Microsoft SC-401 Dumps.pdf
DRAG DROP You have a Microsoft 365 E5 subscription that has data loss prevention (DLP) implemented. You need to create a custom sensitive info type. The solution must meet the following requirements: ● Match product serial numbers that contain a 10-character alphanumeric string. ● Ensure that the abbreviation of SN appears within six characters of each product serial number. ● Exclude a test serial number of 1111111111 from a match. Which pattern settings should you configure for each requirement? To answer, drag the appropriate settings to the correct requirements. Each setting may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. 
DRAG DROP You have a Microsoft 365 tenant. A new regulatory requirement states that all documents containing a patent ID be labeled, retained for 10 years, and then deleted. The policy used to apply the retention settings must never be disabled or deleted by anyone. You need to implement the regulatory requirement. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. 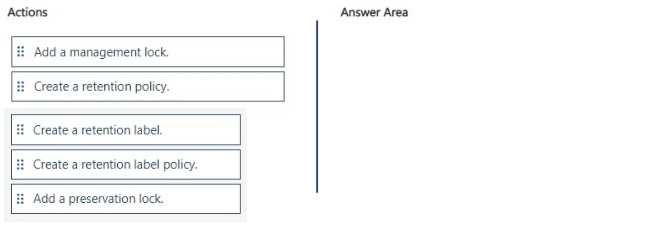
DRAG DROP You need to create a trainable classifier that can be used as a condition in an auto-apply retention label policy. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. 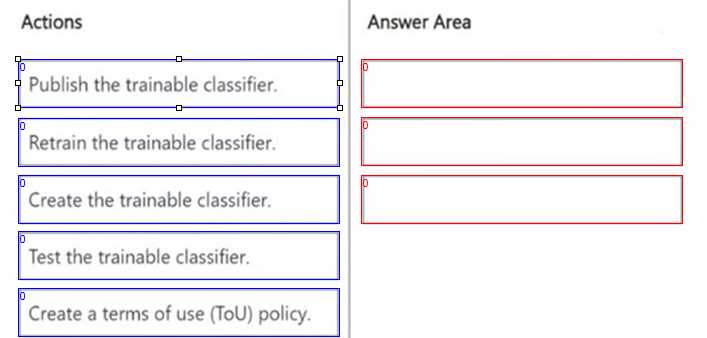
DRAG DROP You have a Microsoft 365 E5 subscription that uses Microsoft Purview insider risk management and contains three users named User1, User2, and User3. All insider risk management policies have adaptive protection enabled and the default conditions for insider risk levels configured. The users perform the following activities, which trigger insider risk policy alerts: User1 performs at least one data exfiltration activity that results in a high severity risk score. User2 performs at least three risky user activities within seven days, that each results in a high severity risk score. User3 performs at least bwo data exfiltration activities within seven days, that each results in a high severity risk score. Which insider risk level is assigned to each user? To answer, drag the appropriate levels to the correct users. Each level may be used once, more than once, or not at all. You may need to drag the split bar between panes or seroll to view content. NOTE: Each correct selection is worth one point. 

