SC-200.pdf
DRAG DROP
You have an on-premises Windows 11 Pro device named Device1 that is onboarded to Microsoft Defender for Endpoint.
You have a Microsoft 365 subscription.
You need to identify the processes running on Device1 and which network connections the processes have open. The solution must minimize administrative effort.
Which four actions should you perform in the Microsoft Defender portal in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

HOTSPOT You have an Azure subscription that contains a Log Analytics workspace named Workspace1. You configure Azure activity logs and Microsoft Entra ID logs to be forwarded to Workspace1. You need to identify which Azure resources have been queried or modified by risky users. How should you complete the KQL query? To answer, select the appropriate options in the answer area.
HOTSPOT You are informed of an increase in malicious email being received by users. You need to create an advanced hunting query in Microsoft 365 Defender to identify whether the accounts of the email recipients were compromised. The query must return the most recent 20 sign- ins performed by the recipients within an hour of receiving the known malicious email. How should you complete the query? To answer, select the appropriate options in the answer area. 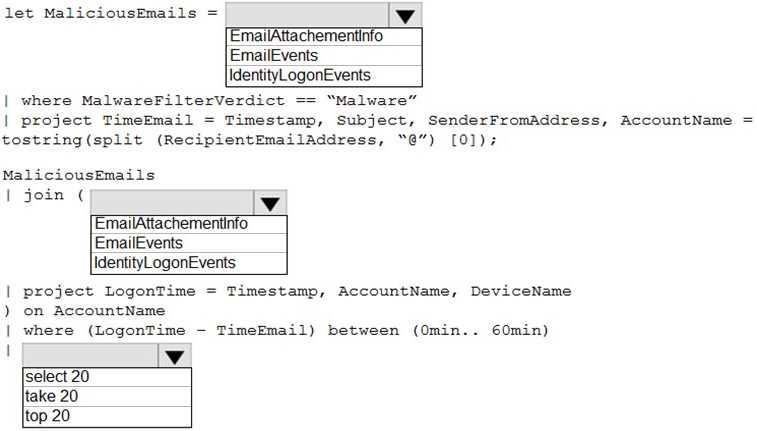
DRAG DROP You have resources in Azure and Google cloud. You need to ingest Google Cloud Platform (GCP) data into Azure Defender. In which order should you perform the actions? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order. 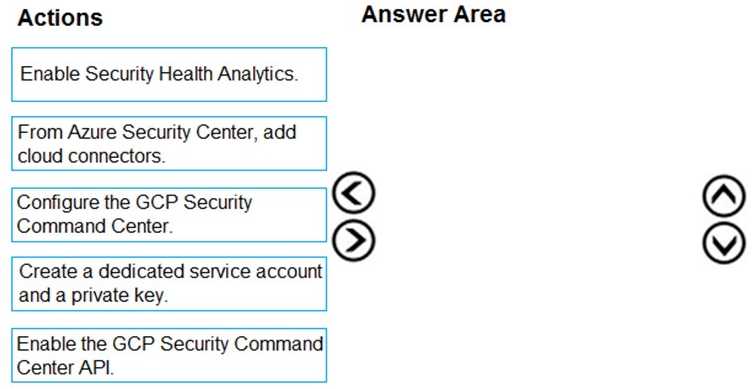
DRAG DROP A company wants to analyze by using Microsoft 365 Apps. You need to describe the connected experiences the company can use. Which connected experiences should you describe? To answer, drag the appropriate connected experiences to the correct description. Each connected experience may be used once, more than once, or not at all. You may need to drag the split between panes or scroll to view content.

DRAG DROP You have a Microsoft Sentinel workspace named workspace1 and an Azure virtual machine named VM1. You receive an alert for suspicious use of PowerShell on VM1. You need to investigate the incident, identify which event triggered the alert, and identify whether the following actions occurred on VM1 after the alert: The modification of local group memberships The purging of event logs Which three actions should you perform in sequence in the Azure portal? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. 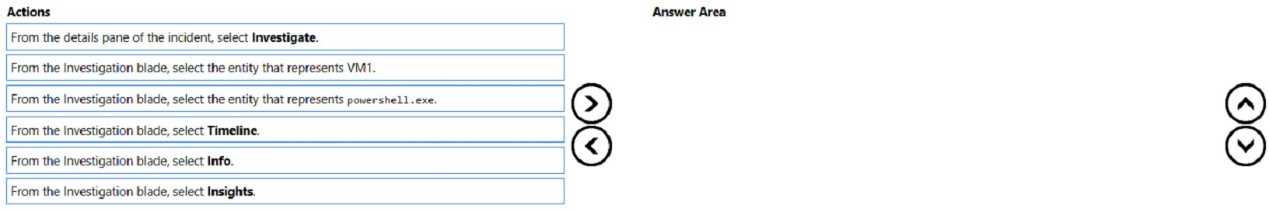
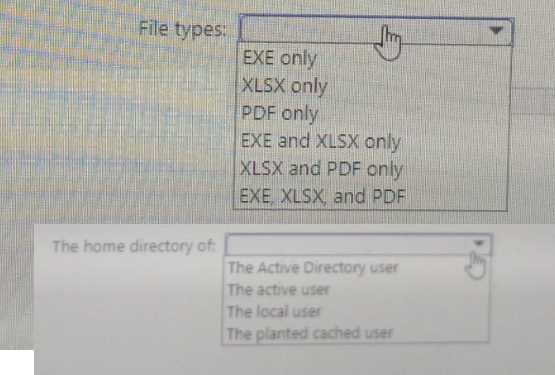
HOTSPOT You have a Microsoft 365 E5 subscription that uses Microsoft Defender XDR. You are implementing a deception rule. You need to provide a custom lure file. For the custom lure, you set Planting path to HOME. Which types of files can you use for the custom lure, and in which home directory should the file be located on a device? To answer, select the appropriate options in the answer area.