Q: 11
For security purposes, an engineer enables CPU ACL and chooses an ACL on the Security > Access
Control Lists > CPU Access Control Lists menu. Which kind of traffic does this change apply to as soon
as the change is made?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 12
When implementing self-registration for guest/BYOD devices, what happens when an employee tries
to connect four devices to the network at the same time?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 13
A wireless engineer is configuring LWA using ISE. The customer is a startup company and requested
the wireless users to authenticate against a directory, but LDAP is unavailable. Which solution should
be proposed in order to have the same security and user experience?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 14
A wireless administrator must assess the different client types connected to Cisco Catalyst 9800
Series Wireless Controller without using any external servers. Which configuration must be added to
the controller to achieve this assessment?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 15
A customer wants the APs in the CEO’s office to have different usernames and passwords for
administrative support than the other APs deployed throughout the facility. Which feature must be
enabled on the WLC and APs to achieve this goal?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 16
DRAG DROP A wireless engineer wants to schedule monthly security reports in Cisco Prime infrastructure. Drag and drop the report the from the left onto the expected results when the report is generated on the right.
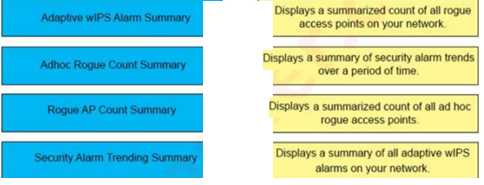
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 17
DRAG DROP The network management team in a large shopping center has detected numerous rogue APs from local coffee shops that are broadcasting SSIDs. All of these SSIDs have names starting with ATC (for example, ATC302, ATC011, and ATC566). A wireless network engineer must appropriately classify these SSIDs using the Rogue Rules feature. Drag and drop the options from the left onto the categories in which they must be used on the right. Not all options are used.
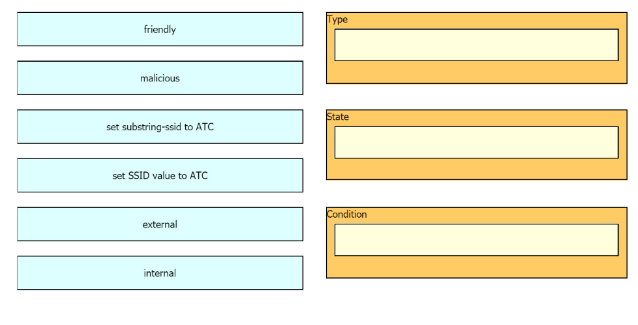
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 18
Refer to the exhibit. Which two items must be supported on the VoWLAN phones to take full
advantage of this WLAN configuration? (Choose two.)
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 19
An engineer is configuring a BYOD deploymernt strategy and prefers a single SSID model.
Which technology is required to accomplish this configuration?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 11 of 20 · Page 2 / 2

