Palo Alto Networks PCNSA.pdf
DRAG DROP Match the network device with the correct User-ID technology. 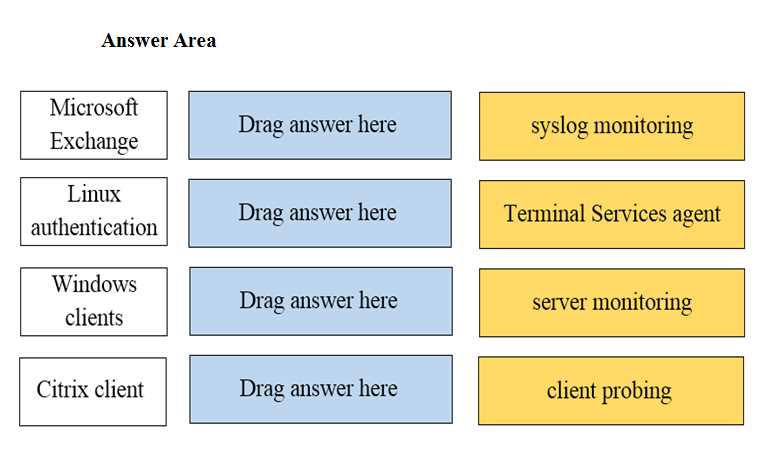
DRAG DROP Arrange the correct order that the URL classifications are processed within the system. 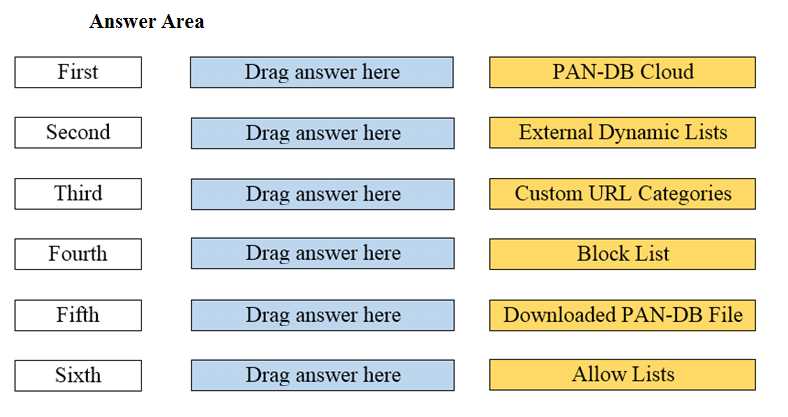
DRAG DROP Match each feature to the DoS Protection Policy or the DoS Protection Profile. 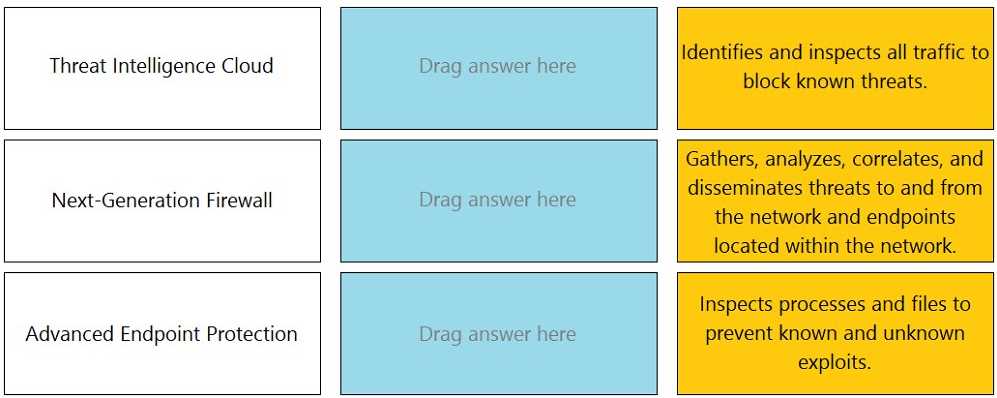
DRAG DROP Place the following steps in the packet processing order of operations from first to last. 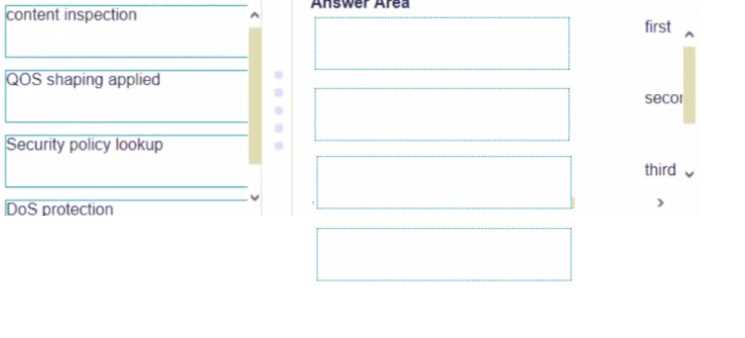
DRAG DROP Place the steps in the correct packet-processing order of operations. 
DRAG DROP Order the steps needed to create a new security zone with a Palo Alto Networks firewall. 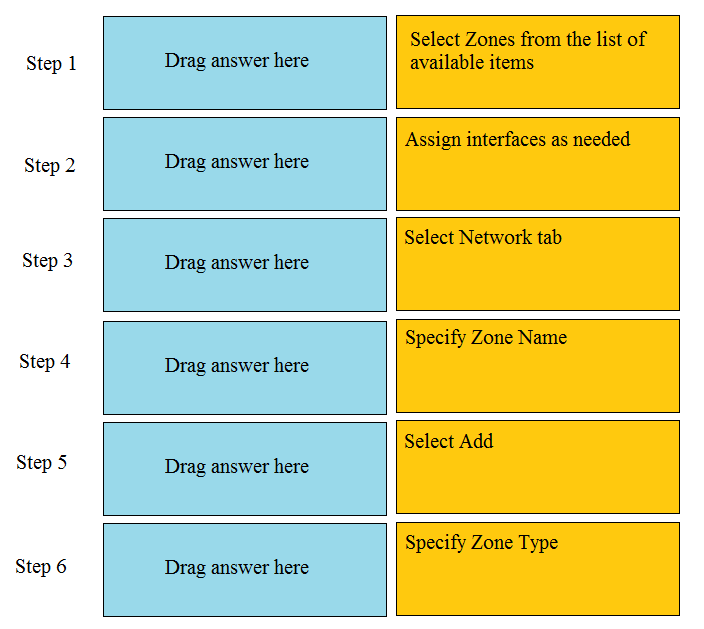
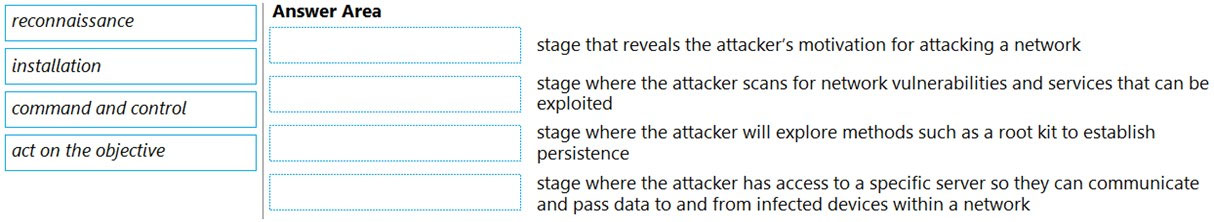
DRAG DROP Match the cyber-attack lifecycle stage to its correct description.
DRAG DROP Match each rule type with its example 
DRAG DROP Match the Cyber-Attack Lifecycle stage to its correct description. 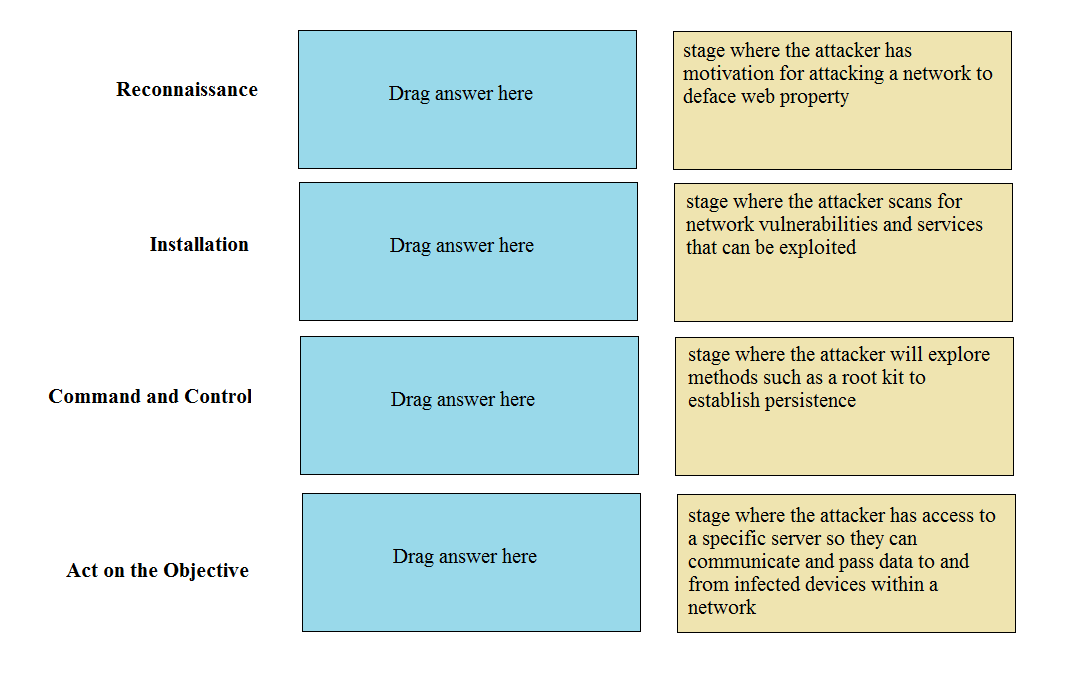
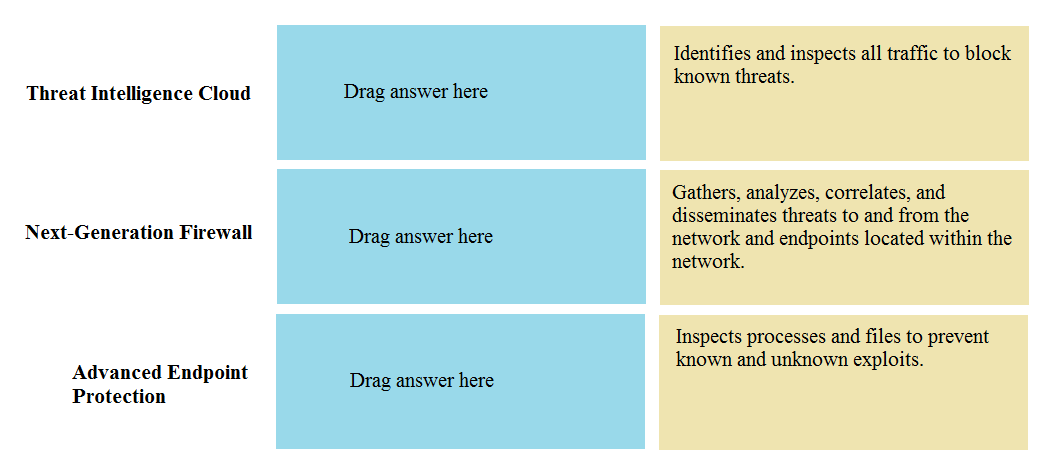
DRAG DROP Match the Palo Alto Networks Security Operating Platform architecture to its description.