GIAC GCIH
Maria works as a professional Ethical Hacker. She recently got a project to test the security of www.we-are-secure.com. Arrange the three pre-test phases of the attack to test the security of weare-secure. 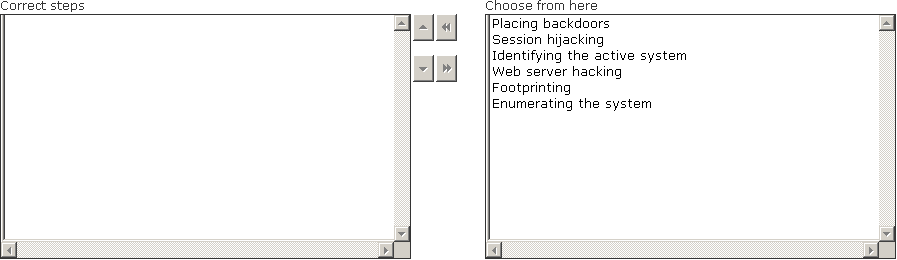
Fill in the blank with the appropriate name of the rootkit. A _______ rootkit uses device or platform firmware to create a persistent malware image.
Rick works as a Professional Ethical Hacker for PassGuide Inc. The company has opened a new branch that uses Windows-based computers. Rick has been assigned a project to check the network security of the new branch office. He wants to ensure that the company is free from remote hacking attacks. Choose the appropriate steps that Rick should perform to accomplish the task. 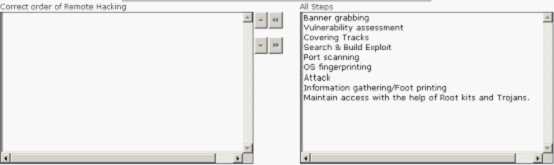
Choose and reorder the steps of an incident handling process in their correct order. 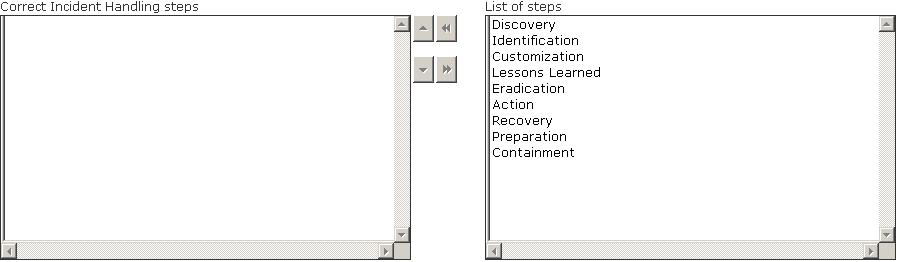
Choose the items from the given list that are required to be in the response kit of an Incident Handler. 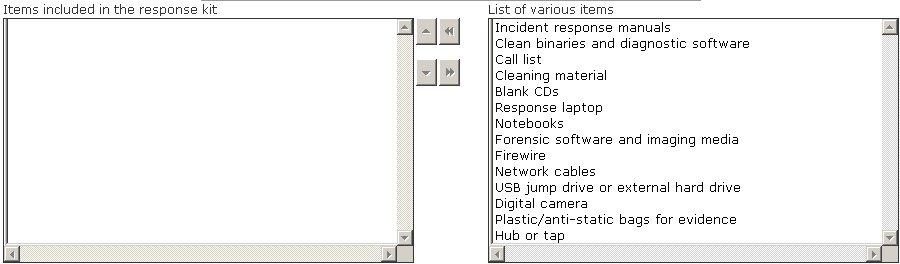
Fill in the blank with the appropriate term. ______ is a free Unix subsystem that runs on top of Windows.
Choose the correct actions performed during the Eradication step of the incident handling process. 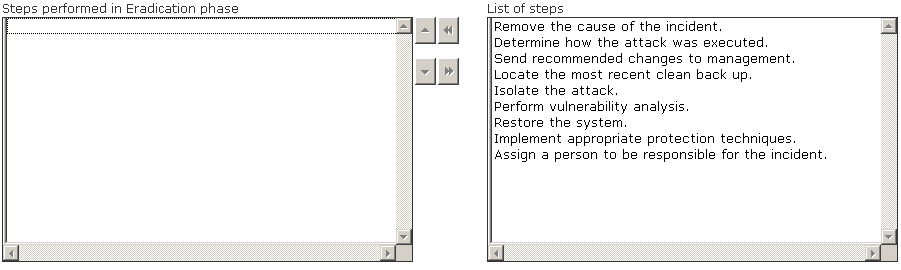
Fill in the blank with the appropriate word. StackGuard (as used by Immunix), ssp/ProPolice (as used by OpenBSD), and Microsoft's /GS option use ______ defense against buffer overflow attacks.
Choose the correct six-step process of threat modeling from the list of different steps. 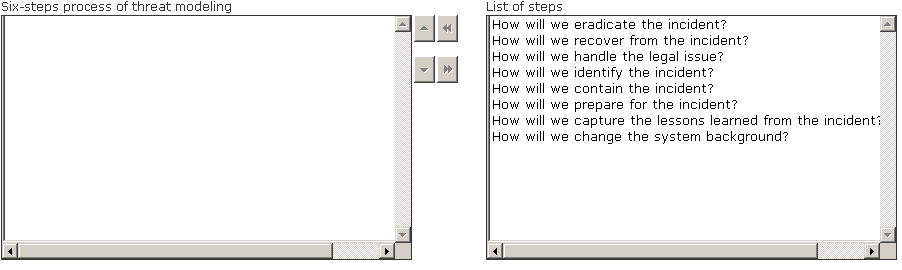
Fill in the blank with the correct numeric value. ARP poisoning is achieved in ______ steps.
Fill in the blank with the appropriate name of the attack. ______ takes best advantage of an existing authenticated connection
Fill in the blank with the appropriate option to complete the statement below. You want to block all UDP packets coming to the Linux server using the portsentry utility. For this, you have to enable the ______ option in the portsentry configuration file.
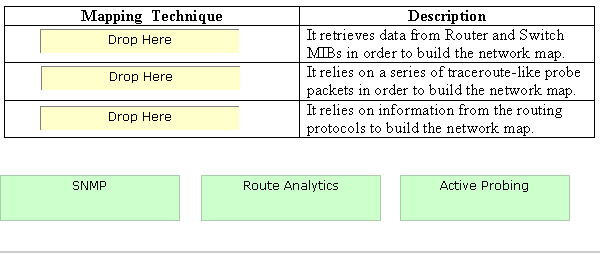
Drag and drop the mapping techniques to their respective descriptions.