Pretty sure it should be C. To see if risk mitigation is really working, you have to look at whether the controls are actually cost-effective and reducing risk, not just if systems are documented (D is more about asset inventory). Seen similar questions in practice material. Anyone see an argument for B here?
Had something like this in a mock recently. The main goal of hardening is to securely configure devices to minimize vulnerabilities, so limiting the attack surface. Option A lines up with that. The others are more about detection or analysis after the fact, not prevention.
Option D might fit if the question was asking about incident response, but since it's about hardening, do they mean "best purpose" or just "one of the purposes"? That would change things here.
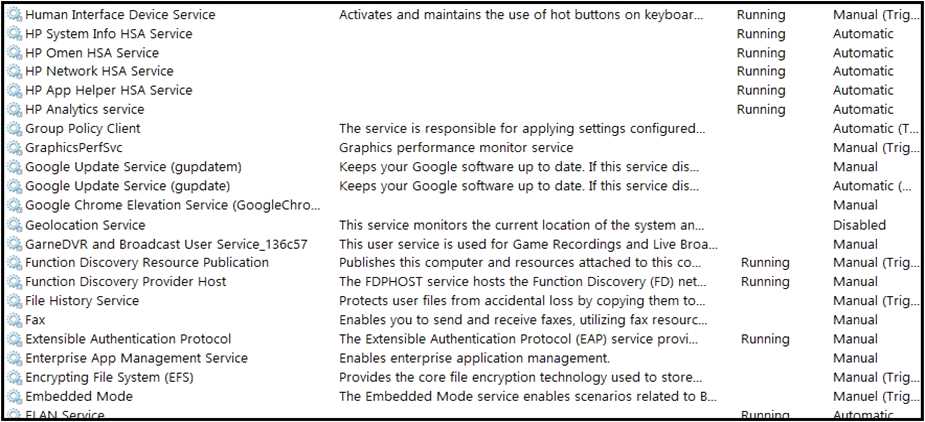 An engineer received multiple reports from employees unable to log into systems with the error: The
Group Policy Client service failed to logon – Access is denied. Through further analysis, the engineer
discovered several unexpected modifications to system settings. Which type of breach is occurring?
An engineer received multiple reports from employees unable to log into systems with the error: The
Group Policy Client service failed to logon – Access is denied. Through further analysis, the engineer
discovered several unexpected modifications to system settings. Which type of breach is occurring?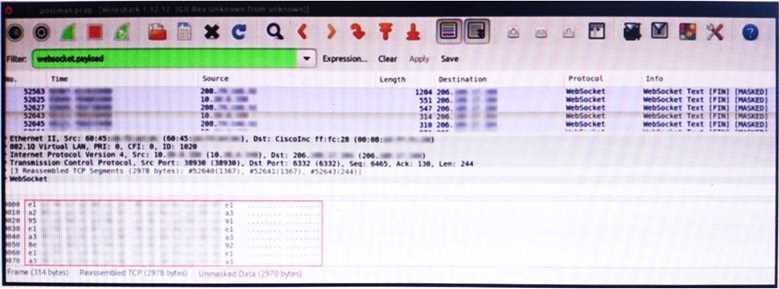 An engineer is analyzing this Vlan0386-int12-117.pcap file in Wireshark after detecting a suspicious
network activity. The origin header for the direct IP connections in the packets was initiated by a
google chrome extension on a WebSocket protocol. The engineer checked message payloads to
determine what information was being sent off-site but the payloads are obfuscated and unreadable.
What does this STIX indicate?
An engineer is analyzing this Vlan0386-int12-117.pcap file in Wireshark after detecting a suspicious
network activity. The origin header for the direct IP connections in the packets was initiated by a
google chrome extension on a WebSocket protocol. The engineer checked message payloads to
determine what information was being sent off-site but the payloads are obfuscated and unreadable.
What does this STIX indicate?D imo makes sense if the focus was on fixing payments quickly, but since it's asking what to do first, A fits better because you need to figure out what happened before jumping to manual fixes. Is there a specific company policy that prioritizes incident escalation over initial investigation?
Shouldn't we check with the SaaS tool team first to figure out what went wrong before escalating? Jumping to B seems like an easy trap here, since you don’t know the scope or if it’s a breach yet.

