300-410.pdf
Q: 1
Refer to the exhibit. SIMULATION 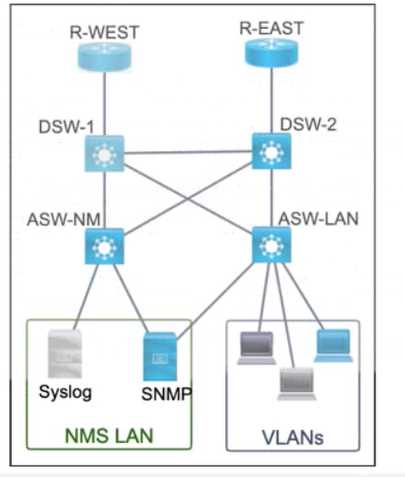

Your Answer
Q: 2
DRAG DROP Drag and drop the descriptions from the left onto the corresponding MPLS components on the right. 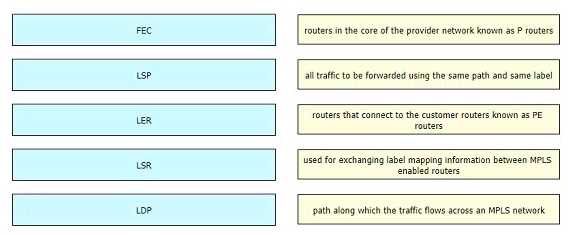
Drag & Drop
Q: 3
DRAG DROP Drag and drop the packet types from the left onto the correct descriptions on the right. 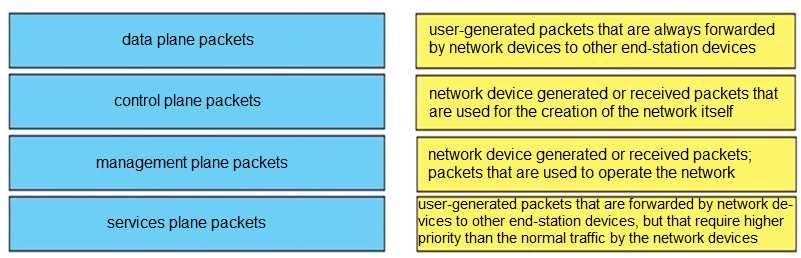
Drag & Drop
Q: 4
What is the minimum time gap required by the local system before putting a BFD control packet on
the wire?
Options
Q: 5
Which IPv6 feature enables a device to reject traffic when it is originated from an address that is not
stored in the device binding table?
Options
Q: 6
A network administrator successfully established a DMVPN tunnel with one hub and two spokes
using EIGRP. One of the requirements was to enable spoke-to-spoke tunnels through the hub router
using EIGRP. Which configuration command must the engineer configure to meet the requirement?
Options
Q: 7
SIMULATION 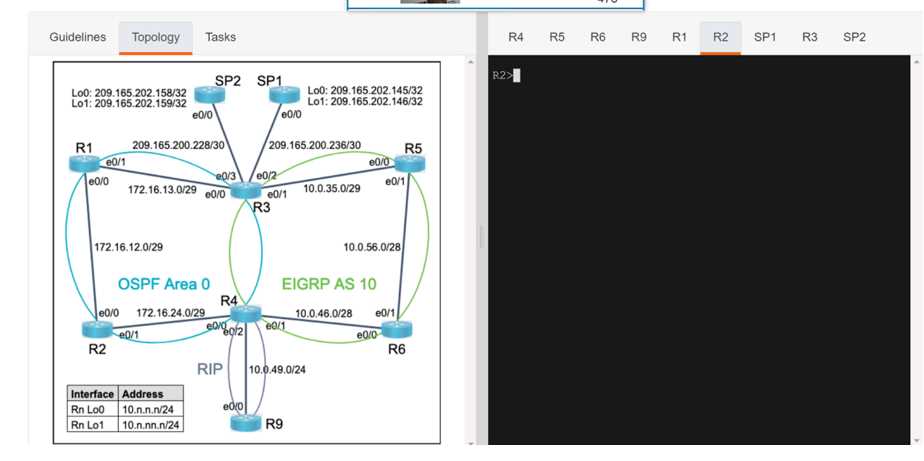
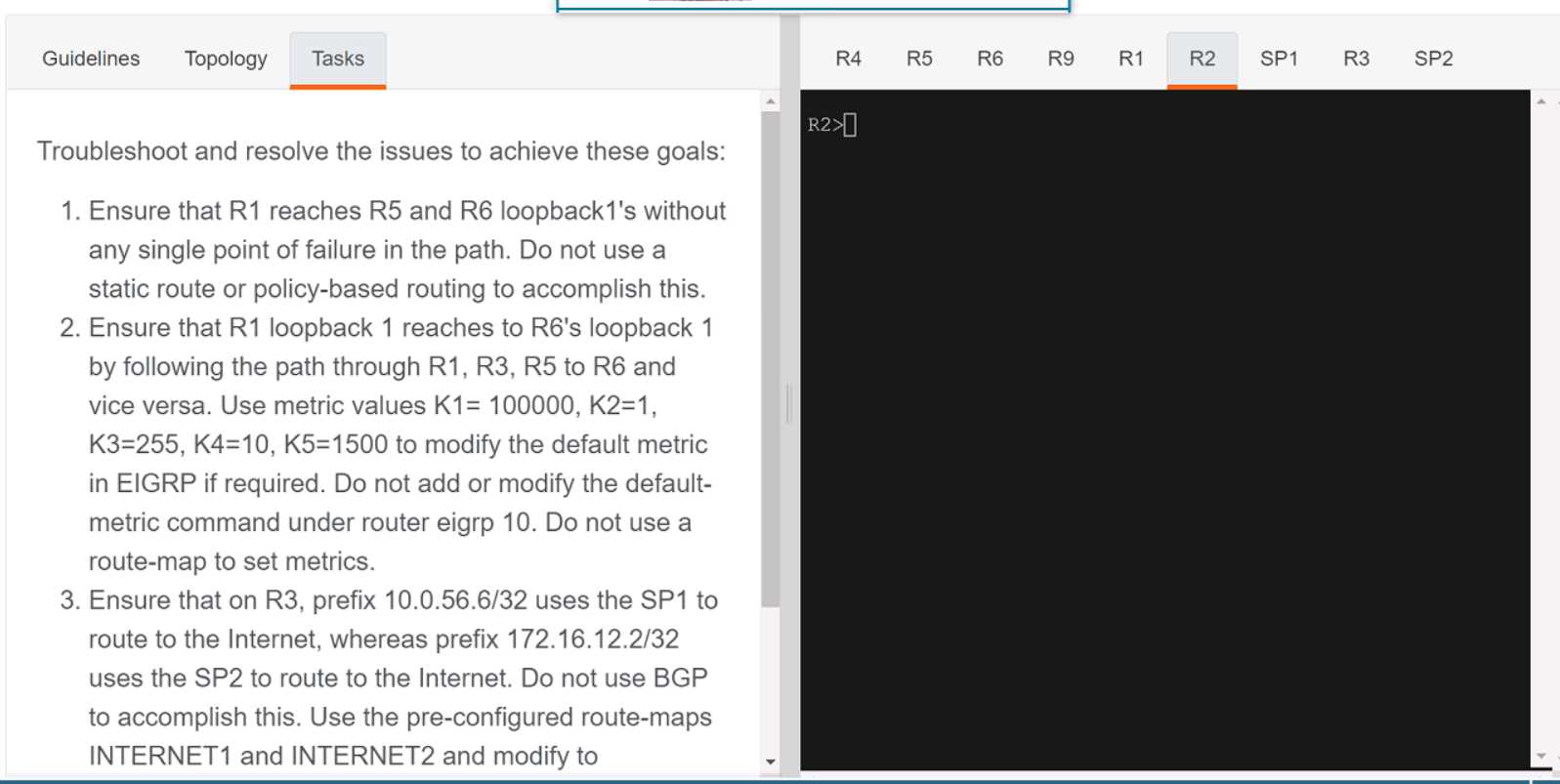
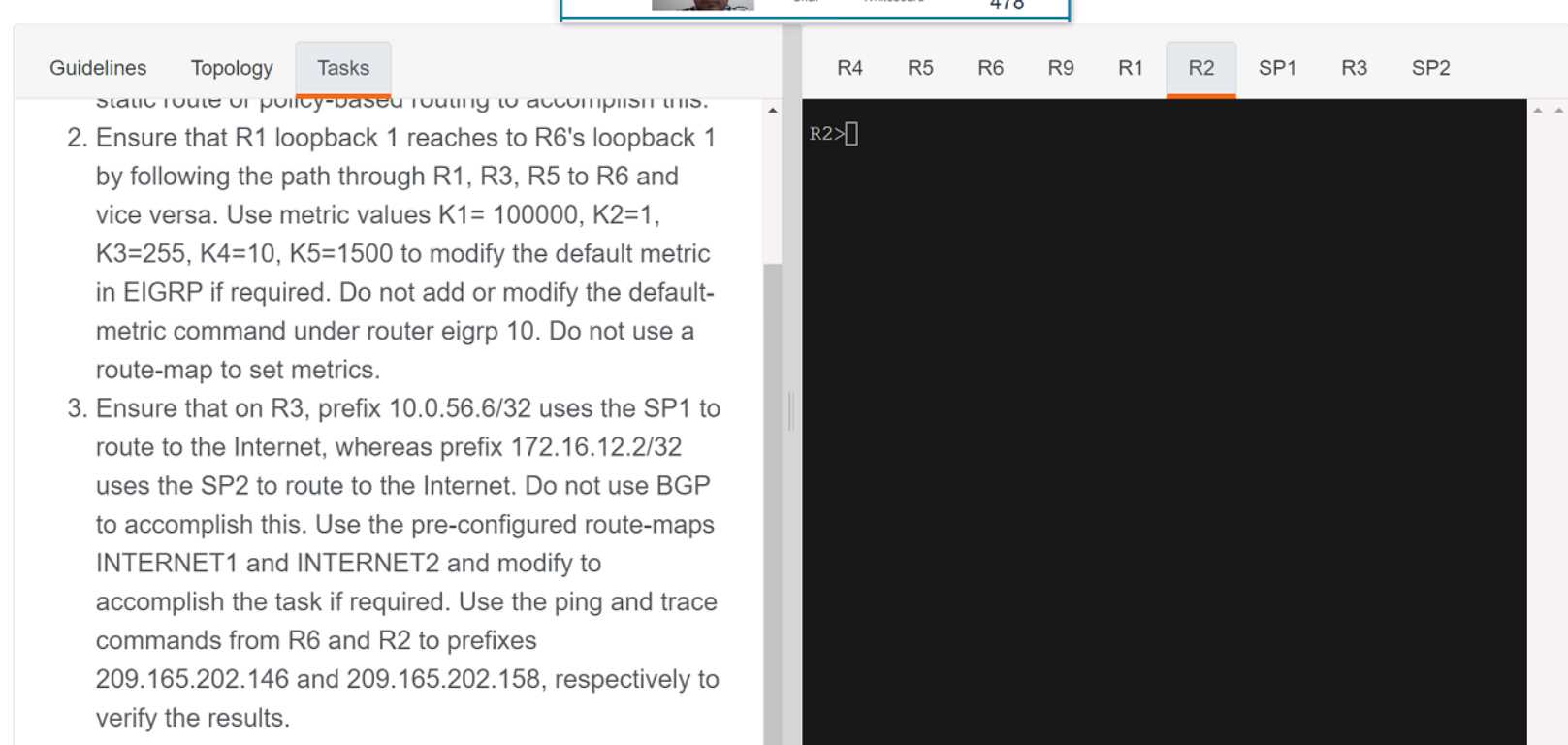
Your Answer
Q: 8
DRAG DROP Drag and drop the OSPF adjacency states from the left onto the correct descriptions on the right. 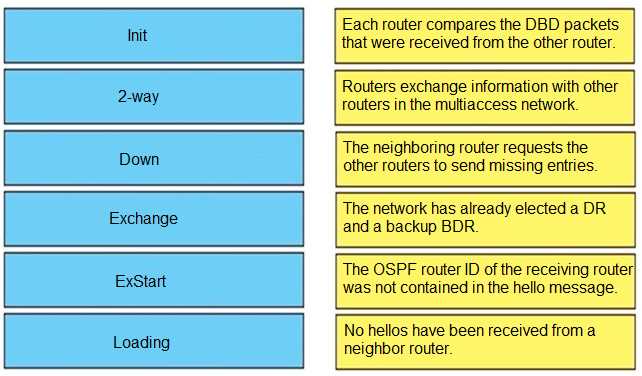
Drag & Drop
Q: 9
What are the two goals of micro BFD sessions? (Choose two.)
Options
Q: 10
DRAG DROP Drag and drop the MPLS terms from the left onto the correct definitions on the right. 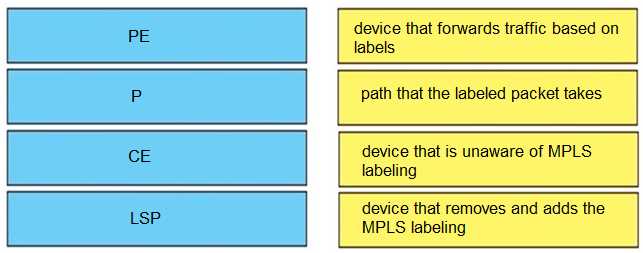
Drag & Drop
Question 1 of 10

