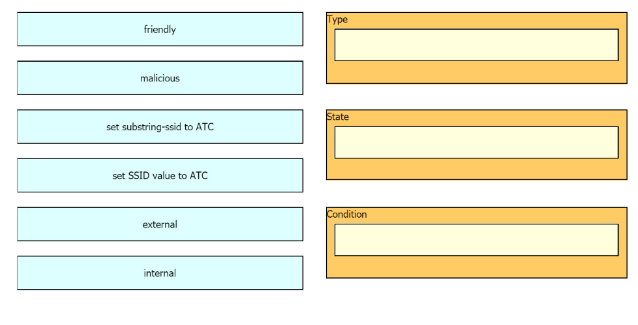
Cisco Systems, Inc. (2024). Cisco Catalyst 9800 Series Wireless Controller Configuration Guide, Cisco IOS XE Cupertino 17.14.x - Rogue Management. In the context of rogue management, Cisco Wireless Controllers allow for the creation of rules to automatically classify rogue APs. A rule condition can be based on the SSID. The classification state for a rogue can be set to 'Friendly', and its status can be defined as 'External' if it is not on the local wired network.
Reference: Section "Configure Rogue Rules". This documentation details creating rules based on conditions like SSID match to set a rogue's classification to "Friendly" and state to "External".
Hucaby, D. (2014). CCNP Wireless IUWVN 642-732 Official Cert Guide. Cisco Press.
Reference: Chapter 14, "Implement Cisco Unified Wireless Security," section "Rogue APs." The text explains that rogue APs can be classified as friendly if they are known and determined not to be a threat. Rules can be configured on a Wireless LAN Controller (WLC) to match specific criteria, such as SSIDs of neighboring wireless networks, and automatically assign them a "Friendly" classification. It also distinguishes between internal rogues (connected to the enterprise network) and external rogues (not connected).
Gass, S., & Pellen, R. M. (2007). Implementing a Wireless Intrusion Prevention System. IEEE Security & Privacy, 5(3), 74-77.
Reference: Page 75, section "Rogue-AP Detection and Mitigation." The paper discusses that a key function of a Wireless Intrusion Prevention System (WIPS) is to classify detected APs. It states, "A WIPS should let administrators classify APs as authorized, rogue, or external (neighboring)." The rules for this classification can be based on various parameters, including the SSID. This aligns with setting the State to external and Type to friendly (a synonym for an acknowledged neighbor).
DOI: 10.1109/MSP.2007.64