Q: 11
Centralized binary logging is a process in which many websites write binary and unformatted log
data to a single log file. What extension should the investigator look to find its log file?
Options
Discussion
C vs B, but pretty sure it's C because .ibl is specific for binary log files in centralized setups.
Be respectful. No spam.
Q: 12
When performing a forensics analysis, what device is used to prevent the system from recording data
on an evidence disk?
Options
Discussion
A imo, since a write-blocker is standard practice in forensics. It stops anything from changing evidence disks during analysis which keeps it admissible. The other options don’t actually prevent writes. Pretty sure about this, but open if someone has seen otherwise.
Option D seen similar phrasing on official practice but lab guides might help clarify.
Be respectful. No spam.
Q: 13
Where should the investigator look for the Edge browser’s browsing records, including history, cache,
and cookies?
Options
Discussion
Its A, ESE Database. Official guide and some lab exercises point to WebCacheV01.dat for Edge history and cache.
Call it it's A (ESE Database). That's where Edge keeps things like history and cookies in the WebCacheV01.dat file. Saw similar questions on practice exams. Anyone think they use B or C for anything browser related?
Be respectful. No spam.
Q: 14
What is the capacity of Recycle bin in a system running on Windows Vista?
Options
Discussion
Definitely D. That's the default 10% per partition in Vista, not unlimited.
D imo, since Vista uses 10% of the partition by default unless you manually set something else.
Be respectful. No spam.
Q: 15
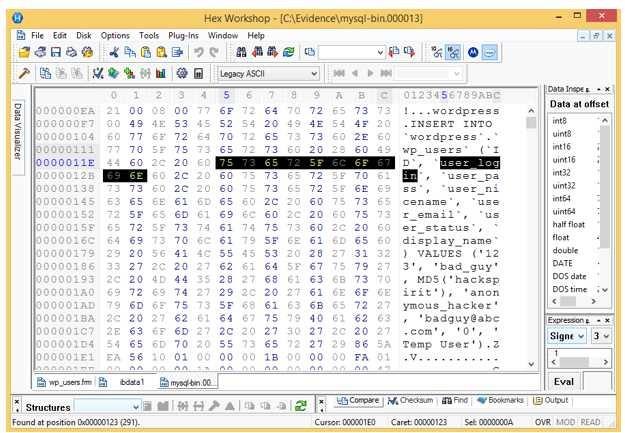
Analyze the hex representation of mysql-bin.000013 file in the screenshot below. Which of the
following will be an inference from this analysis?

Options
Discussion
Option D had something just like this in a mock exam. INSERT with 'bad_guy' really only fits new user creation.
D , but only because the hex dump actually shows an INSERT INTO statement with 'bad_guy' as the userlogin. If it were UPDATE or REPLACE instead of INSERT, then one of the other options might fit. Seen a similar trick on exam practice questions.
Call it it's D. The hex shows an INSERT for 'bad_guy' which matches new WP user creation.
D imo, since it's clear from similar practice that the insert statement is adding 'bad_guy' as a user. Official guide and reviewing lab hex dumps really help with these.
Be respectful. No spam.
Q: 16
Select the tool appropriate for finding the dynamically linked lists of an application or malware.
Options
Discussion
Nope, for finding DLL dependencies you'd pick D here. PEiD is more about packers and signatures.
D for sure.
Its C
Not C, D is right here. Seen similar on practice tests and official guide says Dependency Walker for DLL lists.
Be respectful. No spam.
Q: 17
To check for POP3 traffic using Ethereal, what port should an investigator search by?
Options
Discussion
Its D
Be respectful. No spam.
Q: 18
John is working on his company policies and guidelines. The section he is currently working on covers
company documents; how they should be handled, stored, and eventually destroyed. John is
concerned about the process whereby outdated documents are destroyed. What type of shredder
should John write in the guidelines to be used when destroying documents?
Options
Discussion
Pretty sure it's B. Cross-cut gives better security than strip-cut. I'm not completely confident though, can someone confirm?
Be respectful. No spam.
Q: 19
If you discover a criminal act while investigating a corporate policy abuse, it becomes a publicsector
investigation and should be referred to law enforcement?
Options
Discussion
Hard to say, False. Seen similar questions pop up in the official guide and some practice exams.
Be respectful. No spam.
Q: 20
Rule 1002 of Federal Rules of Evidence (US) talks about
Options
Discussion
Always see Rule 1002 linked with the 'requirement of original' in both exam prep and the official FRE guide. C
C fits here, it's the 'requirement of original' stated in Rule 1002. Seen this pop up often in practice sets and official study guides. Let me know if you found a trick in the question, but pretty sure it's C.
Probably C since Rule 1002 is the actual 'requirement of original' or Best Evidence Rule. It says you need to produce the original record in court unless there's an exception. Pretty sure that's right, correct me if I'm off.
Be respectful. No spam.
Question 11 of 20 · Page 2 / 2

