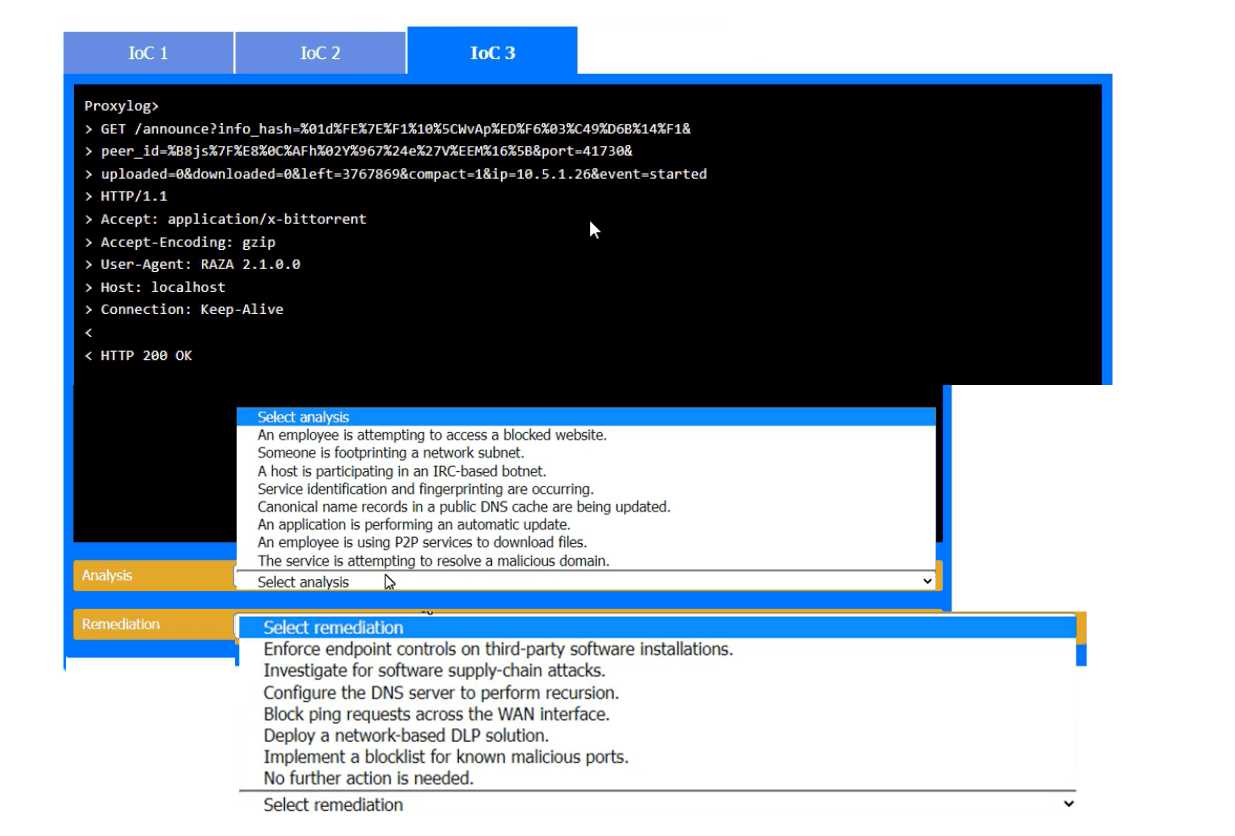
IoC 3:
Evidence:
Proxylog:
GET
/announce?info_hash=%01dff%27f%21%10%c5%wp%4e%1d%6f%63%3c%49%6d&peer_id%3dxJFS
Uploaded=0&downloaded=0&left=3767869&compact=1&ip=10.5.1.26&event=started
User-Agent: RAZA 2.1.0.0
Host: localhost
Connection: Keep-Alive
HTTP200 OK
Analysis:
Analysis: An employee is using P2P services to download files.
Reason: The HTTP GET request with parameters related to a BitTorrent client indicates that the
employee is using peer-to-peer (P2P) services, which can lead to unauthorized data transfer and
potential security risks.
Remediation:
Remediation: Enforce endpoint controls on third-party software installations.
Reason: By enforcing strict endpoint controls, you can prevent the installation and use of
unauthorized software, such as P2P clients, thereby mitigating the risk of data leaks and other
security threats associated with such applications.
Reference:
CompTIA Security+ Study Guide: This guide offers detailed explanations on identifying and mitigating
various types of Indicators of Compromise (IoCs) and the corresponding analysis and remediation
strategies.
CompTIA Security+ Exam Objectives: These objectives cover key concepts in network security
monitoring and incident response, providing guidelines on how to handle different types of security
events.
Security Operations Center (SOC) Best Practices: This resource outlines effective strategies for
analyzing and responding to anomalous events within a SOC, including the use of blocklists, endpoint
controls, and network configuration changes.
By accurately analyzing the nature of each IoC and applying the appropriate remediation measures,
the organization can effectively mitigate potential security threats and maintain a robust security
posture.