Get Ready for Success in the HUAWEI H12-811_V1.0 Exam with Trusted 2026 Preparation Materials
Cert Empire offers verified and up-to-date HUAWEI H12-811_V1.0 exam questions designed for cybersecurity professionals who want to validate their penetration testing and ethical hacking skills. Our study materials reflect real exam environments and the most recent H12-811_V1.0 objectives. To simplify your preparation, we’ve made part of our HUAWEI H12-811_V1.0 content free for all learners. You can practice anytime with the H12-811_V1.0 Practice Test to strengthen your confidence before the real test.
GIAC GPEN
Q: 1
Which of the following tools can be used to find a username from a SID?
Options
Q: 2
Which of the following tools uses exploits to break into remote operating systems?
Options
Q: 3
You are using the Nmap Scripting Engine and want detailed output of the script as it runs. Which
option do you include in the command string?
Options
Q: 4
John works as a Professional Penetration Tester. He has been assigned a project to test the Website
security of www.we-are-secure Inc. On the We-are-secure Website login page, he enters ='or''=' as a
username and successfully logs on to the user page of the Web site. Now, John asks the we-are-
secure Inc. to improve the login page PHP script. Which of the following suggestions can John give to
improve the security of the we-are-secure Website login page from the SQL injection attack?
Options
Q: 5
If the privacy bit is set in the 802.11 header, what does it indicate?
Options
Q: 6
Which type of Cross-Sire Scripting (XSS> vulnerability is hardest for automated testing tools to detect,
and for what reason?
Options
Q: 7
Which of the following tasks can be performed by using netcat utility?
Each correct answer represents a complete solution. Choose all that apply.
Options
Q: 8
192.168.116.9 Is an IP address forvvww.scanned-server.com. Why are the results from the two scans,
shown below, different?
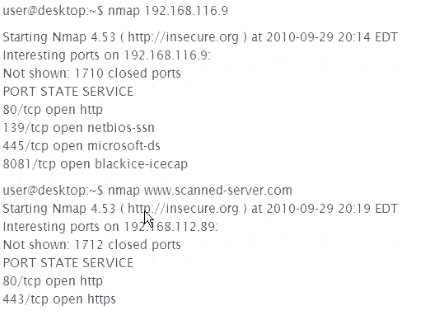

Options
Q: 9
Given the following Scapy information, how is default Layer 2 information derived?
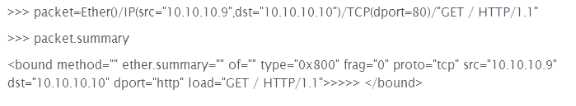

Options
Q: 10
How can a non-privileged user on a Unix system determine if shadow passwords are being used?
Options
Question 1 of 10

