I don't think it's D. Investigating hosts in SIEM logs is classic detection and analysis (A), not containment, which comes after. Trap is thinking you'd go right to action just by reviewing logs-logs are for figuring out what's happening.
Full packet capture (D) eats up way more storage than the others. You're saving every single bit for all packets, not just summaries or metadata. Unless you're doing something weird with retention, D is the clear storage hog here. Pretty sure that's what Cisco aims for on this kind of question-someone correct me if I'm off.
Option C is the one here. Application-level whitelisting only lets pre-approved apps execute, while B (host-based IPS) generally catches known threats but doesn't default-deny by app name. I see why B trips people up, but it's not actually a whitelist. Makes sense?
C vs B-have seen similar questions in practice where some argue host-based IPS can restrict apps, but only C (application-level whitelisting) strictly allows execution of pre-approved software. B can block bad behavior but isn't always default-deny. Pretty sure C is what they want unless they're focusing on device rules, not just app list control. Someone disagree?
Encryption (D) is what actually prevents easy inspection, since it scrambles payload data so you can't just capture and read it. Stuff like SSL interception (A) is a workaround, not the blocker. I think D is right for what the question asks, but open if anyone sees it differently.
Had something like this in a mock, D fits best. The encryption in HTTPS is what blocks you from seeing the actual content of packets unless you do SSL decryption. Not 100% but that's how I remember it.
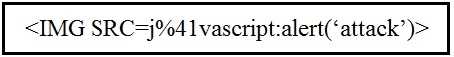 Which kind of attack method is depicted in this string?
Which kind of attack method is depicted in this string?Not B, A. The string uses an <IMG SRC=javascript:...> tag, which is textbook cross-site scripting (XSS), not SQL injection or MITM. B is a bit of a trap here since the code looks odd at first glance, but it's about browser code execution, not interception or DB queries. Pretty sure A is right, open to more input if I missed something.
javascript: in tags. Let me know if someone saw a different pattern, but pretty sure it’s A.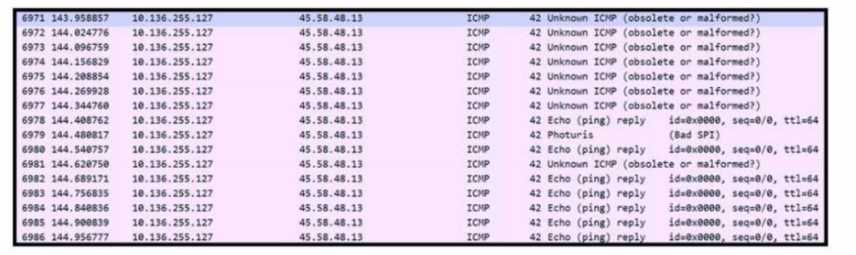 Refer to the exhibit. An engineer received a ticket to analyze unusual network traffic. What is
occurring?
Refer to the exhibit. An engineer received a ticket to analyze unusual network traffic. What is
occurring?I don’t think B fits here, since data exfiltration usually shows smaller, sustained outbound flows. The traffic spike in the exhibit looks more like a flood, classic for a denial-of-service attack (A). Regular traffic (C) is a trap option. Open to other thoughts if I missed something on the graph.
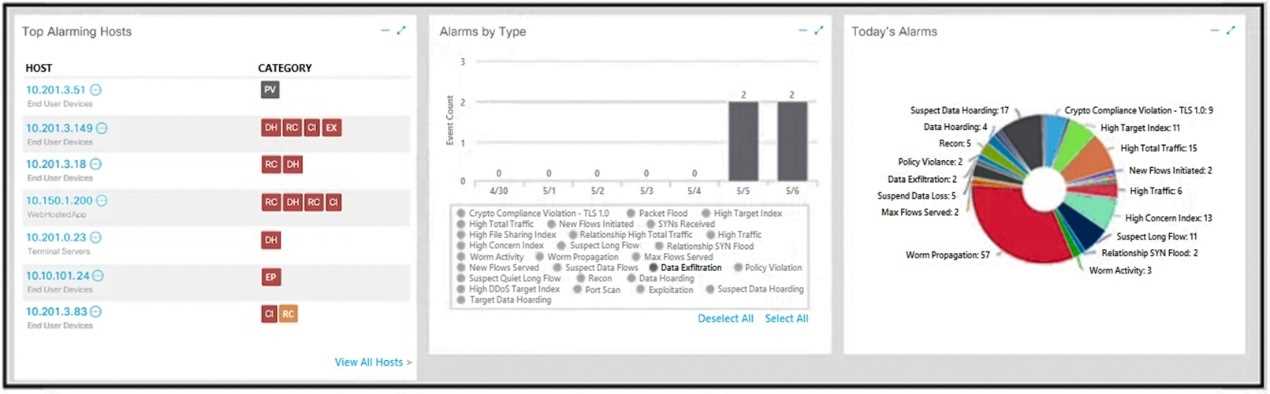 What is the potential threat identified in this Stealthwatch dashboard?
What is the potential threat identified in this Stealthwatch dashboard?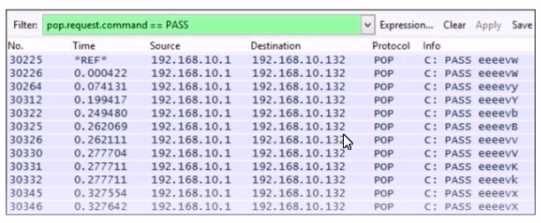 Which alert is identified from this packet capture?
Which alert is identified from this packet capture?
