Palo Alto XSIAM ANALYST
Q: 1
Which interval is the duration of time before an analytics detector can raise an alert?
Options
Q: 2
Based on the image below, which two additional steps should a SOC analyst take to secure the
endpoint? (Choose two.)
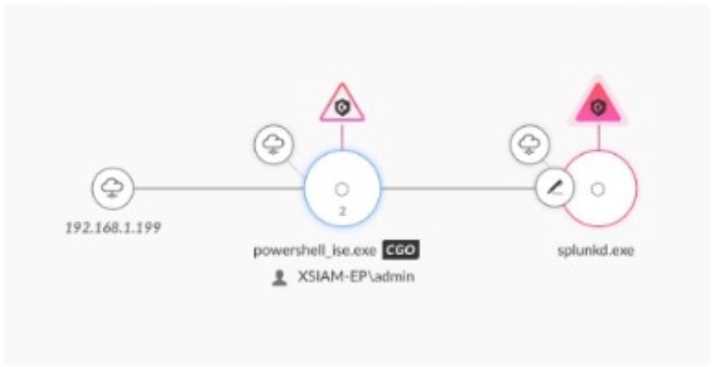

Options
Q: 3
During an investigation of an alert with a completed playbook, it is determined that no indicators
exist from the email "[email protected]" in the Key Assets & Artifacts tab of the parent incident.
Which command will determine if Cortex XSIAM has been configured to extract indicators as
expected?
Options
Q: 4
Why would an analyst schedule an XQL query?
Options
Q: 5
When a sub-playbook loops, which task tab will allow an analyst to determine what data the sub-
playbook used in each iteration of the loop?
Options
Q: 6
An analyst is responding to a critical incident involving a potential ransomware attack. The analyst
immediately initiates full isolation on the compromised endpoint using Cortex XSIAM to prevent the
malware from spreading across the network. However, the analyst now needs to collect additional
forensic evidence from the isolated machine, including memory dumps and disk images without
reconnecting it to the network. Which action will allow the analyst to collect the required forensic
evidence while ensuring the endpoint remains fully isolated?
Options
Q: 7
While investigating an alert, an analyst notices that a URL indicator has a related alert from a
previous incident. The related alert has the same URL but it resolved to a different IP address.
Which combination of two actions should the analyst take to resolve this issue? (Choose two.)
Options
Q: 8
An incident in Cortex XSIAM contains the following series of alerts:
10:24:17 AM - Informational Severity - XDR Analytics BIOC - Rare process execution in organization
10:24:18 AM - Low Severity - XDR BIOC - Suspicious AMSI DLL load location
10:24:20 AM - Medium Severity - XDR Agent - WildFire Malware
11:57:04 AM - High Severity - Correlation - Suspicious admin account creation
Which alert was responsible for the creation of the incident?
Options
Q: 9
Which attributes can be used as featured fields?
Options
Q: 10
Two security analysts are collaborating on complex but similar incidents. The first analyst merges the
two incidents into one for easier management. The other analyst immediately discovers that the
custom incident field values relevant to the investigation are missing.
How can the team retrieve the missing details?
Options
Question 1 of 10

