Q: 1
Refer to the exhibit.
 A security analyst notices unusual connections while monitoring traffic. What is the attack vector,
and which action should be taken to prevent this type of event?
A security analyst notices unusual connections while monitoring traffic. What is the attack vector,
and which action should be taken to prevent this type of event?
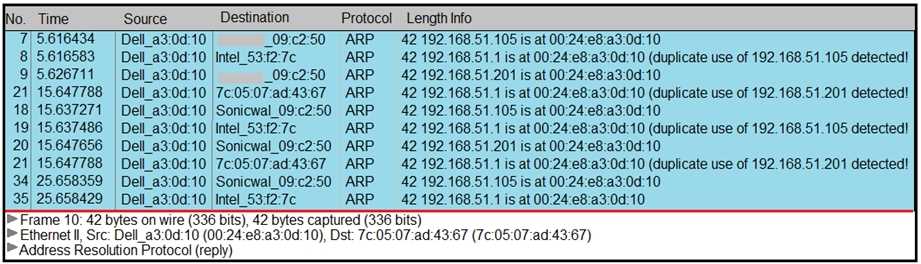 A security analyst notices unusual connections while monitoring traffic. What is the attack vector,
and which action should be taken to prevent this type of event?
A security analyst notices unusual connections while monitoring traffic. What is the attack vector,
and which action should be taken to prevent this type of event?Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.

