GIAC GPYC
Q: 1
During a password guessing attack, which HTTP request method would a Python program most
commonly call to submit a usemame and password to a target website?
Options
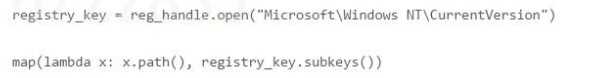
Q: 2
What would be the result of the following code in Python?

Options
Q: 3
What is the output when the following commands are typed in Python interactive mode?
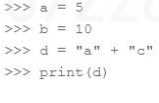
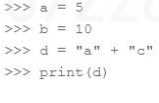
Options
Q: 4
A log file is stored in variable "a". The file has the following format for each log entry, in order, stored
in big endian:
Field 1: 2-byte integer
Field 2: 2-byte integer
Field 3: 4-byte string
Which of the following would unpack a line from the log file into the proper fields?
Options
Q: 5
Review the following Python 3 code.


Options
Q: 6
Review the following code:
 What is the output of this code?
What is the output of this code?
 What is the output of this code?
What is the output of this code?Options
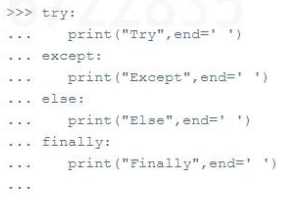
Q: 7
What is the output of the following commands typed in the Python Interactive shell?

Options
Q: 8
A multi-byte character encoded with UTF-8 has the first byte 11861101. What will the next byte
begin with?
Options
Q: 9
What is the output of the following program when executed with the Python Interpreter?
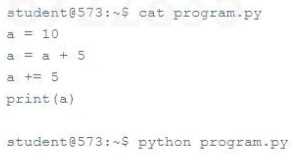

Options
Q: 10
What is the output of the following line of code typed into a Python interactive session?
>>> print ( int ("1111", 2) )
Options
Question 1 of 10

