I don’t think it’s D, that’s more about malware control. C is the one tied to strong access controls since assigning unique IDs is all about tracking who can get into systems. Saw similar wording in practice, B is tempting but that’s encryption, not access control. Let me know if you see it another way.
PCI DSS always splits up controls in oddly specific ways, it's confusing sometimes. Definitely C for this one, since giving everyone a unique ID is all about tracking and managing who gets access to what (least privilege, accountability, the usual). The rest are important but don't fit "strong access control" like C does. Pretty sure that's correct, let me know if you see it differently.
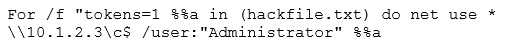 What is Eve trying to do?
What is Eve trying to do?I get why some might lean toward D since classes.dex is important at runtime, but config-wise it's A. AndroidManifest.xml defines the structure and what services, activities, etc. the app exposes. Maybe not 100% clear from just "configuration" in the question, but I've seen similar practice sets always pick A for this type. Open to pushback if anyone thinks otherwise.
ls -d), that's how you'd trigger an AXFR zone transfer in nslookup after connecting to the DNS server. A looks like a distractor. Pretty sure B is what CEH wants here.Leaning B since it's close to actual ls -d, but D looks tempting if you think they're after something zone specific. These CEH questions can be tricky with typos.
server 192.168.10.2? That would matter here.ls -d abccorp.local). Even with the typo, it's clear what they're testing for. Not 100% perfect syntax but definitely closest here.Isn’t the trap here that higher MX numbers are actually lower priority? I see why some would pick True, but DNS goes for the lowest number first. Feels like they’re testing if you know MX preference values work opposite to what you’d expect.
Nice and clear wording on this one. False
What if the mail system has custom logic or a failover config that ignores MX priority? In standard DNS lower numbers win, but I’ve seen environments where admins manually override the defaults. Would that flip how this works?
A . Don't think C is right here, AT&T IoT Platform is more for device management not scanning for default creds. The scenario calls out automated discovery and credential checking, which lines up exactly with what IoTSeeker does. Easy to get tripped up by the big vendor names, but in this context A makes the most sense.
Nice clear subnetting question. C fits the last 100 usable in that /23, as it's within the upper part of 10.1.4.0-10.1.5.255. I think that's right but if anyone sees another angle let me know.

