GIAC GCCC
Q: 1
An organization is implementing an application software security control their custom-written code
that provides web—based database access to sales partners. Which action will help mitigate the risk
of the application being compromised?
Options
Q: 2
How does an organization's hardware inventory support the control for secure configurations?
Options
Q: 3
A security incident investigation identified the following modified version of a legitimate system file
on a compromised client:
C:\Windows\System32\winxml.dll Addition Jan. 16, 2014 4:53:11 PM
The infection vector was determined to be a vulnerable browser plug-in installed by the user. Which
of the organization’s CIS Controls failed?
Options
Q: 4
Based on the data shown below.
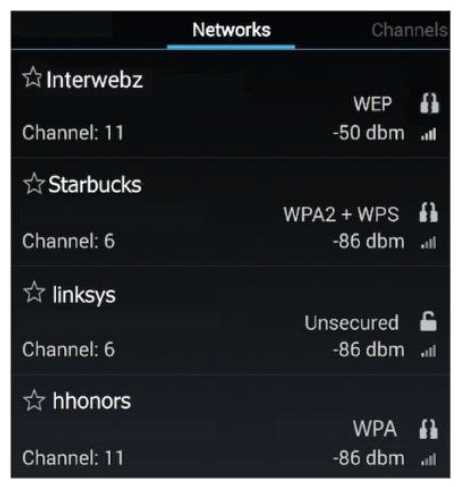 Which wireless access point has the manufacturer default settings still in place?
Which wireless access point has the manufacturer default settings still in place?
 Which wireless access point has the manufacturer default settings still in place?
Which wireless access point has the manufacturer default settings still in place?Options
Q: 5
Review the below results of an audit on a server. Based on these results, which document would you
recommend be reviewed for training or updates?
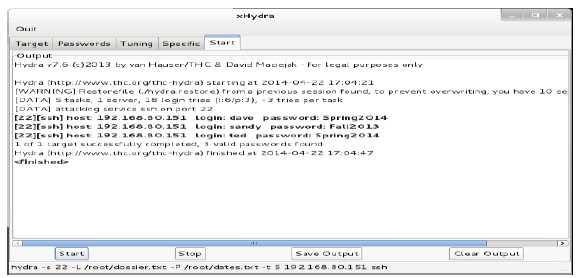

Options
Q: 6
Acme Corporation is doing a core evaluation of its centralized logging capabilities. Which of the
following scenarios indicates a failure in more than one CIS Control?
Options
Q: 7
Which activity increases the risk of a malware infection?
Options
Q: 8
Which of the following items would be used reactively for incident response?
Options
Q: 9
As part of an effort to implement a control on E-mail and Web Protections, an organization is
monitoring their webserver traffic. Which event should they receive an alert on?
Options
Q: 10
An Internet retailer's database was recently exploited by a foreign criminal organization via a remote
attack. The initial exploit resulted in immediate root-level access. What could have been done to
prevent this level of access being given to the intruder upon successful exploitation?
Options
Question 1 of 10

