300-215.pdf
Q: 1
Refer to the exhibit.
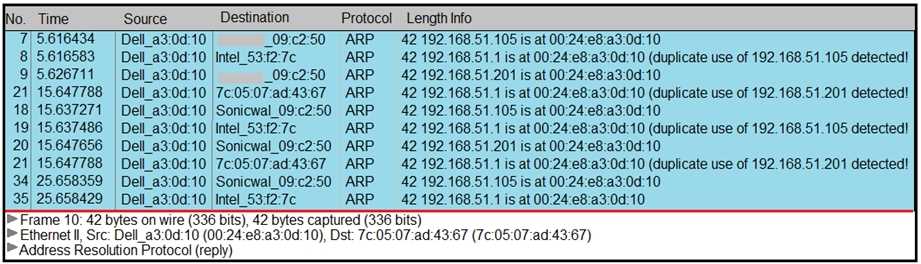 A security analyst notices unusual connections while monitoring traffic. What is the attack vector,
and which action should be taken to prevent this type of event?
A security analyst notices unusual connections while monitoring traffic. What is the attack vector,
and which action should be taken to prevent this type of event?
 A security analyst notices unusual connections while monitoring traffic. What is the attack vector,
and which action should be taken to prevent this type of event?
A security analyst notices unusual connections while monitoring traffic. What is the attack vector,
and which action should be taken to prevent this type of event?Options
Q: 2
A security team is notified from a Cisco ESA solution that an employee received an advertising email
with an attached .pdf extension file. The employee opened the attachment, which appeared to be an
empty document. The security analyst cannot identify clear signs of compromise but reviews running
processes and determines that PowerShell.exe was spawned by CMD.exe with a grandparent
AcroRd32.exe process. Which two actions should be taken to resolve this issue? (Choose two.)
Options
Q: 3
An engineer received a report of a suspicious email from an employee. The employee had already
opened the attachment, which was an empty Word document. The engineer cannot identify any
clear signs of compromise but while reviewing running processes, observes that PowerShell.exe was
spawned by cmd.exe with a grandparent winword.exe process. What is the recommended action the
engineer should take?
Options
Q: 4
A security team is discussing lessons learned and suggesting process changes after a security breach
incident. During the incident, members of the security team failed to report the abnormal system
activity due to a high project workload. Additionally, when the incident was identified, the response
took six hours due to management being unavailable to provide the approvals needed. Which two
steps will prevent these issues from occurring in the future? (Choose two.)
Options
Q: 5
An employee receives an email from a “trusted” person containing a hyperlink that is malvertising.
The employee clicks the link and the malware downloads. An information analyst observes an alert
at the SIEM and engages the cybersecurity team to conduct an analysis of this incident in accordance
with the incident response plan. Which event detail should be included in this root cause analysis?
Options
Q: 6
What is the steganography anti-forensics technique?
Options
Q: 7
An “unknown error code” is appearing on an ESXi host during authentication. An engineer checks the
authentication logs but is unable to identify the issue. Analysis of the vCenter agent logs shows no
connectivity errors. What is the next log file the engineer should check to continue troubleshooting
this error?
Options
Q: 8
Refer to the exhibit.
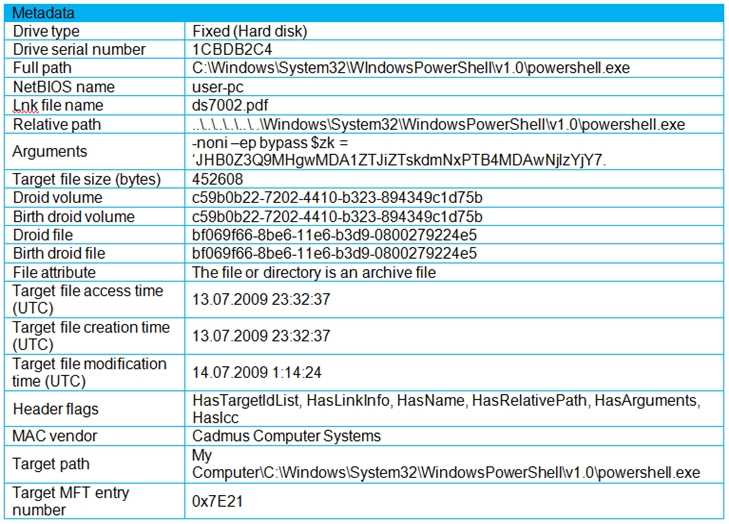 An engineer is analyzing a .LNK (shortcut) file recently received as an email attachment and blocked
by email security as suspicious. What is the next step an engineer should take?
An engineer is analyzing a .LNK (shortcut) file recently received as an email attachment and blocked
by email security as suspicious. What is the next step an engineer should take?
 An engineer is analyzing a .LNK (shortcut) file recently received as an email attachment and blocked
by email security as suspicious. What is the next step an engineer should take?
An engineer is analyzing a .LNK (shortcut) file recently received as an email attachment and blocked
by email security as suspicious. What is the next step an engineer should take?Options
Q: 9
Refer to the exhibit.
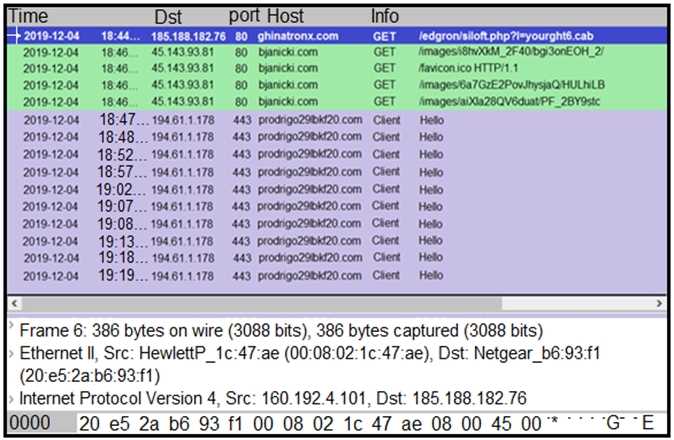 A network engineer is analyzing a Wireshark file to determine the HTTP request that caused the
initial Ursnif banking Trojan binary to download. Which filter did the engineer apply to sort the
Wireshark traffic logs?
A network engineer is analyzing a Wireshark file to determine the HTTP request that caused the
initial Ursnif banking Trojan binary to download. Which filter did the engineer apply to sort the
Wireshark traffic logs?
 A network engineer is analyzing a Wireshark file to determine the HTTP request that caused the
initial Ursnif banking Trojan binary to download. Which filter did the engineer apply to sort the
Wireshark traffic logs?
A network engineer is analyzing a Wireshark file to determine the HTTP request that caused the
initial Ursnif banking Trojan binary to download. Which filter did the engineer apply to sort the
Wireshark traffic logs?Options
Q: 10
Refer to the exhibit.
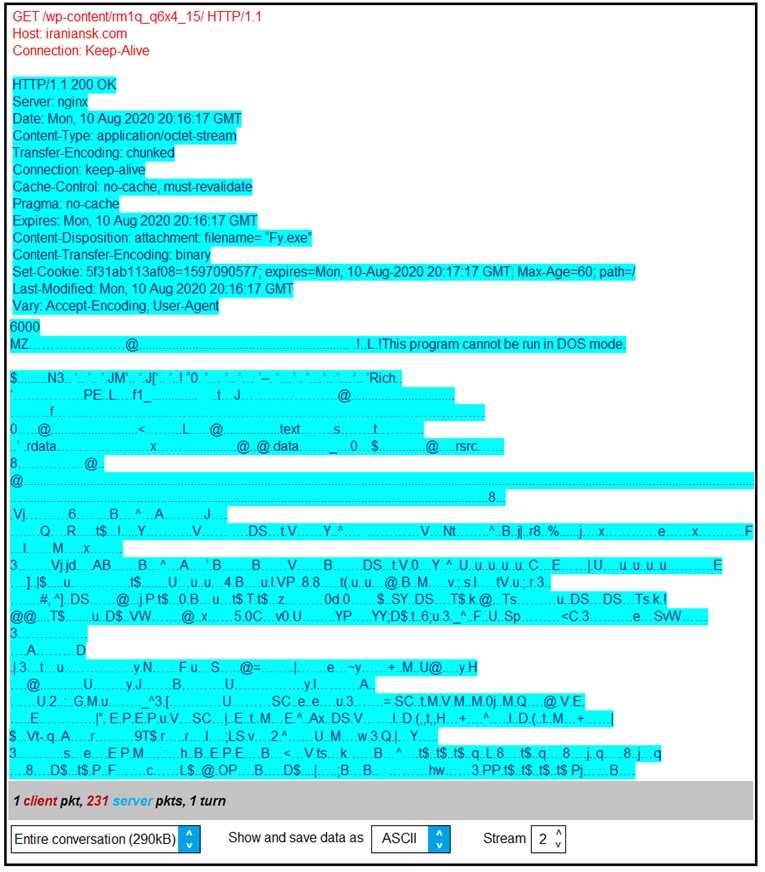 According to the Wireshark output, what are two indicators of compromise for detecting an Emotet
malware download? (Choose two.)
According to the Wireshark output, what are two indicators of compromise for detecting an Emotet
malware download? (Choose two.)
 According to the Wireshark output, what are two indicators of compromise for detecting an Emotet
malware download? (Choose two.)
According to the Wireshark output, what are two indicators of compromise for detecting an Emotet
malware download? (Choose two.)Options
Question 1 of 10

