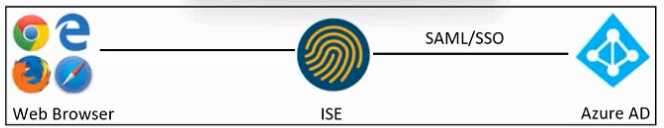
 Refer to the exhibit. An engineer must configure SAML SSO in Cisco ISE to use Microsoft Azure AD as
an identity provider. These configurations were performed:
Configure a SAML IdP in ISE.
Configure the Azure AD IdP settings.
Which two actions must the engineer take in Cisco ISE? (Choose two.)
Refer to the exhibit. An engineer must configure SAML SSO in Cisco ISE to use Microsoft Azure AD as
an identity provider. These configurations were performed:
Configure a SAML IdP in ISE.
Configure the Azure AD IdP settings.
Which two actions must the engineer take in Cisco ISE? (Choose two.)Q: 1
Refer to the exhibit.
 Refer to the exhibit. An engineer must configure SAML SSO in Cisco ISE to use Microsoft Azure AD as
an identity provider. These configurations were performed:
Configure a SAML IdP in ISE.
Configure the Azure AD IdP settings.
Which two actions must the engineer take in Cisco ISE? (Choose two.)
Refer to the exhibit. An engineer must configure SAML SSO in Cisco ISE to use Microsoft Azure AD as
an identity provider. These configurations were performed:
Configure a SAML IdP in ISE.
Configure the Azure AD IdP settings.
Which two actions must the engineer take in Cisco ISE? (Choose two.)
 Refer to the exhibit. An engineer must configure SAML SSO in Cisco ISE to use Microsoft Azure AD as
an identity provider. These configurations were performed:
Configure a SAML IdP in ISE.
Configure the Azure AD IdP settings.
Which two actions must the engineer take in Cisco ISE? (Choose two.)
Refer to the exhibit. An engineer must configure SAML SSO in Cisco ISE to use Microsoft Azure AD as
an identity provider. These configurations were performed:
Configure a SAML IdP in ISE.
Configure the Azure AD IdP settings.
Which two actions must the engineer take in Cisco ISE? (Choose two.)Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 2
According to Cisco Security Reference Architecture, which solution provides threat intelligence and
malware analytics?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 3
A recent InfraGard news release indicates the need to establish a risk ranking for all on-premises and
cloud services. The ACME Corporation already performs risk assessments for on-premises services
and has applied a risk ranking to them. However, the cloud services that were used lack risk rankings.
What Cisco Umbrella function should be used to meet the requirement?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 4
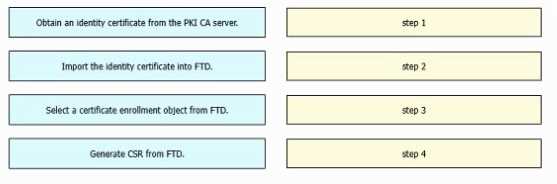
DRAG DROP
An engineer must configure certificate-based authentication in a cloud-delivered Cisco Secure
Firewall Management Center. Drag and drop the steps from left to right to manually enroll
certificates on a Cisco Secure Firewall Threat Defense Virtual device.

Your Answer
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 5
Which types of algorithm does a web application firewall use for zero-day DDoS protection?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 6
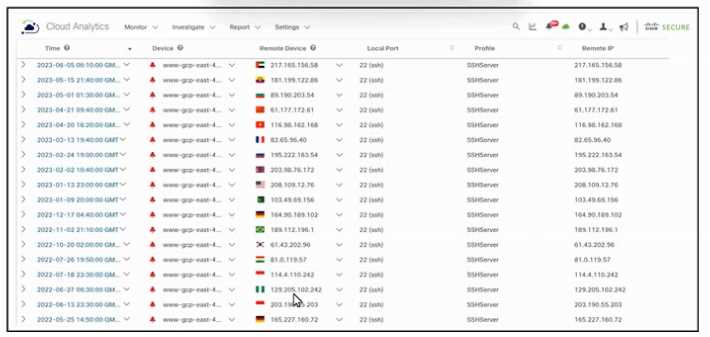
Refer to the exhibit.
 Refer to the exhibit. An engineer must analyze the Cisco Secure Cloud Analytics report. What is
occurring?
Refer to the exhibit. An engineer must analyze the Cisco Secure Cloud Analytics report. What is
occurring?
 Refer to the exhibit. An engineer must analyze the Cisco Secure Cloud Analytics report. What is
occurring?
Refer to the exhibit. An engineer must analyze the Cisco Secure Cloud Analytics report. What is
occurring?Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 7
An engineer is configuring multifactor authentication using Duo. The implementation must use Duo
Authentication Proxy and the Active Directory as an identity source. The company uses Azure and a
local Active Directory. Which configuration is needed to meet the requirement?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 8
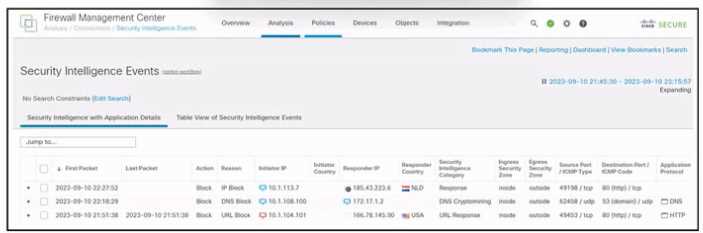
Refer to the exhibit.
 Refer to the exhibit. An engineer is analyzing a Cisco Secure Firewall Management Center report.
Which activity does the output verify?
Refer to the exhibit. An engineer is analyzing a Cisco Secure Firewall Management Center report.
Which activity does the output verify?
 Refer to the exhibit. An engineer is analyzing a Cisco Secure Firewall Management Center report.
Which activity does the output verify?
Refer to the exhibit. An engineer is analyzing a Cisco Secure Firewall Management Center report.
Which activity does the output verify?Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 9
Refer to the exhibit.
 Refer to the exhibit. An engineer must troubleshoot an incident by using Cisco Secure Cloud
Analytics. What is the cause of the issue?
Refer to the exhibit. An engineer must troubleshoot an incident by using Cisco Secure Cloud
Analytics. What is the cause of the issue?
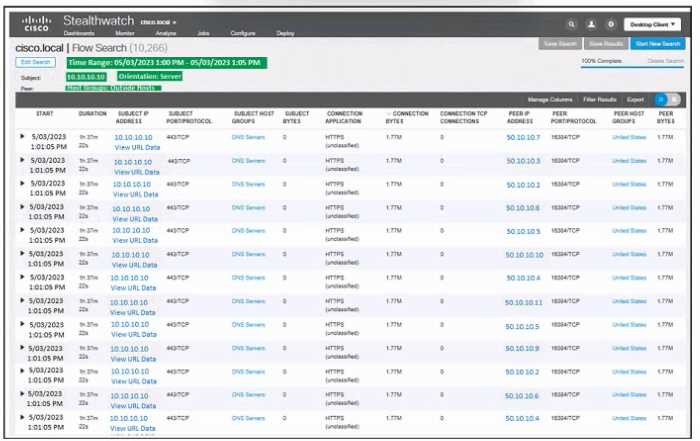 Refer to the exhibit. An engineer must troubleshoot an incident by using Cisco Secure Cloud
Analytics. What is the cause of the issue?
Refer to the exhibit. An engineer must troubleshoot an incident by using Cisco Secure Cloud
Analytics. What is the cause of the issue?Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 10
Refer to the exhibit.
 Refer to the exhibit. An engineer must create a policy in Cisco Secure Firewall Management Center to
prevent restricted users from being able to browse any business or mobile phone shopping websites.
The indicated policy was applied; however, the restricted users still can browse on the mobile phone
shopping websites during business hours. What should be done to meet the requirement?
Refer to the exhibit. An engineer must create a policy in Cisco Secure Firewall Management Center to
prevent restricted users from being able to browse any business or mobile phone shopping websites.
The indicated policy was applied; however, the restricted users still can browse on the mobile phone
shopping websites during business hours. What should be done to meet the requirement?
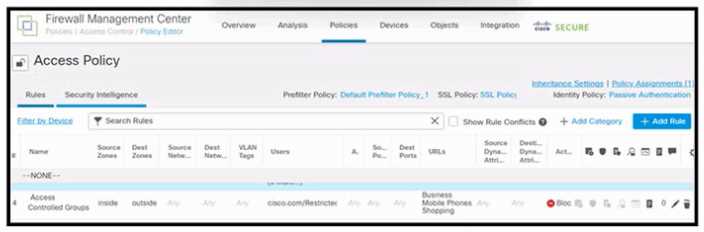 Refer to the exhibit. An engineer must create a policy in Cisco Secure Firewall Management Center to
prevent restricted users from being able to browse any business or mobile phone shopping websites.
The indicated policy was applied; however, the restricted users still can browse on the mobile phone
shopping websites during business hours. What should be done to meet the requirement?
Refer to the exhibit. An engineer must create a policy in Cisco Secure Firewall Management Center to
prevent restricted users from being able to browse any business or mobile phone shopping websites.
The indicated policy was applied; however, the restricted users still can browse on the mobile phone
shopping websites during business hours. What should be done to meet the requirement?Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 1 of 20 · Page 1 / 2

