Prepare effectively for the Google Security-Operations-Engineer exam with updated 2026 resources and genuine exam questions.
Cert Empire provides refreshed Google Security-Operations-Engineer exam questions aimed at professionals proving their security operations and monitoring expertise. These materials follow official objectives and mimic the real test setup. To make studying simple, part of the Google Security-Operations-Engineer content is free. You can use the Security-Operations-Engineer Practice Test anytime to build confidence before taking the real exam.
GIAC GPEN
Q: 1
Which of the following tools can be used to find a username from a SID?
Options
Q: 2
Which of the following tools uses exploits to break into remote operating systems?
Options
Q: 3
You are using the Nmap Scripting Engine and want detailed output of the script as it runs. Which
option do you include in the command string?
Options
Q: 4
John works as a Professional Penetration Tester. He has been assigned a project to test the Website
security of www.we-are-secure Inc. On the We-are-secure Website login page, he enters ='or''=' as a
username and successfully logs on to the user page of the Web site. Now, John asks the we-are-
secure Inc. to improve the login page PHP script. Which of the following suggestions can John give to
improve the security of the we-are-secure Website login page from the SQL injection attack?
Options
Q: 5
If the privacy bit is set in the 802.11 header, what does it indicate?
Options
Q: 6
Which type of Cross-Sire Scripting (XSS> vulnerability is hardest for automated testing tools to detect,
and for what reason?
Options
Q: 7
Which of the following tasks can be performed by using netcat utility?
Each correct answer represents a complete solution. Choose all that apply.
Options
Q: 8
192.168.116.9 Is an IP address forvvww.scanned-server.com. Why are the results from the two scans,
shown below, different?
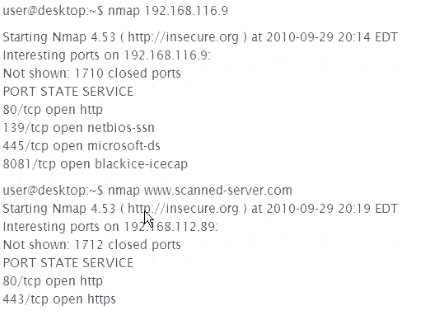

Options
Q: 9
Given the following Scapy information, how is default Layer 2 information derived?
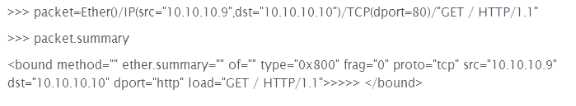

Options
Q: 10
How can a non-privileged user on a Unix system determine if shadow passwords are being used?
Options
Question 1 of 10

