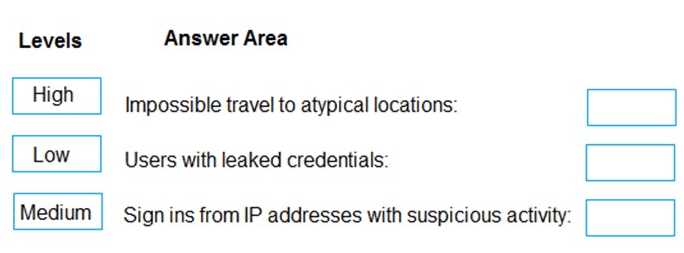
DRAG DROP You are implementing conditional access policies. You must evaluate the existing Azure Active Directory (Azure AD) risk events and risk levels to configure and implement the policies. You need to identify the risk level of the following risk events: Users with leaked credentials Impossible travel to atypical locations Sign ins from IP addresses with suspicious activity Which level should you identify for each risk event? To answer, drag the appropriate levels to the correct risk events. Each level may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Leaked creds are flagged as high risk because it's a confirmed compromise. Impossible travel and suspicious IPs tend to be medium since they can trigger on legit activity (like VPN or shared proxies). Pretty sure this matches what MS expects but open to other ideas if anyone's gotten different in practice.
I think the right mapping is: Impossible travel = Medium, Leaked credentials = High, Suspicious IP = Medium. Leaked creds are always High since that's a direct compromise, but impossible travel and suspicious IPs are usually only Medium. That Low option is a common trap here.