IBM C1000-162 Dumps.pdf
Q: 1
How does a Device Support Module (DSM) function?
Options
Q: 2
On the Offenses tab, which column explains the cause of the offense?
Options
Q: 3
A mapping of a username to a user’s manager can be stored in a Reference Table and output in a
search or a report.
Which mechanism could be used to do this?
Options
Q: 4
Which two (2) types of data can be displayed by default in the Application Overview dashboard?
Options
Q: 5
What Is the result of the following AQL statement?
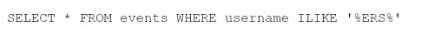
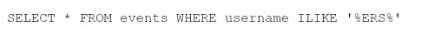
Options
Q: 6
DRAG DROP Select all that apply What is the sequence to create and save a new search called "Offense Data" that shows all the CRE events that are associated with offenses? 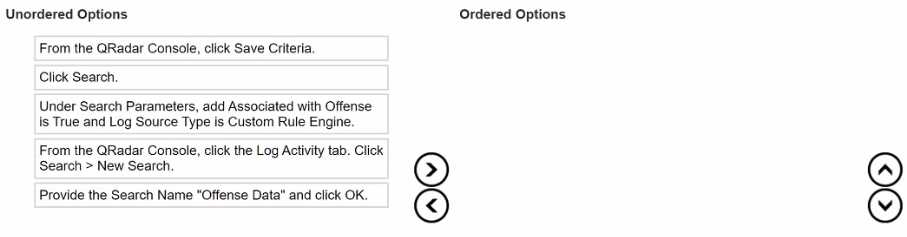
Drag & Drop
Q: 7
HOTSPOT
New vulnerability scanners are deployed in the company's infrastructure and generate a high
number of offenses. Which function in the Use Case Manager app does an analyst use to update the
list of vulnerability scanners?


Your Answer
Q: 8
Offense chaining is based on which field that is specified in the rule?
Options
Q: 9
When examining lime fields on Event Information, which one represents the time QRadar received
the raw event?
Options
Q: 10
What is the effect of toggling the Global/Local option to Global in a Custom Rule?
Options
Question 1 of 10

