Q: 7
Refer to the exhibit.
 An engineer is analyzing this Vlan0386-int12-117.pcap file in Wireshark after detecting a suspicious
network activity. The origin header for the direct IP connections in the packets was initiated by a
google chrome extension on a WebSocket protocol. The engineer checked message payloads to
determine what information was being sent off-site but the payloads are obfuscated and unreadable.
What does this STIX indicate?
An engineer is analyzing this Vlan0386-int12-117.pcap file in Wireshark after detecting a suspicious
network activity. The origin header for the direct IP connections in the packets was initiated by a
google chrome extension on a WebSocket protocol. The engineer checked message payloads to
determine what information was being sent off-site but the payloads are obfuscated and unreadable.
What does this STIX indicate?
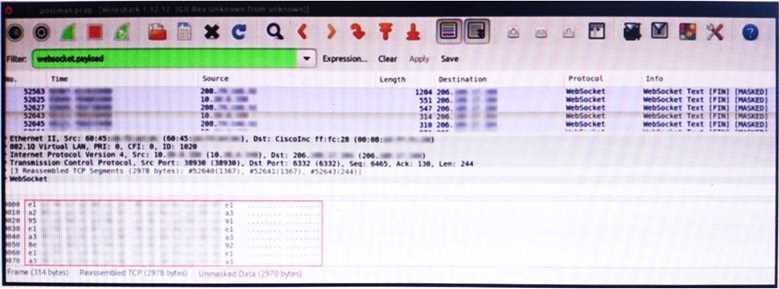 An engineer is analyzing this Vlan0386-int12-117.pcap file in Wireshark after detecting a suspicious
network activity. The origin header for the direct IP connections in the packets was initiated by a
google chrome extension on a WebSocket protocol. The engineer checked message payloads to
determine what information was being sent off-site but the payloads are obfuscated and unreadable.
What does this STIX indicate?
An engineer is analyzing this Vlan0386-int12-117.pcap file in Wireshark after detecting a suspicious
network activity. The origin header for the direct IP connections in the packets was initiated by a
google chrome extension on a WebSocket protocol. The engineer checked message payloads to
determine what information was being sent off-site but the payloads are obfuscated and unreadable.
What does this STIX indicate?Options
Discussion
C. not D. Malware is tempting but the clue is about obfuscated payloads that aren’t UTF-8, which can mean data leak via odd encoding. Similar exam questions tend to push toward C here.
D doesn’t fit, C . Official guides and Wireshark labs both mention encoded payloads as red flags for exfil.
I think D. If the payloads are obfuscated and using non-standard encoding over WebSockets, could be malware talking to C2. I know C is possible but encrypted channels are classic for exfil. Not totally sure though, open to other ideas.
Probably C. Exam reports often point to encoded payloads being a sign of possible data exfiltration, especially when you can't immediately read the content and it's not in expected formats like UTF-8. Official study guides and Wireshark lab practice both call this out as suspect. Pretty sure on this-disagree if you've seen different documentation.
Be respectful. No spam.

