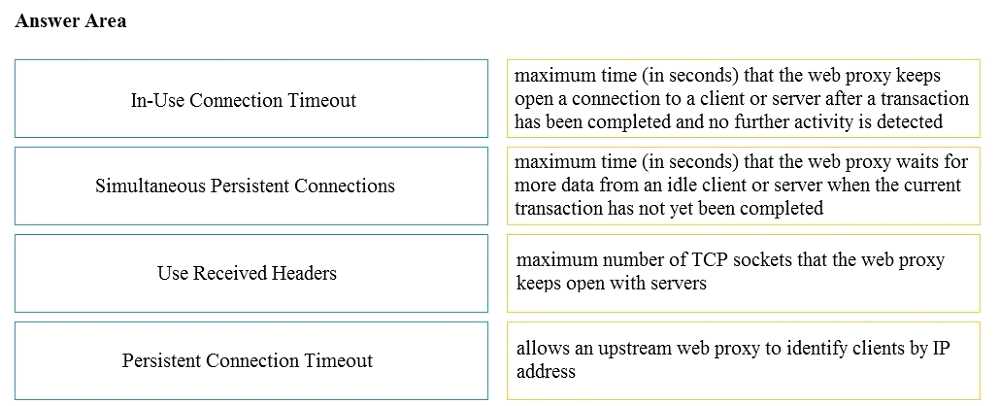
DRAG DROP Drag and drop the properties from the left onto the correct advanced web proxy setting descriptions on the right.
📖 About this Domain
This domain covers configuring Cisco WSA to enforce granular access control through Identification Profiles and Access Policies. It focuses on differentiating user traffic for customized web security based on identity and group membership from sources like Active Directory.
🎓 What You Will Learn
- Configure Identification Profiles to map users to policies using methods like IP surrogates or authentication integration.
- Build Access Policies that apply specific rules, such as URL filtering or malware scanning, to different identified user groups.
- Integrate the WSA with authentication realms like NTLM or Kerberos for transparent user identification.
- Organize users into policy groups to apply differentiated access rules and reporting.
🛠️ Skills You Will Build
- Implement user-based policies by configuring WSA policies enforced on specific users or Active Directory groups.
- Troubleshoot authentication and identification failures for users connecting through the WSA.
- Design and implement complex access policies that differentiate traffic for various departments or user roles.
- Configure transparent authentication mechanisms to identify users without requiring manual login prompts.
💡 Top Tips to Prepare
- Master the configuration and troubleshooting of NTLM, Kerberos, and LDAP authentication realms on the WSA.
- Practice creating multiple policy groups and understand the order of precedence for Access Policy application.
- Know the different methods for identifying users, such as by IP address or authentication, and when to use each.
- Utilize both the WSA GUI and CLI to configure and verify Identification Profiles and Access Policies.
📖 About this Domain
The Configuration domain covers the hands-on implementation of Cisco Web Security Appliance (WSA) and Email Security Appliance (ESA). It focuses on deploying proxy services, defining security policies, and configuring authentication and integrations.
🎓 What You Will Learn
- You will learn to configure Cisco WSA proxy modes, including explicit and transparent, to intercept and manage web traffic.
- You will learn to implement security policies for HTTPS decryption, access control, and acceptable use on the WSA.
- You will learn to configure mail, file, and data security policies on the Cisco ESA to mitigate email-based threats.
- You will learn to integrate authentication services using SAML and connect to third-party security services via ICAP.
🛠️ Skills You Will Build
- You will build the skill to deploy and troubleshoot various WSA proxy configurations in a live network environment.
- You will build the skill to create and verify granular access policies, decryption policies, and end-user notifications.
- You will build the skill to configure robust mail policies on the ESA, including anti-spam, anti-virus, and outbreak filters.
- You will build the skill to implement data security and SaaS access controls on both WSA and ESA platforms.
💡 Top Tips to Prepare
- Gain practical experience with the WSA and ESA administrative interfaces, focusing on policy creation and proxy settings.
- Master the configuration and verification of HTTPS decryption, including certificate management and policy application.
- Understand the traffic flow and policy engine logic for both transparent and explicit proxy deployments.
- Practice configuring authentication methods, especially SAML, and understand how identity is used in policy enforcement.
📖 About this Domain
This domain covers the configuration of core proxy functions on the Cisco Secure Web Appliance (WSA). It emphasizes the creation and application of policies that control user access, inspect encrypted traffic, and enforce security controls.
🎓 What You Will Learn
- You will learn to configure authentication realms and identity-based access policies for granular user control.
- You will learn to implement decryption policies to enable inspection of HTTPS traffic for malware and policy violations.
- You will learn to enforce acceptable use policies (AUP) and data security policies to mitigate risk and prevent data loss.
- You will learn to create routing policies to manage traffic flow, including upstream proxy configurations and PAC files.
🛠️ Skills You Will Build
- You will build the skill to integrate the WSA with Active Directory for transparent user authentication using NTLM or Kerberos.
- You will build the skill to deploy and troubleshoot HTTPS decryption, including certificate management and handling certificate pinning.
- You will build the skill to configure Data Loss Prevention (DLP) policies to block sensitive data uploads.
- You will build the skill to construct complex policy groups that combine multiple policy types for specific user sets.
💡 Top Tips to Prepare
- Master the policy trace tool to troubleshoot how different policies are applied to specific web requests.
- Practice configuring both explicit forward and transparent proxy modes to understand their operational differences.
- Understand the flow of policy evaluation on the WSA, including the order of precedence for identity, access, and decryption policies.
- Focus on the configuration of custom URL categories and their use within access and decryption policies.
📖 About this Domain
This domain covers Cisco WSA decryption policies for inspecting encrypted web traffic. You will learn to configure policies to decrypt, bypass, or drop SSL/TLS sessions based on defined criteria.
🎓 What You Will Learn
- Configure WSA decryption policies to intercept and inspect HTTPS traffic for threats.
- Implement policy rules to bypass decryption for sensitive traffic categories like financial services.
- Create policies to drop encrypted traffic that uses untrusted certificates or weak ciphers.
- Understand the role of certificate authorities and certificate validation in the decryption process.
🛠️ Skills You Will Build
- Proficiency in configuring SSL/TLS decryption, bypass, and drop rules on the Cisco WSA.
- Ability to troubleshoot decryption failures using policy trace and access logs.
- Competence in managing certificate trust lists and custom URL categories for granular policy control.
- Skill in integrating decryption policies with identity services and access policies for user-based enforcement.
💡 Top Tips to Prepare
- Gain hands-on experience with the WSA GUI to build and test decryption policy groups and rules.
- Master the WSA policy engine's order of operations, specifically how decryption policies interact with access policies.
- Study the different certificate validation methods like OCSP and CRL and their configuration within the WSA.
- Practice interpreting access log entries related to decrypted, bypassed, and dropped HTTPS transactions.
📖 About this Domain
This domain covers the core functionalities of the Cisco Web Security Appliance (WSA), focusing on its role as a forward proxy. You will explore the implementation of features for web threat defense, advanced malware protection, and granular policy control.
🎓 What You Will Learn
- Understand WSA deployment options, including explicit forward proxy and transparent proxy modes using WCCP.
- Learn to configure HTTPS traffic inspection using decryption policies, certificate management, and SSL/TLS settings.
- Master the creation of access policies, identities, and URL filtering to enforce acceptable use and security controls.
- Explore the integration of Advanced Malware Protection (AMP) and Threat Grid for dynamic threat analysis and file reputation.
🛠️ Skills You Will Build
- Configure and manage core WSA services like the web proxy, authentication realms, and PAC files.
- Implement granular access and decryption policies based on user identity, URL categories, and application visibility.
- Troubleshoot web traffic flows through the WSA using access logs, reporting, and diagnostic tools.
- Integrate WSA with external security components like Cisco AMP and Threat Grid to enhance malware detection.
💡 Top Tips to Prepare
- Review the official Cisco WSA AsyncOS Configuration Guides for detailed feature implementation steps.
- Utilize Cisco dCloud labs to gain hands-on experience with WSA policy configuration and deployment scenarios.
- Memorize the processing order for access policies, decryption policies, and routing policies as this is a critical concept.
- Understand the data flow and configuration for integrating WSA with Cisco AMP and Threat Grid for file analysis.
📖 About this Domain
This domain covers the configuration of Cisco WSA policies to enforce corporate acceptable use guidelines. It focuses on controlling user access to web content, applications, and file types through Access Policies and Identification Profiles. The core objective is to manage web traffic based on defined rules to mitigate security risks.
🎓 What You Will Learn
- You will learn to configure Access Policies to control web access based on URL categories, time of day, and user identity.
- You will learn to implement Application Visibility and Control (AVC) to identify and manage specific web applications and services.
- You will learn to create policies for controlling file downloads and uploads by type, size, and malware scanning results.
- You will learn to integrate the WSA with authentication realms like LDAP or NTLM to apply granular, user-based acceptable use policies.
🛠️ Skills You Will Build
- You will build the skill to construct and manage complex Access Policy groups for different user sets.
- You will build proficiency in configuring URL filtering using both predefined and custom URL categories to enforce web usage rules.
- You will build the ability to configure and tune AVC policies to block or throttle non-compliant application traffic.
- You will build expertise in creating and applying Decryption Policies for HTTPS inspection, which is critical for effective acceptable use control.
💡 Top Tips to Prepare
- Master the interaction between Identification Profiles and Access Policies as this is fundamental to applying user-specific rules.
- Practice configuring AVC to block common social media and streaming applications in a lab environment.
- Understand the processing order of policies, as the first matched policy is the one that is enforced on the traffic.
- Focus on how Decryption Policies enable visibility into encrypted traffic, which is essential for modern AVC and URL filtering.
Premium Access Includes
- ✓ Quiz Simulator
- ✓ Exam Mode
- ✓ Progress Tracking
- ✓ Question Saving
- ✓ Flash Cards
- ✓ Drag & Drops
- ✓ 3 Months Access
- ✓ PDF Downloads