GIAC GCFA
Q: 1
In Linux, which of the following files describes the processes that are started up during boot up?
Options
Q: 2
You work as a Network Administrator for uCertify Inc. You want to edit the MSDOS .SYS file, in your
computer, from the DOS prompt. You are unable to find the file. What is the most likely cause?
Options
Q: 3
John works as a professional Ethical Hacker. He has been assigned the project of testing the security
of www.we-are-secure.com. He receives the following e-mail:
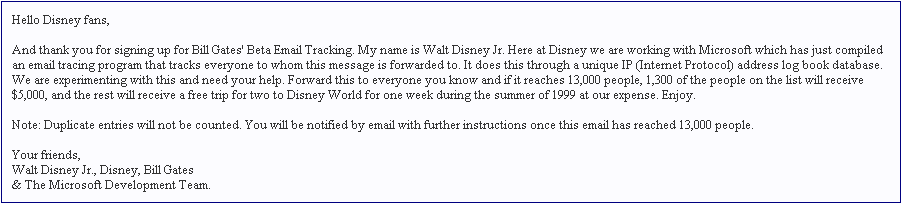 The e-mail that John has received is an example of __________.
The e-mail that John has received is an example of __________.
 The e-mail that John has received is an example of __________.
The e-mail that John has received is an example of __________.Options
Q: 4
Mark works as a security manager for SofTech Inc. He is using a technique for monitoring what the
employees are doing with corporate resources. Which of the following techniques is being used by
Mark to gather evidence of an ongoing computer crime if a member of the staff is e-mailing
company's secrets to an opponent?
Options
Q: 5
Adam works as a Security Analyst for Umbrella Inc. He suspects that a virus exists in the network of
the company. He scanned the client system with latest signature-based anti-virus, but no productive
results have been obtained. Adam suspects that a polymorphic virus exists in the network. Which of
the following statements are true about the polymorphic virus?
Each correct answer represents a complete solution. Choose all that apply.
Options
Q: 6
Which of the following enables an inventor to legally enforce his right to exclude others from using
his invention?
Options
Q: 7
John works as a professional Ethical Hacker. He has been assigned a project to test the security of
www.we-are-secure.com. He wants to test the effect of a virus on the We-are-secure server. He
injects the virus on the server and, as a result, the server becomes infected with the virus even
though an established antivirus program is installed on the server. Which of the following do you
think are the reasons why the antivirus installed on the server did not detect the virus injected by
John?
Each correct answer represents a complete solution. Choose all that apply.
Options
Q: 8
Which of the following type of files is NOT deleted by Disk Cleanup program of Windows XP?
Options
Q: 9
You work as a Network Administrator for Net World International. You want to configure a Windows
2000 computer to dual boot with Windows 98. The hard disk drive of the computer will be
configured as a single partition drive. Which of the following file systems will you use to accomplish
this?
Options
Q: 10
Which of the following tools is used to modify registry permissions in Windows?
Options
Question 1 of 10

