Q: 1
Which information in the HTTP request is used to determine if it is subject to the referrer exceptions
feature in the Cisco WSA?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 2
Which IP address and port are used by default to run the system setup wizard?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 3
Which statement about identification profile default settings on the Cisco WSA is true?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
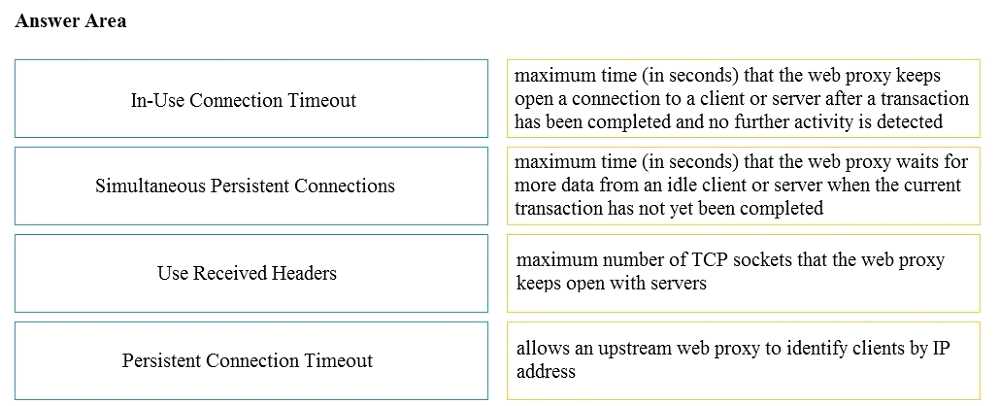
Q: 4
DRAG DROP Drag and drop the properties from the left onto the correct advanced web proxy setting descriptions on the right.
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 5
Which two configuration options are available on a Cisco WSA within a decryption policy? (Choose
two.)
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 6
A network administrator noticed that all traffic that is redirected to the Cisco WSA from the Cisco
ASA firewall cannot get to the Internet in a Transparent proxy environment using WCCP.
Which troubleshooting action must be taken on the CLI to make sure that WCCP communication is
not failing?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 7
Which two configuration options can be configured when invalid certificates are processed with the
HTTPS proxy on WSA enabled? (Choose two.)
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
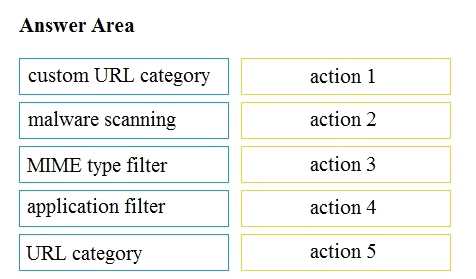
Q: 8
DRAG DROP Drag and drop the Cisco WSA access policy elements from the left into the order in which they are processed on the right.
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 9
What is a benefit of integrating Cisco Cognitive Threat Analytics with a Cisco WSA?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 1 of 20 · Page 1 / 2