Q: 9
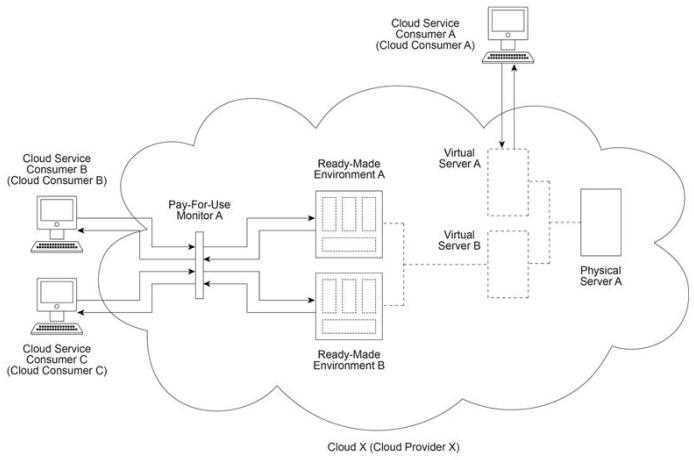
Cloud X (owned by Cloud Provider X) provides Physical Server A which hosts Virtual Servers A and B.
Virtual Server B hosts Ready-Made Environments A and B. Cloud Service Consumer A uses Virtual
Server A as part of an IaaS leasing agreement in which Cloud Consumer A is charged a fixed monthly
fee for unlimited access. Cloud Service Consumers B and C use Ready-Made Environments A and B
respectively as part of a PaaS leasing agreement based on per-minute usage fees. In both cases,
access is monitored via Pay-For-Use Monitor A, which keeps track of log-in and log-out times in order
to calculate the usage charges that are billed to Cloud Consumers B and C . Virtual Server A begins
generating a series of exceptions. Soon thereafter, Virtual Server B becomes destabilized, resulting in
further exceptions being raised in Ready-Made Environments A and B. Cloud Service Consumers B
and C receive a series of error messages until both of their connections are dropped Finally, Physical
Server A shuts down completely. A subsequent investigation reveals that Virtual Server A was the
victim of a security attack performed by a malicious cloud service consumer, the attacker generated
increased loads of external communication requests on Virtual Server A and the underlying network,
causing Physical Server A (along with Virtual Server B) to eventually shut down.
 Which of the following statements accurately identifies the type of security threat that corresponds
to the described attack - and -provides a solution that can directly mitigate this type of security
threat within Cloud X?
Which of the following statements accurately identifies the type of security threat that corresponds
to the described attack - and -provides a solution that can directly mitigate this type of security
threat within Cloud X?
 Which of the following statements accurately identifies the type of security threat that corresponds
to the described attack - and -provides a solution that can directly mitigate this type of security
threat within Cloud X?
Which of the following statements accurately identifies the type of security threat that corresponds
to the described attack - and -provides a solution that can directly mitigate this type of security
threat within Cloud X?Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.

