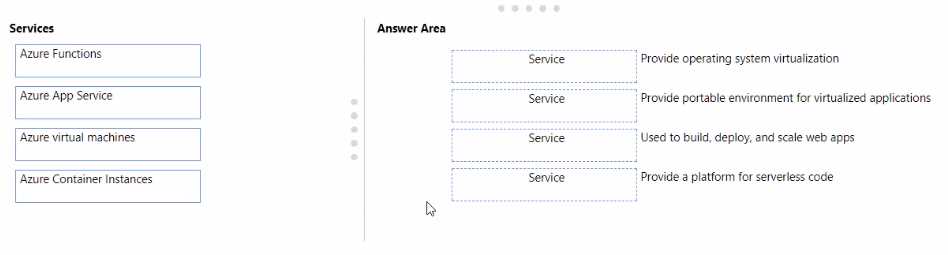
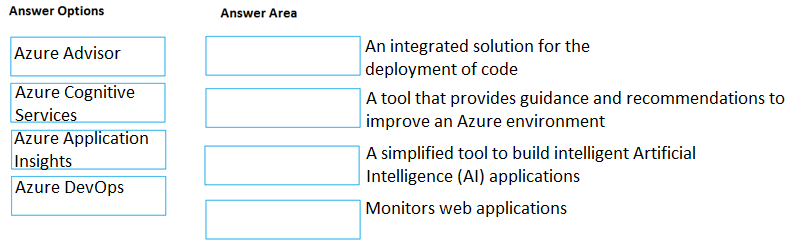
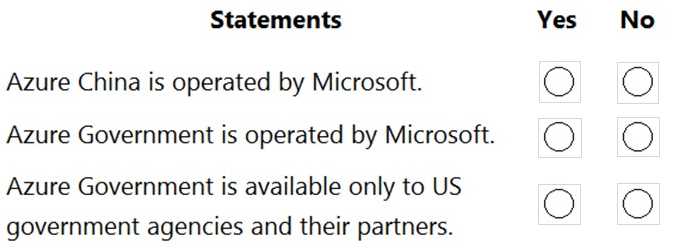
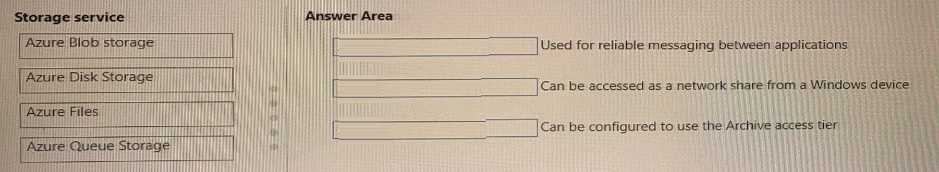
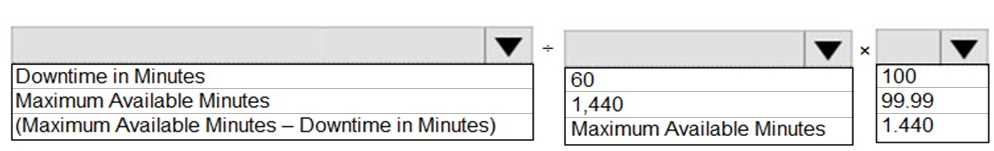
Microsoft Learn. (n.d.). What is defense in depth?. Microsoft Azure Documentation.
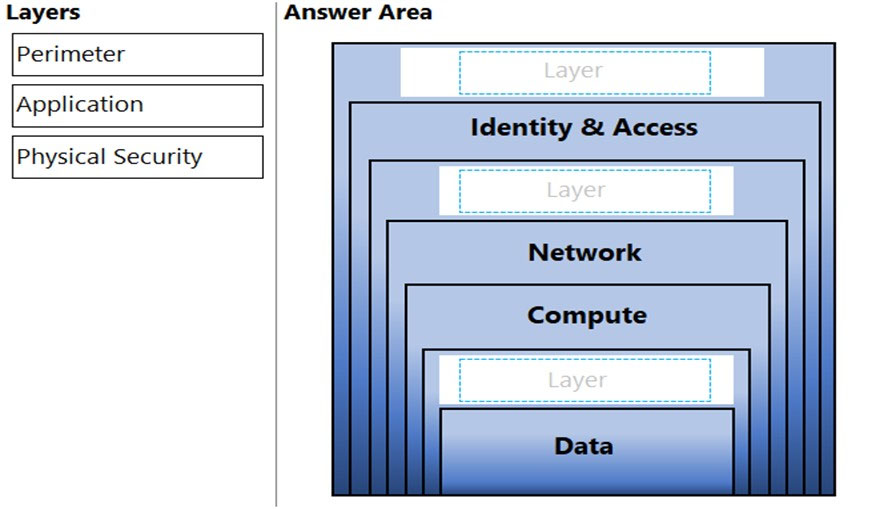
This document outlines the standard layered security model used by Microsoft. It explicitly details the order and purpose of each layer: "The layers are: physical security, identity and access, perimeter, network, compute, application, and data." This directly supports the placement of all three draggable layers in the provided diagram.
National Security Agency (NSA). (n.d.). Defense in Depth: A practical strategy for achieving Information Assurance in today's highly networked environments.
This foundational document (referenced in academic texts, e.g., Wikipedia "Defense in depth (computing)") establishes the "onion model" concept. It describes the layering of defenses, starting with Physical Security as a fundamental component, followed by network and host-level controls (like Perimeter and Compute), and finally protecting the Application and Data at the core.
National Institute of Standards and Technology (NIST). (n.d.). Glossary: Defense-in-Depth. Computer Security Resource Center (CSRC).
Document: NIST SP 800-53 Rev. 5, Security and Privacy Controls for Information Systems and Organizations.
Reference: This standard, along with the CSRC glossary, defines defense-in-depth as an "information security strategy integrating people, technology, and operations capabilities to establish variable barriers across multiple layers and dimensions of the organization." The layered model in the question is a direct visualization of implementing these variable barriers, which include physical, network (perimeter), and application controls as distinct layers.