AZ-500.pdf
DRAG DROP You are implementing conditional access policies. You must evaluate the existing Azure Active Directory (Azure AD) risk events and risk levels to configure and implement the policies. You need to identify the risk level of the following risk events: Users with leaked credentials Impossible travel to atypical locations Sign ins from IP addresses with suspicious activity Which level should you identify for each risk event? To answer, drag the appropriate levels to the correct risk events. Each level may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. 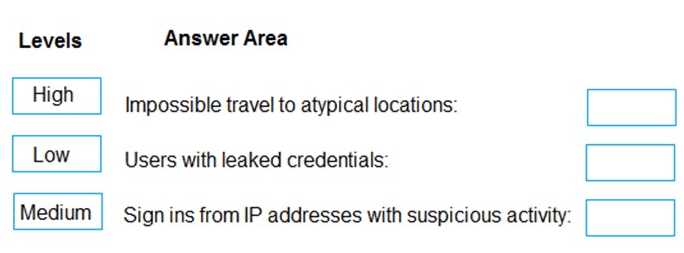
DRAG DROP You have an Azure Sentinel workspace that has an Azure Active Directory (Azure AD) data connector. You are threat hunting suspicious traffic from a specific IP address. You need to annotate an intermediate event stored in the workspace and be able to reference the IP address when navigating through the investigation graph. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. 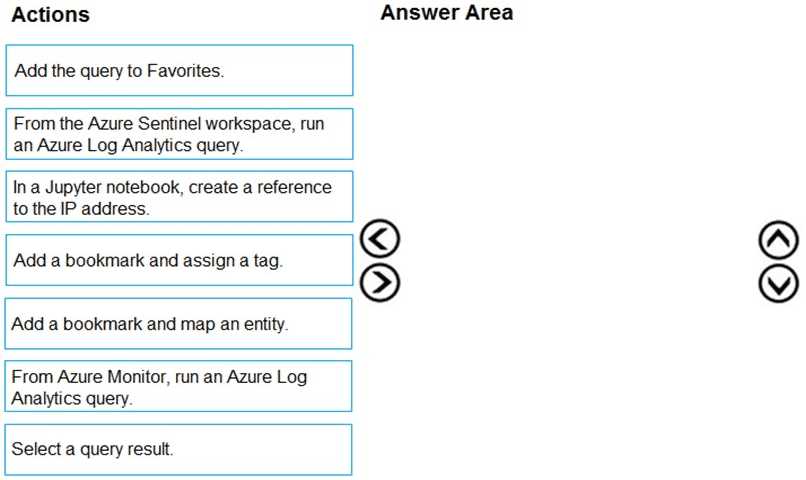
You have an Azure subscription that contains an Azure App Services web app named WebApp1. WebApp1 is accessed by users in multiple Azure regions. You need to secure access to WebApp1. The solution must meet the following requirements:
* Protect against common web vulnerabilities.
* Optimize the routing of traffic from different regions.
What should you use?
HOTSPOT You have an Azure subscription that contains the Azure Firewall policies shown in the following table. 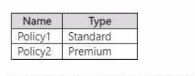 The subscription contains the firewalls shown in the following table.
The subscription contains the firewalls shown in the following table. 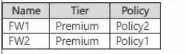 The subscription contains the virtual networks shown in the following table.
The subscription contains the virtual networks shown in the following table. 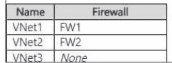 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. 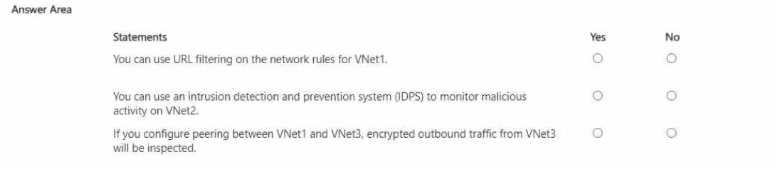
You have an Azure AD tenant. You plan to implement an authentication solution to meet the following requirements:
• Require number matching.
• Display the geographical location when signing in.
Which authentication method should you include in the solution?
HOTSPOT You have an Azure subscription that contains a storage account named storage1 and several virtual machines. The storage account and virtual machines are in the same Azure region. The network configurations of the virtual machines are shown in the following table. 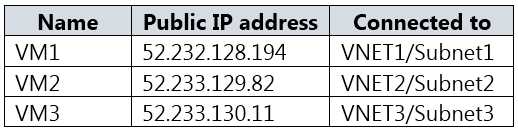 The virtual network subnets have service endpoints defined as shown in the following table.
The virtual network subnets have service endpoints defined as shown in the following table. 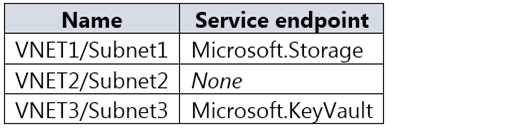 You configure the following Firewall and virtual networks settings for storage1: Allow access from: Selected networks Virtual networks: VNET3\Subnet3 Firewall – Address range: 52.233.129.0/24 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
You configure the following Firewall and virtual networks settings for storage1: Allow access from: Selected networks Virtual networks: VNET3\Subnet3 Firewall – Address range: 52.233.129.0/24 For each of the following statements, select Yes if the statement is true. Otherwise, select No. 
DRAG DROP Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure Subscription named Sub1. Sub1 contains an Azure virtual machine named VM1 that runs Windows Server 2016. You need to encrypt VM1 disks by using Azure Disk Encryption. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. 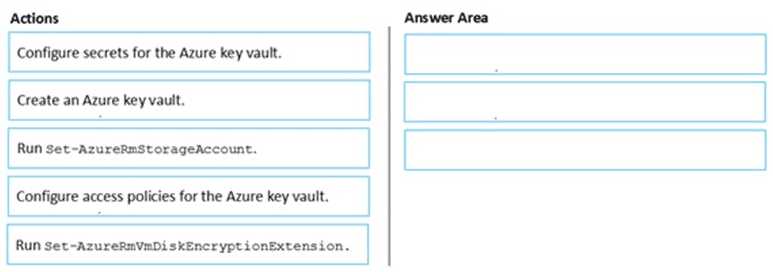
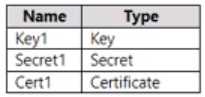 Which resources support the creation of a rotation policy?
Which resources support the creation of a rotation policy?DRAG DROP You create an Azure subscription. You need to ensure that you can use Azure Active Directory (Azure AD) Privileged Identity Management (PIM) to secure Azure AD roles. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. 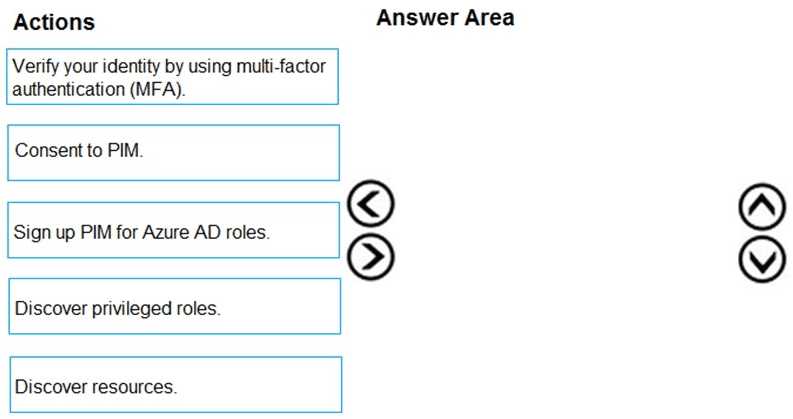
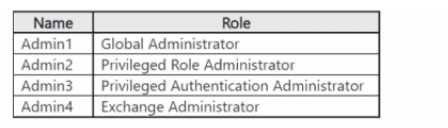 Which accounts will be listed as assigned to highly privileged roles on the Azure AD insights tab in
the Entra Permissions Management portal?
Which accounts will be listed as assigned to highly privileged roles on the Azure AD insights tab in
the Entra Permissions Management portal?
