The metadata in the exhibit reveals a strong indicator that this .LNK file (shortcut) is malicious:
The shortcut file is named "ds7002.pdf" but actually points to the execution of PowerShell:
→ Full path: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
Arguments include:
→ -noni -ep bypass $z = '...'; indicating an attempt to run a PowerShell script with execution policy
bypassed (a known tactic for fileless malware delivery).
The file is masked as a PDF (common social engineering technique), and PowerShell execution via
.LNK is a signature technique used by many malware families to initiate second-stage payloads or
scripts.
Given this, the correct and safest course of action is to:
→ Open the .LNK file in a sandbox environment (D).
This enables safe behavioral analysis to observe what actions it attempts upon execution without
endangering live systems.
Other options are inappropriate:
A (ignoring the threat due to extension) is dangerous — .LNKs can trigger code.
B (upload to virus engine) is only helpful for known malware and lacks behavioral context.
C (quarantine) is preventive but not investigative — sandboxing provides visibility.
Reference: CyberOps Technologies (CBRFIR) 300-215 study guide, Chapter on “Threat Hunting and
Malware Analysis,” section covering shortcut (.LNK) based attacks, PowerShell-based threats, and
sandbox behavioral analysis strategies.
 An engineer is analyzing a .LNK (shortcut) file recently received as an email attachment and blocked
by email security as suspicious. What is the next step an engineer should take?
An engineer is analyzing a .LNK (shortcut) file recently received as an email attachment and blocked
by email security as suspicious. What is the next step an engineer should take?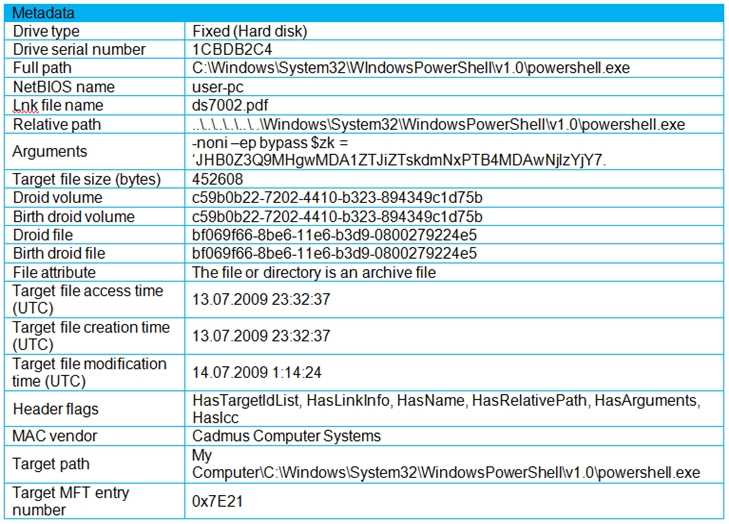 An engineer is analyzing a .LNK (shortcut) file recently received as an email attachment and blocked
by email security as suspicious. What is the next step an engineer should take?
An engineer is analyzing a .LNK (shortcut) file recently received as an email attachment and blocked
by email security as suspicious. What is the next step an engineer should take?
