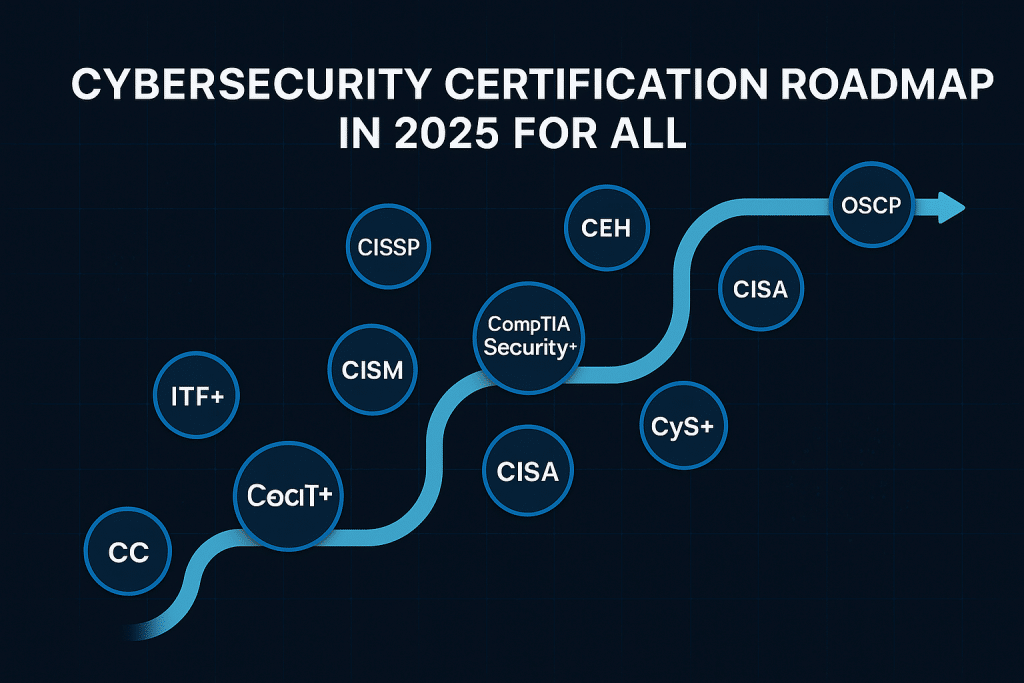
Cybersecurity is full of certifications, and figuring out where to begin can feel overwhelming. The truth is, not every certification is worth your time right away. A roadmap helps cut through the noise. It shows you which ones matter at your stage, whether you’re just starting out, switching careers, or already working in IT, and how to build step by step.
Instead of jumping in blindly, you get a clear career path that matches real jobs and keeps you moving forward with purpose.
Who This Roadmap Is For?
This Cybersecurity certification roadmap is for people at different stages of their career who want to break into or grow within cybersecurity:
- Career switchers with little or no IT background: You want a simple on-ramp and proof that you can learn quickly, eventually paving the way to high-paying cybersecurity jobs.
- Early-career IT pros (helpdesk, desktop support, networking, sysadmin): You’ve worked with tickets and infrastructure, and now you want to make a real impact in security.
- Students and recent graduates: You need a strong signal for internships or junior roles, along with a small but effective portfolio.
- Mid-career professionals pivoting into security (cloud, data, software, audit): You already have domain strengths, and this roadmap helps align them with security-focused roles.
What will You Get?
This isn’t about chasing logos, it’s about building real skills and moving with purpose. With this roadmap, you’ll find:
- Role-based, stackable cybersecurity certification paths that map to SOC, cloud, GRC, pentesting, DFIR, IAM, and AppSec.
- Clear sequences from foundation to advanced, with realistic timelines.
- 60–90 day milestones so you always know the next step.
- Practical study guidance, including labs, practice exams, and budget-friendly resources.
- A “one primary resource + one practice set” approach, so you avoid overwhelm.
- Weekly micro-labs to build hands-on skills.
- Direct links to official vendor sources, study blueprints, and trusted prep hubs only.
How to Use This Roadmap?
The best way to get value from this roadmap is to keep it simple and focused:
- Start with the “Core Principles” section to understand the foundation.
- Jump to the track that matches your target role.
- Pick one near-term milestone (60–90 days) to focus on.
- Stick to one solid study resource and a reputable practice exam set, don’t scatter your attention.
This way, you always know what’s next, avoid distraction, and keep moving forward with confidence.
Quick persona-to-first-move Guide
| Persona | First milestone (60–90 days) | Why this first | Tiny labs to do | Budget tip |
| Career switcher (no IT) | SC-900 or ITF+ (book immediately) | Fast fundamentals; security vocabulary; confidence boost | Enable MFA everywhere; compare password policies; trace a DNS lookup | Use vendor discounts; pick one course + one practice set |
| Early-career IT (helpdesk/desktop/net/sys) | Security+ (SY0-701) | Most requested baseline; bridges ops to security tasks | Harden a Windows/Linux host; write basic firewall rules; parse auth logs | Bundle voucher + retake; log CEUs as you go |
| Student / recent grad | Security+ (schedule); warm-up with SC-900 if needed | Strong interview signal; pairs well with a small GitHub portfolio | Draw a network segmentation diagram; build a basic SIEM search in Splunk Free/Elastic | Student pricing; campus resources; free cloud tiers |
| Mid-career pivot (cloud/data/software/audit) | Security+ or ISC2 CC → then role-specific (e.g., AZ-500, CISA) | Unifies fundamentals; sets up your domain strength for security roles | Cloud IAM policy test; risk register draft; container image scan (Trivy) | Employer sponsorship; align cert to team goals |
Make this Cybersecrity Certification Roadmap stick!
- Keep sessions short and focused: topic → 10–15 quiz questions → a tiny lab.
- Track weak domains early using a practice exam baseline.
- Favor legit resources with full explanations. Learn the “why,” not just answers.
- Book the exam before you feel “ready.” A date sharpens your plan.
That’s it. Pick your lane, lock one milestone, and move.
Core Principles of a Strong Cybersecurity Certification Roadmap
Be Role-Driven, Not Logo-Driven
Start with the job family you want: SOC, pentest, cloud security, GRC, DFIR, AppSec, or IAM. Then choose the shortest and clearest certification path that leads to that role.
Pick 3-5 real job postings you’d love. Highlight the required skills, tools, and certifications. Your plan should mirror that list. If a certification doesn’t move you toward a specific role, set it aside for later.
Build in Layers
Think of certifications as layers you stack over time:
- Foundations → Entry Security → Intermediate → Advanced/Specialized
Each layer should give you skills you can demonstrate, not just another badge. Treat every layer as a “ship something” checkpoint:
- Foundations: basic network map, MFA + least privilege demo
- Entry: mini incident notes or a secure baseline checklist
- Intermediate: SIEM detection, cloud policy set, or a pentest report
- Advanced: architecture diagram, risk treatment plan, or red/blue engagement write-up
You’re building demonstrable capability, not just collecting acronyms.
Vendor-Neutral vs Vendor-Specific
- Neutral certifications (CompTIA, ISC2, GIAC) give you broad theory and principles.
- Vendor certifications (Microsoft, AWS, Cisco, Palo Alto, Splunk) give you hands-on value in specific platforms.
Use neutral certs to learn the “why.” Use vendor certs to master the “how” in real environments. If your market is heavy on Azure or AWS, vendor certifications often convert faster into interviews. If you’re still exploring, neutral keeps your options open.
| Track type | Best when | Strengths | Watch-outs | Examples |
| Vendor-neutral | You’re choosing a lane or want fundamentals that transfer. | Broad theory, portable skills, strong baseline vocabulary. | Less hands-on with a specific tool; may feel abstract without labs. | CompTIA Security+, ISC2 CC/CISSP, GIAC GSEC/GCIH. |
| Vendor-specific | Your target jobs list a specific stack (Azure/AWS/Cisco/Splunk). | Direct job relevance, platform depth, faster “job-ready” signal. | Knowledge can be stack-bound; keep fundamentals fresh. | Microsoft AZ-500/SC-200, AWS Security — Specialty, Cisco CyberOps, Splunk Power User. |
Time and Energy Constraints Are Real
Set realistic expectations. Aim for 60–90 days per milestone. If you’re working full-time, plan for 5–8 hours of study each week; double that if you’re sprinting.
Guardrails that help:
- Fix a test date first, then plan backward.
- Use 2–3 focused study blocks per week (60–90 minutes each).
- Cap resources: one primary course or book + one practice exam set with full explanations.
- If a domain stalls you for 2+ sessions, schedule a tiny lab to break the block.
Hands-On Beats Trivia
Labs and scenarios build lasting skills. Use practice exams not just for scoring, but for learning style, timing, and coverage.
Keep labs atomic and repeatable:
- Blue team: parse a log sample, write one SIEM query, document one detection.
- Cloud: craft a least-privilege IAM policy, enable logging, verify with a query.
- Network: add a firewall rule, test, and record before/after packets.
- Pentest: enumerate → exploit → report a single vuln with remediation.
Practice exams are learning tools. Read every rationale, and note why wrong answers are wrong.
Keep It Ethical and Current
- Always read official exam outlines and update notes when blueprints change.
- Use legitimate prep resources with explanations, not dumps.
- Refresh quarterly by following vendor blogs, exam change logs, and product release notes.
- Credit your sources, sanitize screenshots, and respect NDAs, your integrity is part of your hire signal.
Also, track CPE/CEU activities from day one. Keeping a lightweight log saves you renewal headaches later.
Tip: If you’re ever torn between two paths, ask, “Which one gets me interview-ready sooner for the exact role I want?” Choose that, then iterate.
Entry-level security (2–6 months): Prove you are Security-ready
Pick One Primary Certification
Start with one certification. At most, choose two if they clearly complement your target role. The goal isn’t to collect logos, it’s to prove you can speak security, read logs, spot risks, and follow basic incident playbooks.
Primary Targets (Choose 1–2)
ISC2 Certified in Cybersecurity (CC)
- Vendor-neutral principles, incident basics, light governance.
- Recognized global brand with no experience prerequisite.
- Great for confidence and vocabulary building.
CompTIA Security+ (SY0-701)
- Widely recognized baseline across risk, network/app security, incident response, and governance.
- Considered the “capstone” entry-level cert, with broader coverage than most.
Cisco Certified CyberOps Associate
- Strong focus on SOC operations fundamentals: log analysis, SIEM, and triage workflows.
- Ideal if you’re aiming for analyst roles.
Why These Certifications Matter
These certifications align closely with what appears in junior security job postings. They validate not just theory, but your operational understanding: the vocabulary, tools, and workflows that employers expect.
Exam Prep Essentials
- Start with the official exam blueprint, it defines what you’ll be tested on.
- Mix in small labs (policy setup, firewall rules, log searches) for hands-on learning.
- Use reputable practice exams to sharpen timing and identify weak areas.
Which One Should You Pick?
- Brand new to security: Start with ISC2 CC for vocabulary and confidence, then move to Security+.
- Already in IT (helpdesk, network, sysadmin): Go straight to Security+.
SOC-curious / targeting analyst roles: Pair Security+ with Cisco CyberOps, in either order.
Key Differences Between Cybersecurity Certifications at a Glance
| Certification | Focus Areas | Exam details | Prep window | Renewal | Best for |
| ISC2 CC | Core security concepts, access control, network basics, incident fundamentals | ~100 questions, ~2 hrs, multiple choice | 4–8 weeks if new; faster with IT background | 3 years; CPEs + annual fee | First security cert, career switchers, students |
| CompTIA Security+ (SY0-701) | Risk, network/app/cloud security, identity, incident response, governance | Up to 90 questions, 90 mins; MCQ + performance-based | 8–12 weeks typical; build labs weekly | 3 years; CEUs or higher-level cert | Universal baseline; meets DoD 8140/8570 IAT II |
| Cisco CyberOps Associate | SOC workflows, SIEM, threat intel basics, detection/triage, forensics-lite | ~95–105 questions, ~120 mins | 8–12 weeks with hands-on log work | 3 years; CE credits or retake | SOC/Tier 1 Analyst path, blue-team focus |
Practical micro-labs (hands-on beats trivia)Practical Micro-Labs (Hands-On Beats Trivia)
Identity Basics
- Spin up a free Microsoft Entra trial.
- Configure MFA and a conditional access rule.
- Test with a throwaway user and record the outcomes.
Network and Firewall
- Use pfSense or OPNsense in a VM.
- Create an allow-list rule for HTTP/HTTPS and block everything else.
- Verify with curl and browser tests.
Logging and SIEM
- Send Windows Event Logs or Linux syslog to a local ELK stack or Splunk Free.
- Search for failed logons, new local admin creation, and service installs.
Web Security Quick Checks
- Run OWASP ZAP in safe mode against a demo app (e.g., OWASP Juice Shop locally).
- Identify findings and map at least 2 issues to mitigations.
Incident Fundamentals
- Write a 1-page incident note from a simulated phishing alert.
- Include indicators, containment steps, and recovery verification.
Study Approach That Works
- Start with the official exam objectives and turn them into a checklist. Bold the weak areas.
- Use one primary course/book + one practice-exam set with full explanations.
- Stick to a cadence of 3 sessions per week (60–90 mins each):
- Learn → 10–15 practice questions → update notes.
- Add 1 small lab per week. Keep it repeatable and documented.
Practice Exams
- Take a baseline practice test at the 30% mark to identify weak domains.
- Run weekly full mocks during the final 2–3 weeks.
- Review every single miss, understand why wrong answers are wrong and why right answers are right.
Example 8–10 Week Sprint (Security+ Sample)
- Weeks 1–2: Cover Domains 1–2 + labs (MFA policy, basic firewall rules).
- Weeks 3–4: Cover Domains 3–4 + SIEM searches (auth failures, admin events).
- Week 5: Take a baseline full practice exam; fix top 2 weak areas.
- Weeks 6–7: Remaining domains + lab on secure configs (CIS Benchmarks).
- Weeks 8–9: Weekly full practice exams; tighten timing and rationale.
- Week 10: Light review, redraw core diagrams (CIA triad vs risk, identity flows, network zones), then sit the exam.
Resource Picks (Straight to the Point)
- Official Outlines: ISC2 CC, CompTIA Security+ (SY0-701), Cisco 200-201 CBROPS.
- Structured prep + updated practice sets with explanations:
Quick Decision Guide
- Need a fast win to unlock interviews: ISC2 CC (~6 weeks).
- Need a widely requested baseline + DoD alignment: Security+ (~10 weeks).
- Targeting SOC roles and log work: Cisco CyberOps + a SIEM user cert or lab portfolio.
Tip: Publish What You Learn
After each lab, post a short write-up with sanitized screenshots. Tag the exam domain it supports. This proves real skill, not just study effort, and it doubles as a portfolio.
Advanced/professional (12–36+ months): leadership and deep specialization
You’ve moved past “how do I configure it?” and into “why, where, and how do we secure at scale?” This tier signals judgment, breadth, and depth. Expect architecture, trade-offs, and real impact.
Prerequisite Expectations
To operate at this level, you’ll need:
- Multi-year hands-on experience or significant lab/portfolio proof.
- Evidence of shipped detections, remediations, secure designs, or real engagements.
- A tidy GitHub, internal write-ups, or a homelab with reproducible scenarios.
For some certifications, formal experience requirements apply. However, “Associate” paths exist:
- CISSP/CCSP: You can pass now and earn the endorsement later as an Associate of ISC2.
- Always read each vendor’s policy before booking.
High-Signal Options
ISC2 CISSP
- Broad coverage of leadership-level domains.
- Associate of ISC2 path available if you lack full experience.
- Strong for mobility into lead, manager, architect, or consultant roles.
ISC2 CCSP
- Focused on advanced cloud security architecture and governance.
- Best pursued with real-world cloud exposure.
- CISSP can waive CCSP experience requirements.
- Ideal as a follow-up to AZ-500 or AWS Security Specialty.
CompTIA CASP+
- Practitioner track for architecture, enterprise risk, and integration.
- Best for senior engineers who design and validate hands-on solutions.
- Less management focus; more about technical leadership.
GIAC/SANS Portfolio (GSEC, GCIH, GCIA, GDAT, GCSA, GMON, GCFE, etc.)
- Deep, role-specific mastery with strong employer recognition.
- Premium cost, but unmatched in credibility.
- Great for specialization: IR, forensics, detection engineering, cloud, ICS.
Offensive Security (OSCP, OSWA, OSWE)
- Hands-on, rigorous, portfolio-grade offensive certifications.
- OSCP: Demonstrates methodology, pivoting, and reporting under time pressure.
- OSWA/OSWE: Prove advanced web and application exploitation skills.
| Certification | Best For | What It Proves | Experience Sweet Spot | Hands-on vs Theory | Renewal | Cost Level | Typical Prep Time |
| CISSP (ISC2) | Security leadership, architect, senior consultant | Breadth across 8 domains, risk trade-offs, program design | 4–7 years (Associate path if less) | More theory/architecture than labs | CPEs (120/3yrs) + AMF | High | 10–16 weeks |
| CCSP (ISC2) | Cloud security architect/engineer | Cloud architecture, governance, SaaS/IaaS/PaaS controls | 3–6 years (CISSP can waive) | Architecture + scenarios | CPEs (90/3yrs) + AMF | High | 8–14 weeks |
| CASP+ (CompTIA) | Senior practitioner/architect, hands-on | Enterprise design, risk, integration under constraints | 5–10 years (recommended) | Mixed: scenario-heavy, technical | CEUs (every 3yrs) | Medium–High | 8–12 weeks |
| GIAC (SANS) | Deep specialists (IR, forensics, detection, cloud, ICS) | Role-specific mastery and tool/artifact fluency | 2–8 years in-lane | Strong hands-on + exams | CPEs (cycle ~4yrs) | Very High | 3–10 weeks post-course |
| OSCP/OSWA/OSWE (OffSec) | Red team/pentest, app exploit specialists | Real exploitation, pivoting, rigorous reporting | 1–4 years offensive focus | Very hands-on, timed exams | No formal CPE (as of now) | High | 8–16+ weeks with labs |
Key Certifications for Career Growth
Whether you’re new to the field or looking to advance, you’ll want to focus on certifications that match your career goals. Starting with a foundational certification like Security+ will help you establish a solid understanding of core security concepts. From there, you can build on those fundamentals as you gain more experience.
As you progress, you might want to tackle more advanced exams. Some of the hardest certifications challenge even the most experienced professionals, but passing them will significantly boost your credibility in the cybersecurity space and open doors to more specialized roles.
When to Attempt
After you’ve delivered real projects, detections, remediations, or engagements.
If you can tell a 2–3 minute story for each domain (what you built, why, impact), you’re ready.
When your role requires broader design, risk, or leadership chops.
Being asked “should we do X or Y?” is a strong signal. So is mentoring, reviewing designs, or owning roadmaps.
Decision Mini-Guide
- Want leadership breadth and long-term mobility? Pick CISSP first, then add CCSP if cloud-heavy.
- Designing cloud guardrails day-to-day? CCSP fits right after AZ-500/AWS Security Specialty/Google PCSE.
- Remaining deeply technical and hands-on? CASP+ over CISSP, then a focused GIAC in your lane.
- Targeting offensive credibility? OSCP → OSWA/OSWE. Keep a clean portfolio and reporting samples.
Micro Study Plans (Keep it Tight)
CISSP (10–16 weeks)
2 domains/week: read + notes → 50–75 Qs with rationales → mini “why” summaries.
Final 3 weeks: full timed mocks, brain-dump diagrams (network models, IAM flows, BCP/DR).
CCSP (8–14 weeks)
Map each domain to your cloud stack. Do 1–2 small labs per week (KMS, IAM, logging pipelines).
Practice scenario stems: “most cost-effective,” “shared responsibility,” “jurisdiction.”
CASP+ (8–12 weeks)
Scenario drills: given constraints X/Y/Z, pick the design. Sketch trade-off matrices.
Refresh crypto, enterprise auth, SDN, hybrid patterns.
GIAC (3–10 weeks post-course)
Lab the tools/artifacts immediately after class. Build index/notes. Run 2 practice tests end-to-end.
OSCP (8–16+ weeks)
Daily rep: 1 box/day rhythm. Write every step. Post-mortem each fail. Practice reporting early.
Week -2: full mock under exam timing, report same day.
Tips to Lock Value
Pair an advanced “breadth” cert with a “depth” cert. Example: CISSP + GMON, CCSP + GCSA, CASP+ + GCIA, OSCP + cloud attack labs.
Show outcomes, not just badges: architecture diagrams, detections that fired, sanitized reports.
Budget smart: ask employers for SANS/OffSec sponsorship tied to SOC uplift, compliance, or app-sec risk reduction.
Specialization Tracks: Pick Your Lane
Pick a path that matches the work you want to do daily. Use the Start → Build → Advanced flow as your spine. Then add one or two small, repeatable labs that show you can apply it. Keep cycles tight. Ship proof.
SOC Analyst / Blue Team
- Start: ISC2 CC or Security+, Cisco CyberOps.
Build: CySA+, Splunk/Sentinel skills, GMON/GCIH if budget allows.
Advanced: CISSP (for career growth), GIAC specialized blue-team certs - Skills/labs: log parsing, correlation rules, triage playbooks, case notes, threat intel basics.
Cloud Security (Azure/AWS/GCP)
- Start: Security+ or SC-900 + cloud fundamentals (AZ-900/AWS Cloud Practitioner).
- Build: AZ-500, AWS Security — Specialty, Google PCSE.
- Advanced: CCSP, GIAC cloud tracks, vendor CNAPP/tooling certs.
- Skills/labs: IAM policies, network segmentation, key management, logging pipelines, CSPM/CWPP basics.
Red Team / Pentest
- Start: Security+, eJPT/eJPTv2.
- Build: PenTest+, OSCP; add web app focus (Burp, OSWA/OSWE) as needed.
- Advanced: Specialized exploit dev, adversary emulation frameworks, cloud attacks.
- Skills/labs: methodology, scoping, reporting, chain-of-attack thinking, OPSEC.
Governance, Risk, and Compliance (GRC) / Audit
- Start: Security+, ISC2 CC.
- Build: ISACA CISA (audit), ISO 27001 lead implementer/lead auditor courses.
- Advanced: CISM for leadership; CISSP for breadth; privacy certs (where relevant).
- Skills/labs: control mapping, risk registers, policy authoring, audit evidence, metrics.
DFIR / Threat Hunting
- Start: Security+, SOC fundamentals.
- Build: Splunk/Sentinel, memory/disk forensics fundamentals, GCIH/GCFA/GCFE if possible.
- Advanced: Threat hunting methodologies, purple teaming.
- Skills/labs: evidence handling, host/network artifacts, timeline analysis, detection engineering.
IAM (Identity and Access Management)
Start: SC-900, Security+.
Build: Azure AD/Entra, Okta, Ping product certs; AWS IAM specialization via labs.
Advanced: Architecture and governance paths (CISSP, CCSP).
Skills/labs: SSO, federation, conditional access, PAM, SCIM, lifecycle management.
Application Security / DevSecOps
- Start: Security+, developer-sec awareness training.
- Build: Cloud provider security, container/k8s security certs and labs.
- Advanced: OSWE, secure SDLC leadership, threat modeling mastery.
- Skills/labs: SAST/DAST/IaC scanning, SBOMs, supply chain controls, pipeline policies.
OT/ICS Security
- Start: Security+ plus industrial network fundamentals.
- Build: Vendor/industry ICS security courses and certs, network monitoring tooling.
- Advanced: Specialized ICS incident response and safety controls.
- Skills/labs: Purdue model, safety-critical constraints, passive monitoring, asset inventory.
Bold, Simple Actions You Can Take Now
- Pick one track. Circle the Start item. Book the exam for 8–10 weeks out.
- Add one micro-lab that mirrors the “Skills/labs” line. Keep it small and repeatable.
- Write a 1–2 paragraph summary of what you configured, why, and the result. That’s your first portfolio artifact.
Micro-Labs That Show Real Ability (Choose One per Track)
- SOC Analyst / Blue Team: Parse a week of Windows/Sysmon logs; build 3 SIEM correlation rules; document 2 false positives and fixes.
- Cloud Security: Create a least-privilege IAM policy for a serverless app; log to centralized storage; alert on high-risk actions.
- Red Team / Pentest: Recon + exploit a vulnerable web app in a homelab; capture chain-of-attack notes; write a tight, executive-safe summary.
- GRC / Audit: Map 10 controls from NIST 800-53 to a small SaaS; build an audit evidence checklist; log 3 metrics.
- DFIR / Threat Hunting: Acquire a memory image; carve credentials/process artifacts; build a 5-query hunt pack with expected findings.
- IAM: Implement SSO with SAML/OIDC in a test tenant; add conditional access and step-up MFA; show lifecycle automation via SCIM.
- Application Security / DevSecOps: Add SAST, DAST, and IaC scans to a CI pipeline; require code owners for critical paths; ship a SBOM.
- OT/ICS: Draw a Purdue-aligned network map; test passive traffic collection; inventory assets and flag unauthorized changes.
Quick Comparison
| Track | Start | Build | Advanced | Core lab focus |
| SOC / Blue Team | ISC2 CC or Security+, Cisco CyberOps | CySA+, Splunk/Sentinel | CISSP; GIAC blue (GMON/GCIH, etc.) | SIEM parsing, correlation, triage notes |
| Cloud Security | Security+ or SC-900 + AZ-900/AWS CP | AZ-500; AWS Sec–Specialty; Google PCSE | CCSP; GIAC cloud; CNAPP/tooling | IAM policies, segmentation, keys, logging |
| Red Team / Pentest | Security+, eJPT/eJPTv2 | PenTest+, OSCP; OSWA/OSWE | Exploit dev; adversary emulation; cloud attacks | Scoping, chain-of-attack, reporting |
| GRC / Audit | Security+, ISC2 CC | CISA; ISO 27001 LI/LA | CISM; CISSP; privacy (e.g., CIPM) | Control mapping, risk registers, evidence |
| DFIR / Threat Hunting | Security+, SOC fundamentals | Splunk/Sentinel; GCIH/GCFA/GCFE | Hunt methodologies; purple team | Artifacts, timelines, detections |
| IAM | SC-900, Security+ | Entra/Okta/Ping; AWS IAM labs | CISSP; CCSP | SSO, federation, CA, PAM, lifecycle |
| AppSec / DevSecOps | Security+, secure coding | Cloud + container/K8s security | OSWE; secure SDLC leadership | SAST/DAST/IaC, SBOM, pipeline policies |
| OT/ICS Security | Security+; industrial network basics | ICS vendor courses; monitoring tools | ICS IR; safety controls | Purdue model, passive monitoring, inventory |
Tips to Pick Fast (No Overthinking)
- Choose the environment you already touch (Windows logs? Azure? CI/CD?). That’s your track.
- If roles near you demand vendor skills, favor that stack in the Build step.
- Keep labs close to job tasks. Your resume bullets should read like your lab notes.
Outcome You’re Aiming For
- A clear 3-step cert ladder per track.
- One mini-project that proves you can do the work.
- Language that speaks to job posts: alerts, detections, IAM policies, threat models, audits.
Study Method That Works in the Real World
You don’t need a perfect system. You need a routine that sticks and proves progress weekly. Here’s a field-tested way to study around a full-time job and still pass.
Pre-Game
- Download the official exam objectives first.
- Print or copy the blueprint. Turn each domain into a checklist.
- Weight your time by domain percentages.
- Skim exam policies (question types, PBQs/sims, time, scoring). No surprises on test day.
- Choose 1 primary learning resource (book or video) and 1 practice exam set with full explanations.
- One core course/book to learn. One practice bank to measure and correct. That’s it. Avoid resource overload.
Set the Date
- Book the exam 8–10 weeks out.
- Work backward to create 8 weekly sprints.
- Deadlines focus the mind.
Prep a Tiny Lab
Minimal but real: a VM or two (Windows + Linux), a browser, and free-tier cloud.
Good starters:
- Azure free
- AWS free
- M365 Dev tenant + Microsoft Sentinel trial
- Splunk Free/Trial
- Kali VM
- Wireshark
- nmap
- OpenSSL
Start Two Living Docs
- A “miss log” (what you got wrong, why, the fix).
- A glossary (short, plain definitions you write).
Build Your Diagram Set
Aim for 2–3 core diagrams you can redraw fast:
- Identity flow (IdP/SP, tokens)
- Network segmentation (VPC/VNet, subnets, SG/NSG)
- Logging pipeline (sources → SIEM → alerts)
| Pre-game item | Why it matters | Tool/Link (examples) |
| Blueprint download | Sets scope and week-by-week plan | Official vendor exam page |
| Schedule exam | Creates urgency and pacing | Pearson VUE / PSI (vendor portal) |
| Primary resource | Single source of truth while learning | Official Study Guide or reputable course |
| Practice set | Timing, coverage, rationales for each item | MeasureUp, Boson, Wiley Test Bank, CertEmpire |
| Mini lab | Hands-on beats trivia | Azure/AWS free tiers, Splunk Free, Sentinel |
| Miss log + Glossary | Turns errors into points | Simple sheet or notes app |
| Core diagrams | Fast recall under time pressure | Any drawing tool or pen/pape |
Weekly Cadence (While Working Full-Time)
- 2–3 study blocks of 60–90 minutes.
- Keep it light but consistent. If life gets loud, do 45-minute blocks.
- Momentum beats marathons.
Structure of Each Study Block
- Learn (30–40 minutes max): cover one topic.
- Quiz (10–15 questions): do it immediately after learning.
- Notes: tighten definitions, add one tiny diagram.
- Recall (5 minutes): close your notes, list key terms from memory.
Weekly Lab Practice (One Small Lab)
Keep labs atomic and repeatable, simple steps that you can re-run quickly.
- Networking: run nmap -sV against a test VM; explain one finding in plain words.
- Identity: create a conditional access policy in Entra/Azure AD test tenant; test a block scenario.
- Cloud: deploy a locked-down storage bucket with least-privilege IAM; verify deny works.
- Logging: send a few logs to Splunk/Sentinel; write one search/KQL query that finds failed logins.
- Crypto/TLS: use openssl s_client -connect example.com:443 and read the cert chain.
- OS: on Linux, set file perms with chmod; on Windows, review Security Event IDs for logon types.
Keep a Lab Recipe
- Write down the steps, why you did it, and one screenshot/query.
Re-run in 10 minutes next week to reinforce memory.
| Day | Focus | Actions | Output | Time |
| Mon | Domain study | Watch/read 1 topic, 10–15 Q quiz, notes | Updated notes + 1 micro-diagram | 60–90m |
| Wed | Drill + recall | Revisit weak items, flashcards, quick quiz | Miss log entries + glossary adds | 60m |
| Sat | Atomic lab | Run 1 lab, save steps, screenshot/query | Lab recipe (repeatable) | 60–90m |
Practice Exam Strategy
- Baseline mock: Take your first timed practice exam at 25–33% through your study to find weak domains.
- Don’t chase a score, chase patterns. Update your miss log by domain.
- In the final 2–3 weeks, do one full timed practice exam per week.
- Aim for stable 80–85% on fresh sets. Rotate providers if possible to avoid memorization.
- Always do a miss-analysis:
- Why each wrong option is wrong
- Why your pick failed
- Why the right one wins
- Trigger words you missed (“BEST,” “FIRST,” “EXCEPT”)
- Read rationales even when you’re right. Confirm the “why” and capture any new nuance.
Timing and Triage
- Budget: total questions ÷ time = questions per minute.
- Mark long scenarios and return later.
- PBQs/simulations: either tackle first while fresh or last after quick wins—pick one strategy and practice it.
Item Types Mindset
- Expect scenario sets, multi-select, drag/drop, PBQs. Practice all types.
- For “EXCEPT/NOT” items, highlight the negation mentally and restate the ask.
Active Recall Boosters
- Flashcards (Anki or simple notes).
- Keep one small deck: terms, ports, cloud/IAM gotchas, IR steps.
- Review 10 minutes per day.
Exam Week
- Light review of weak domains.
- Re-draw 2–3 core diagrams from memory.
- One pass through the blueprint, no new topics.
- Fix gaps when redrawing diagrams.
- Sleep and hydration are non-negotiable.
- No cramming the night before.
- Taper study 24 hours out—short warm-up only (15–20 quiz items you’re likely to get right).
Logistics Check (Online or Test Center)
- Valid ID, exam time, route/parking.
- System check for online proctoring.
- Quiet room, cleared desk.
- Test your webcam and internet.
Test-Day Game Plan
- Breathe, read stems slowly, underline constraints in your head (budget, compliance, “first,” “most secure,” “least effort”).
- Eliminate two wrong choices fast.
- Flag edge cases.
- Keep pace
- Trust your prep.
After You Submit
- Jot quick notes on what felt tough (domains only).
- If a retake is needed, you’ve got the map.
If you pass, update your CE/CPE log and post one short lab write-up.
Prove it: Portfolio Beats Paragraphs
Hiring managers believe evidence. Short, clear artifacts beat a wall of buzzwords every time. Build small, repeatable pieces that show decisions, not just screenshots.
What to show
- 2–3 short lab write-ups with screenshots/logs
- Show the exact prompt, steps, and result. Include queries/commands, raw output, and a one-line takeaway.
- Examples: detect encoded PowerShell in logs; enforce least-privilege on an S3 bucket; block egress to known C2 ranges; triage a phishing alert.
- One diagram per domain (identity flow, network segmentation, pipeline controls)
- Label data flows, trust boundaries, and controls. Add assumptions and risks.
- A mini incident playbook or audit checklist tailored to a common framework
- Phishing triage, ransomware containment, or a NIST CSF/ISO 27001 Annex A control walkthrough with evidence types.
Where to show it
- GitHub/GitLab for lab artifacts (sanitize secrets)
- Repo naming: role-first (e.g., soc-detections, cloud-iam-labs, appsec-pipeline-guards).
- Structure: README at root, /labs, /detections, /diagrams, /docs, /artifacts.
- LinkedIn feature section for diagrams and summaries
- Post a 3–5 image carousel with a tight caption and a link to the repo.
- Interview-ready: a 2–3 minute story per project
- Keep one-page quick-reads (PDF) per project on your drive or printed.
Portfolio Asset Blueprint
| Asset | Example idea | Evidence to include | Tools/Tech | Maps to roles/certs |
| Lab write-up (detection) | Detect encoded PowerShell (Base64) in process logs | Event IDs/raw logs, query (KQL/SPL), FP/FN notes, before/after alert | Sysmon, Splunk or Microsoft Sentinel | SOC Analyst, Security+, CySA+ |
| Cloud hardening mini | Lock down S3 bucket and add IAM least privilege | Policy diff (before→after), CloudTrail snippet, misconfig proof | AWS IAM, CloudTrail, AWS CLI | Cloud Sec Eng, AZ-500, AWS Security – Specialty |
| Network segmentation diagram | Hub-spoke VNet/VPC with NSGs/NACLs for tiered app | Diagram (PNG/SVG), rules table, threat model notes | draw.io/diagrams.net, Azure or AWS console | Security Engineer, AZ-500, Network+/Security+ |
| Pipeline control | Add SAST and IaC checks to CI with policy gates | Workflow YAML, failing→passing runs, sample findings | GitHub Actions, Trivy/Checkov, Semgrep | AppSec/DevSecOps, OSWA/OSWE (later) |
| Mini incident playbook | Phishing triage and containment | Trigger, roles, tools, step-by-step, timing, exit criteria | M365/Defender, Posture policies, SOAR (optional) | SOC/IR, GCIH (aspiring) |
| Audit checklist | Map controls to NIST CSF or ISO 27001 Annex A | Control, test step, evidence type, pass/fail example | Spreadsheet + policy snippets | GRC/Audit, CISA track |
| Threat hunt notebook | Failed logins → MFA fatigue → suspicious token | Hypothesis, data sources, queries, findings, next steps | Sentinel KQL/Splunk SPL, Jupyter (optional) | Threat Hunter, CySA+/GMON (aspiring) |
How to show it (simple templates)
- Lab README skeleton
- Title: one-line outcome (e.g., “Detect encoded PowerShell with Sysmon + Sentinel”)
- Context: why it matters (1–2 sentences)
- Steps: numbered, each with the exact command/query
- Evidence: screenshot + short caption; link to raw logs/artifacts
- Result: what improved (alert fidelity, reduced noise, blocked action)
- Next: how you’d harden or scale it
- Diagram notes
- Add a legend, trust boundaries, and callouts like “enforce TLS”, “deny egress”, “rotate keys”.
- Playbook/checklist
- Trigger → Identify → Contain → Eradicate → Recover → Lessons. Include roles and timing targets.
2–3 minute project story (use CARL: Context, Action, Result, Learning)
| Step | Prompt | Example (detection lab) |
| Context | What problem and why now? | Encoded PowerShell bypassed simple keyword rules; I wanted a resilient detection. |
| Action | What you did, specifically? | Enabled Sysmon, parsed CommandLine, built a KQL to flag -enc/base64 patterns and long entropy strings. |
| Result | Impact with a number | Reduced false positives by ~60% in a 24h sample; surfaced 2 true positives in test data. |
| Learning | What you’d change next time? | Add parent-child proc chains and blocklist common admin tools used for LOLBins. |
Quality checklist (use this before you share)
- Reproducible: steps run on a fresh VM/cloud account.
- Minimal: one objective per artifact; small scope, big clarity.
- Measured: include a simple metric (time saved, alerts reduced, risk lowered).
- Mapped: reference a framework or ATT&CK technique when relevant.
- Clean: no secrets, tokens, org names, or internal screenshots.
Sanitization and ethics
- Replace org details with placeholders; redact hostnames, user emails, account IDs.
- Use sample data where possible. If in doubt, re-create the scenario in your own lab.
- Credit sources and tools. Avoid exam dumps or copyrighted content.
Make it discoverable
- Add tags/keywords in READMEs: “KQL”, “Sysmon”, “AWS IAM”, “NIST CSF”, “MITRE ATT&CK T1059”.
- Use concise repo descriptions and a pinned portfolio repo linking to all projects.
- Post a short demo clip (60–90s) walking through the result, then link to the write-up.
Fast start (this week)
- Pick one lab from your current cert’s blueprint and ship it in a repo.
- Draw one diagram for identity or network flow and post it with a caption.
- Outline one page of a phishing or audit checklist using the template above.
Small, sharp, and verifiable wins. That’s what gets callbacks.
Common pitfalls and how to dodge them
Quick reality check: everyone bumps into these. The win is noticing early and course-correcting fast.
| Pitfall | Why it hurts | Quick fix | 1‑minute action |
| Waiting to schedule until you “feel ready” | No deadline. Scope creep. Momentum fades. | Book 6–10 weeks out. Back-plan weekly targets. | Open the test vendor site. Pick a date. Add to calendar. |
| Only watching videos, no quizzes or labs | Passive learning. Poor recall on exam tasks. | Add quizzes + one tiny lab every week. | Queue a 10‑question quiz for your next session. |
| Memorizing answers without understanding | Shaky reasoning. Curveball questions break you. | Use practice sets with full rationales. Write the “why.” | Create a “why-not” note for your last 5 misses. |
| Chasing too many certs at once | Split focus. Lower pass rates. Burnout risk. | Limit WIP: one cert per quarter. | Pause other courses. Keep one open tab only. |
| Skipping official objectives | Study gaps. Surprises on exam day. | Mirror the blueprint in your study plan. | Download the objectives PDF. Turn it into a checklist. |
Waiting to Schedule Until You “Feel Ready”
- Set a date 6–10 weeks out and work backward.
- Add guardrails:
- Put the exam on your calendar and invite an accountability buddy.
- Block two 60–90 minute study slots weekly. Protect them like meetings.
- Milestones:
- Week 3 baseline quiz
- Week 6 full practice
- Week 8 review + exam
Micro-Template (8-Week Back-Plan)
- Week 1–2: Read/primary course for Domains A–B + 1 micro-lab each week.
- Week 3–4: Domains C–D + baseline practice; fix weak areas.
- Week 5–6: Domains E–F + first full timed practice; miss-analysis.
- Week 7: Targeted review + second timed practice.
- Week 8: Light review, diagrams, sleep, test.
Only Watching Videos, No Quizzes or Labs
- Add practice and hands-on each week, even if tiny.
- Keep labs atomic (15–30 minutes).
- Networking: capture a curl request and read the HTTP/TLS details.
- IAM: create a least-privilege policy; test deny-by-default behavior.
- SIEM: run a basic KQL/SPL query to find failed logons; save a detection.
- Firewall: write a rule to allow 443, block 23; verify logs.
Fast feedback loop:
- After each lesson, take a 10–15 question quiz.
- Missed a question? Note the concept, add one tiny lab to cement it.
Memorizing Answers Without Understanding
- Favor practice exams with full rationales; study the “why,” not just the “what.”
- Build a “distractor diary”:
- For each miss, write why wrong options are wrong (scope, layer, threat model).
- Capture the keyword that should have steered you (e.g., “cost control,” “federation,” “zero trust”).
Teach-back trick:
- Explain the concept to a rubber duck, colleague, or voice note in 60 seconds.
- If you can’t, you don’t own it yet, revisit notes and lab it.
Chasing Too Many Certs at Once
- One cert per quarter max for working professionals.
- Use a WIP limit:
- One primary cert
- One passive resource (podcast/reading) only
- Park everything else on a “Later” list with dates.
Sequence by role, not hype:
- Ask: “Does this cert move me toward SOC, cloud, GRC, pentest, DFIR, IAM, or AppSec right now?”
- If no, it waits.
Skipping Official Objectives
- Your study plan should mirror the blueprint. No surprises.
- Turn the objectives into a living checklist:
- Map each bullet to a resource (timestamp/page) and one lab.
- Score confidence 1–3. Anything ≤2 gets a lab and a quiz.
Pre-exam sweep:
- Re-draw 2–3 core diagrams from memory (IAM flow, network segmentation, pipeline controls).
- Revisit any objective with weak notes and add a 5-minute flash lab.
Pro move:
- Keep a simple “evidence log” as you go, dates studied, labs completed, practice scores, and what improved.
It’s gold for both renewals and interviews.
Vendor roadmaps at a glance (choose the bits that fit your role)
Pick the vendor lane that matches your stack or target job. Use the table to scan levels, then jump to the notes for fit, renewals, and links.
| Vendor | Entry / Fundamentals | Role-focused / Intermediate | Advanced / Professional | Best for | Validity / Renewal |
| ISC2 | Certified in Cybersecurity (CC) | — | CISSP; CCSP (cloud) | Leadership breadth, cloud governance | 3-year cycle; CPEs + annual fees |
| CompTIA | ITF+, A+, Network+ (as needed) | Security+, CySA+, PenTest+ | CASP+ | Entry → SOC, blue team, pentest starter | 3-year; CEUs or higher-level certs |
| Microsoft Security | SC-900 | SC-200 (SOC), AZ-500 (Security Engineer) | SC-100 (Cybersecurity Architect) | Azure/M365 SOC and cloud security | Annual free online renewal assessment |
| AWS / GCP | AWS Cloud Practitioner; GCP ACE | AWS Security – Specialty; Google PCSE | Pair with AWS SA/Pro for depth | Cloud security engineering & architecture | AWS: 3-year; Google: typically 2-year |
| Cisco | CyberOps Associate | CCNP Security (core + concentration) | CCIE Security (expert) | SOC + network security in Cisco shops | 3-year; exam or CE credits |
| Splunk / Sentinel | Splunk Core User/Power User; SC-200 (Sentinel) | Splunk Enterprise Security Admin/Analyst; Sentinel content engineering | Splunk Architect; MS Security Expert paths | SIEM analyst → detection engineer | Splunk: typically 3-year; Microsoft: annual |
| Offensive Security (+ INE) | INE eJPT/eJPTv2 (stepping stone) | OffSec OSCP (core hands-on) | OSWA/OSWE (web), OSEP/OSCE3 (advanced) | Pentest, red team, web exploitation | OffSec certs don’t expire |
ISC2
- Start with CC if you’re brand new but want a respected logo and governance basics.
- Aim at CISSP for leadership breadth; use the “Associate of ISC2” route if you lack required experience.
- Cloud-focused? CCSP pairs well with real AWS/Azure work.
CompTIA
- Security+ is the baseline in most job posts. Add CySA+ for blue team analytics or PenTest+ for offensive fundamentals.
- CASP+ suits senior practitioners who prefer hands-on over management.
- Good vendor-neutral layer before you niche down.
Microsoft Security
- SC-900 sets Azure/M365 fundamentals. Then pick your lane:
- SC-200 if SOC/SIEM with Microsoft Sentinel.
- AZ-500 if building and hardening Azure workloads.
- SC-100 when you’re guiding architecture end to end.
- Renew annually via free assessments. Great ROI if your org runs on Microsoft.
AWS / GCP
- AWS Cloud Practitioner or GCP ACE for grounding.
- AWS Security – Specialty: strong coverage of IAM, KMS, network controls, logging, threat detection. Pairs well with Solutions Architect knowledge.
- Google PCSE: cloud-native security design, IAM, VPC Service Controls, logging pipelines.
- Policies and pricing change; check vendor pages for current details.
- Google Cloud: https://cloud.google.com/certification
Cisco
- CyberOps Associate: SOC workflows, triage, SIEM basics. Great for network-leaning analysts.
- Level up with CCNP Security (core + one concentration) if your environment is Cisco-heavy (NGFW, ISE, ASA/FTD).
- Expert path: CCIE Security when you live in large networks.
- Cisco Certs: https://www.cisco.com/c/en/us/training-events/certifications.html
Splunk / Microsoft Sentinel
- Splunk path: Core User → Power User → Enterprise Security (ES) Admin/Analyst. Strong for detection content and SOC maturity.
- Sentinel path: SC-200 for analytics rules, hunting, and incident response in Azure.
- Both map to SIEM analyst → detection engineer roles. Build portfolio hunts and rules as you study.
Offensive Security (+ INE eJPT)
- eJPT/eJPTv2 (INE) is a friendly, hands-on on-ramp to methodology and network/web basics.
- OSCP proves end-to-end exploitation and reporting under time pressure.
- Specialize with OSWA/OSWE for web or OSEP/OSCE3 for advanced tradecraft.
Tips to pick quickly
- If your company runs Azure/M365: go Microsoft (SC-200 or AZ-500).
- If your stack is AWS-first: go AWS Security — Specialty; add Solutions Architect knowledge.
- If you want a neutral baseline for job mobility: Security+ → CySA+/PenTest+.
- If leadership is your aim: CISSP after real hands-on.
- If you’re SIEM-bound: Splunk or Sentinel based on platform.
- If red teaming calls you: eJPT → OSCP; add OSWA/OSWE for appsec depth.
Renewal cheat notes
- CompTIA, ISC2, Cisco: 3-year windows; earn credits or pass newer/higher exams.
- Microsoft: renew yearly with a free online assessment.
- AWS: 3-year validity; re-certify on current exam or higher-level.
- Google: typically 2-year validity; retake to renew.
- OffSec: no expiration (skills still need refreshing via labs and write-ups).
Keep it simple: choose the vendor that matches your tools and job market, lock one cert per quarter, and build a tiny lab or detection per milestone.
Your first 90 days: simple, actionable plan
- Week 0
- Pick the role track and one certification that matches it.
- Book the exam date 8–10 weeks out.
- Decision-helper (fast and honest):
- If you want SOC/Blue Team: pick ISC2 CC or Security+, and a SIEM-focused lab plan.
- If you want Cloud Security: SC-900 → Security+ or AZ-500 (if you already live in Azure).
- If you want Red Team: Security+ then eJPT/eJPTv2.
- If you want GRC/Audit: Security+ or ISC2 CC; CISA later.
- Calendar setup (15 minutes, worth it):
- Block three 60–90 minute study slots per week now. Treat them like meetings.
- Reserve one 2-hour window in Weeks 4–6 for your first full practice exam.
- Add a 30-minute “note clean-up” block every Sunday.
- Lab baseline (no overbuild):
- Create a notes repo or doc (headings by exam domain).
- Spin up a tiny homelab or cloud free tier: one Windows VM, one Linux VM, or use Microsoft/AWS sandboxes.
- Install required tooling early (e.g., Wireshark, PowerShell, Azure Portal access, Splunk Free/Trial).
- Quick-pick guide (use this if you’re torn):
| Target track | Starter cert (8–10 weeks) | One mini‑lab you’ll do | Primary resource style | Hours/week |
| SOC Analyst / Blue Team | ISC2 CC or CompTIA Security+ | Search logs in Splunk/Sentinel and write one alert rule | Video + practice exams with explanations | 5–8 |
| Cloud Security (Azure) | SC-900 then AZ-500 (if ready) | Build a least‑privilege role and block public storage | Docs-first + targeted labs | 6–9 |
| Red Team / Pentest | Security+ → eJPT/eJPTv2 | Enumerate a target and write a short findings report | Hands‑on lab + method notes | 7–10 |
| GRC / Audit | ISC2 CC or Security+ | Map CIS Controls to one small environment | Book + practice Qs + framework cheat sheets | 5–7 |
- Weeks 1–3
- Study 3x per week; end each week with a 20–30 question quiz.Build a tiny glossary and 2 domain diagrams.Cadence that sticks:
- Session A (learn): 45–60 minutes on one blueprint objective; 15 minutes recap in your own words.Session B (quiz): 20–30 timed questions; tag misses by domain; jot down “why wrong.”Session C (light lab or demo): click through a console or tool matching what you studied.
- Example entries: CIA triad, risk vs. threat vs. vulnerability, TLS handshake, MFA, SSO, least privilege, SIEM, IDS vs IPS, token vs. certificate, conditional access, PAM.Format: term → one‑line definition → one example.
- Identity flow: user → IdP (Azure AD/Entra or Okta) → app → token validation.Network segmentation: Internet → edge FW → DMZ → app tier → DB tier with security groups/NSGs and logging taps.
- Micro‑habits that pay off:
- Bold your weak domains in notes. Use color coding (red/yellow/green).
- Save every quiz rationale. Patterns will jump out by Week 3.
- Study 3x per week; end each week with a 20–30 question quiz.Build a tiny glossary and 2 domain diagrams.Cadence that sticks:
- Weeks 4–6
- Add one small lab per week; tighten notes to address weak areas.Take a baseline full-length practice exam at end of week 6.Lab menu (pick based on your track; small, repeatable):
- SOC/Blue Team: ingest Windows event logs into Splunk or Sentinel; write a basic correlation rule (failed logons + geolocation anomaly).Cloud Security: create a storage bucket; misconfigure it; detect the issue via policy/alert; remediate; document.Red Team: run nmap against a lab host; parse results; attempt one safe exploitation in a sandbox; create a two‑page report.GRC/Audit: choose NIST CSF or ISO 27001; map 5–7 controls to a lab environment; list evidence you’d request.
- Convert red items to action cards: “I miss PKI questions → re‑study CRL vs OCSP; draw chain of trust; do 10 PKI items tomorrow.”Add 3–5 flashcards per weak domain (only).
- Baseline full practice (target ranges):
- Aim for 70–78% on the first full‑length set. It’s a diagnostic.
- Sort misses into: concept gap, misread, timing. Fix the root cause, not just the item.
- Add one small lab per week; tighten notes to address weak areas.Take a baseline full-length practice exam at end of week 6.Lab menu (pick based on your track; small, repeatable):
- Weeks 7–9
- Weekly full practice exams; focus on timing and rationale analysis.Light review, sleep, then test.Exam simulation rhythm:
- Week 7: Full timed exam → review every miss → re‑draw two diagrams.Week 8: Another full timed exam → aim for 80%+ with rationales → one targeted mini‑lab for your weakest domain.Week 9 (early): Final full exam → brief review of weak pockets only → stop heavy study 24 hours before test.
- First pass: answer easy/medium in ~60–70% of allotted time.Flag long scenarios; return with remaining time.Read the last sentence first on long stems. Then scan for key constraints.
- Night before and day of:
- Close the books. Stretch, hydrate, sleep.
- Pack: valid ID, testing confirmation, water/snack if allowed, quiet setup if online proctored.
- Quick warm‑up: 5–8 lightweight questions to get in flow. No cramming.
- Weekly full practice exams; focus on timing and rationale analysis.Light review, sleep, then test.Exam simulation rhythm:
Tips to keep you moving (optional but powerful):
- Keep “Why I picked this cert” on the first page of your notes. Motivation beats friction.
- Share one lab screenshot or diagram on LinkedIn in Week 6 or Week 8. Visibility helps.
- If you slip a week, don’t double everything. Resume the plan; add one extra quiz block only.
Deliverables by Day 90 (so you can prove it):
- One passed entry‑level cybersecurity certification (or a scheduled retake with improved scores).
- 2 micro‑labs documented with screenshots/logs.
- 2 clean diagrams re‑drawn from memory.
- A short reflection: what you’ll do next quarter (one intermediate cert or deeper labs).
FAQs
Quick hits you can act on. Skim now, bookmark for later.
| Question | Short answer |
| Do I need a degree to start? | No. A degree helps later. For entry roles, focused certs + a small portfolio can land interviews. Show proof: labs, notes, and 1–2 diagrams. |
| Which cert should I start with? | Brand new: ITF+ or SC-900 → then ISC2 CC or Security+. Have IT experience? Start with Security+. |
| Is Security+ still the baseline in 2025? | Yes. It’s the most requested entry-level security cert in job postings. It validates risk, network/app sec, IR, and governance. |
| How many certs per year is reasonable? | Working full-time? One per quarter max. Two if you can sustain study and labs without burnout. |
| Are practice exams necessary? | Yes. They train timing and question style. Use reputable sets with full explanations mapped to current blueprints. Avoid dumps. |
| Vendor-neutral or vendor-specific first? | Start neutral for fundamentals (Security+, ISC2 CC). Add vendor certs that match your stack (Microsoft, AWS, Cisco, Palo Alto, Splunk). |
| When should I think about CISSP or CCSP? | After hands-on work and at least one intermediate cert. No experience yet? Take CISSP as an Associate of ISC2, then accrue experience. |
| How long to land a first security role? | Typical: 6–12 months with steady study (5–8 hrs/week), one entry cert, and a small portfolio. Faster with prior IT or a strong network. |
| Do I need A+ or Network+ before Security+? | Not required. If you already grasp basic networking/OS, go straight to Security+. Use the official objectives as a self-check. |
| Are bootcamps worth it? | Sometimes. Vet outcomes: placement rate, instructor creds, hands-on labs, and employer links. You can DIY with a lower budget if disciplined. |
| What about DoD 8570/8140 requirements? | Many federal/contractor roles require specific certs (Security+, CySA+, CASP+, CISSP). Check the target role category (IAT/IAM/IASAE). |
| Online vs test center? | Both work. Online is convenient but strict (webcam, room scan, no notes). Test centers reduce tech risk. Pick what keeps you calm. |
| What if I fail? | It happens. Review your score report by domain, redo labs, and schedule a retake within 2–4 weeks. Know vendor retake rules and fees. |
| How do I build labs on a budget? | Use free tiers (Azure, AWS), local VMs (VirtualBox), and community tools (Sigma, Zeek, Wireshark). Keep labs small and repeatable. |
| How do I showcase certs and skills? | Resume: top third. LinkedIn: “Featured” with lab screenshots. GitHub: sanitized artifacts + readme. One 2–3 minute story per project. |
Fast tips
- Book the exam early. A date forces momentum and weekly habits.
- One primary resource + one practice set. Depth beats course-hoarding.
- Mirror the blueprint. Your notes and labs should trace the official objectives line by line.
- Use legit materials. Full-rationale practice exams only. No dumps.
- Keep a CE/CPE log. Track renewals from day one; it saves money and stress.
Final steps: lock your plan
- Pick your target role and one certification aligned to it.
- Quick filter: What jobs are local or remote in your market? Which tech stack shows up most (Microsoft, AWS, Cisco, Splunk, Okta)?
- Fit check: Do you like operations (SOC/DFIR), building (cloud/AppSec/IAM), or frameworks (GRC/audit)?
- Decision rule: one role, one cert. No hedging.
- Examples: SOC → Security+ or Cisco CyberOps; Cloud Security → AZ-500; GRC → Security+ then CISA; Pentest → eJPT or PenTest+; IAM → SC-900 then Entra/Okta.
- Book the exam 8–10 weeks out.
- Put it on the calendar now. Work backward to set weekly blocks.
- Protect 2–3 focused sessions per week (60–90 minutes). Add a weekly lab slot.
- Leave a 1–2 week buffer for review and full-length practice exams.
- Pro tip: morning test times reduce fatigue. If available, buy a retake-protected voucher.
- Choose one learning resource and one practice exam set with full rationales.
- Learning resource should map 1:1 to the official exam objectives and include diagrams, brief labs, and chapter quizzes.
- Practice exams must be current to the exam version and explain why wrong answers are wrong.
- Pair ideas:
- Official vendor course + a concise third‑party guide.
- Official blueprint + CertEmpire’s updated practice sets.
- Keep it lean: one primary, one practice set. Add a cheat sheet later if needed.
- Build small, repeatable labs and a tiny portfolio as you study.
- Make labs atomic: 20–40 minutes each, reproducible, with a clear outcome.
- Capture evidence: screenshots, commands, logs, and a 3–5 sentence summary.
- Three easy templates:
- Network: “Block-and-verify” a port with a firewall rule; validate with nmap.
- Cloud: Create a least-privilege policy; test deny/allow; log the event.
- SOC: Ingest a small log source (Sysmon/Sentinel/Splunk), write one detection, test it.
- Portfolio structure:
- Repo: /labs/{lab-name}/readme.md, /images/, /artifacts/.
- Include one identity flow diagram and one network segmentation diagram.
- Sanitize anything sensitive.
- After you pass, apply immediately and publish one short project write-up.
- Same day:
- Update resume, LinkedIn headline, and skills. Add the cert and 2 lab bullets.
- Post a 6–8 sentence summary: what you learned, one diagram, one lab link.
- Next 2 weeks:
- Apply to 5–10 role-aligned jobs per week.
- Message a hiring manager or team lead with a short note + portfolio link.
- Offer a 10‑minute screen-share to walk through a lab or detection.
- Same day:
Quick picks to lock fast
| Target role | Starter cert | Primary resource idea | Practice exams (rationales) | 2 lab ideas | Exam window |
| SOC Analyst / Blue Team | Security+ or Cisco CyberOps | Official blueprint + one structured course | CertEmpire Security+ / CyberOps sets | Parse Windows logs; write a basic correlation rule | 8–10 weeks |
| Cloud Security Engineer (Azure) | AZ-500 | Microsoft Learn path + one deep-dive course | CertEmpire AZ‑500 practice | IAM policy with least privilege; NSG + logging to Sentinel | 8–12 weeks |
| Penetration Tester | eJPT or PenTest+ | Hands-on labs + exam objective map | CertEmpire PenTest+ practice | Recon + report on a legal target; web vuln lab (OWASP Juice Shop) | 8–12 weeks |
| GRC Analyst / IT Auditor | Security+ | Official objectives + concise governance guide | CertEmpire Security+ practice | Map NIST CSF controls; build a mini risk register | 6–9 weeks |
| IAM Engineer | SC-900 → Entra/Okta | Vendor docs + one role-based course | CertEmpire SC‑900 practice | Set SSO + conditional access; automate user lifecycle with SCIM concept | 6–10 weeks |
| DFIR / Threat Hunter | Security+ or CyberOps | IR-focused course + lab time | CertEmpire CyberOps practice | Collect Sysmon; build a timeline from artifacts | 8–10 weeks |
| Application Security / DevSecOps | Security+ (then OSWA/OSWE) | Secure coding + cloud security modules | CertEmpire Security+ practice | Add SAST to CI; enforce IaC policy with a test repo | 8–12 weeks |
Mini-commit checklist
- Role chosen and cert selected
- Exam date scheduled
- One primary resource + one practice set acquired
- Weekly study blocks and lab slots on calendar
- Portfolio repo created; first lab drafted
You now have a locked plan. Keep it simple, execute weekly, and ship small wins.