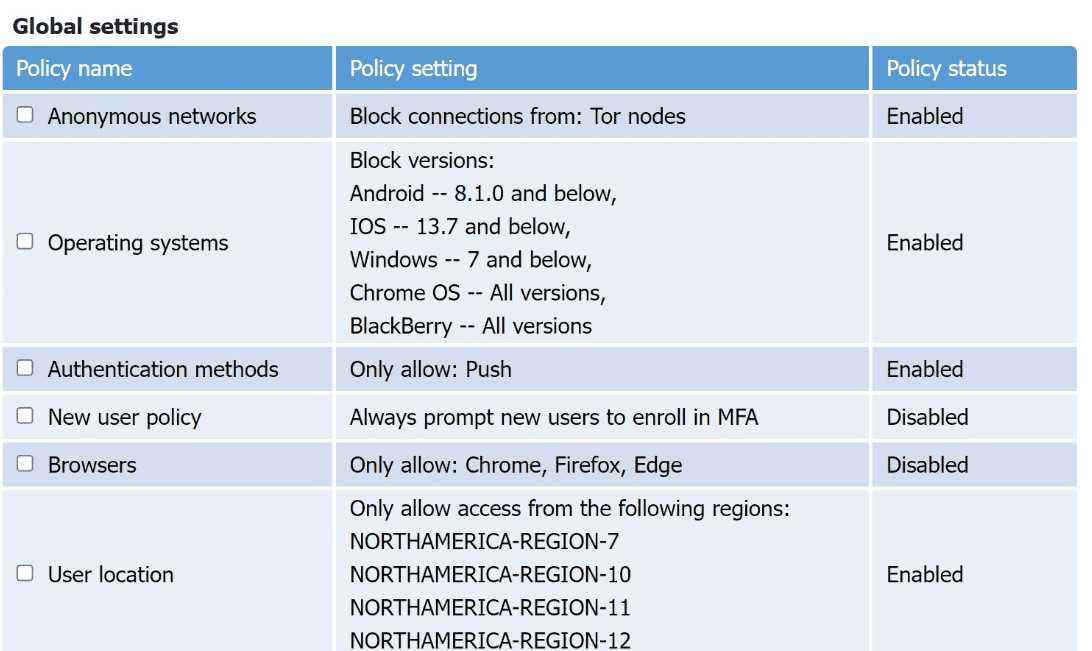
A security architect discovers the following while reviewing code for a company’s website:
selection = "SELECT Item FROM Catalog WHERE ItemID * " & Request("ItemID”)
Which of the following should the security architect recommend?
 Which of the following is the most likely reason for the successful attack?
Which of the following is the most likely reason for the successful attack?












SIMULATION A product development team has submitted code snippets for review prior to release. INSTRUCTIONS Analyze the code snippets, and then select one vulnerability, and one fix for each code snippet. Code Snippet 1 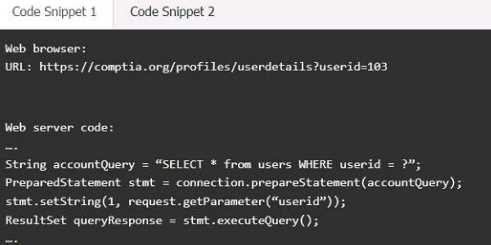
SQL injection
Cross-site request forgery
Server-side request forgery
Indirect object reference
Cross-site scripting
Fix 1:
Perform input sanitization of the userid field.
Perform output encoding of queryResponse,
Ensure usex:ia belongs to logged-in user.
Inspect URLS and disallow arbitrary requests.
Implement anti-forgery tokens.
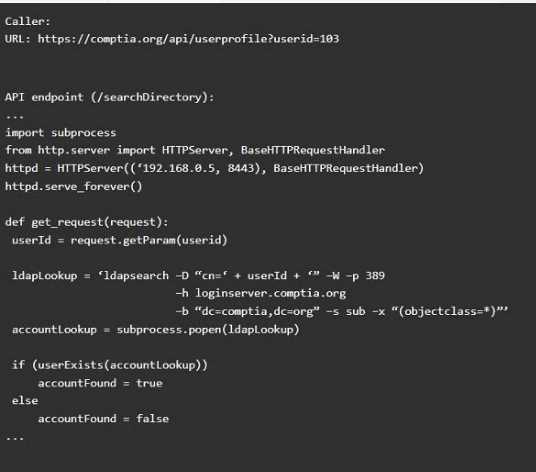
Vulnerability 2
1) Denial of service
2) Command injection
3) SQL injection
4) Authorization bypass
5) Credentials passed via GET Fix 2
A) Implement prepared statements and bind variables.
B) Remove the serve_forever instruction.
C) Prevent the "authenticated" value from being overridden by a GET parameter.
D) HTTP POST should be used for sensitive parameters.
E) Perform input sanitization of the userid field.

