Certified Ethical Hacker 312 50 v13
Q: 1
Which of the following options represents a conceptual characteristic of an anomaly-based IDS over
a signature-based IDS?
Options
Q: 2
The Payment Card Industry Data Security Standard (PCI DSS) contains six different categories of
control objectives. Each objective contains one or more requirements, which must be followed in
order to achieve compliance. Which of the following requirements would best fit under the
objective, "Implement strong access control measures"?
Options
Q: 3
Eve is spending her day scanning the library computers. She notices that Alice is using a computer
whose port 445 is active and listening. Eve uses the ENUM tool to enumerate Alice machine. From
the command prompt, she types the following command.
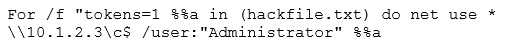 What is Eve trying to do?
What is Eve trying to do?
 What is Eve trying to do?
What is Eve trying to do?Options
Q: 4
What is the file that determines the basic configuration (specifically activities, services, broadcast
receivers, etc.) in an Android application?
Options
Q: 5
You start performing a penetration test against a specific website and have decided to start from
grabbing all the links from the main page.
What Is the best Linux pipe to achieve your milestone?
Options
Q: 6
You are performing a penetration test for a client and have gained shell access to a Windows
machine on the internal network. You intend to retrieve all DNS records for the internal domain, if
the DNS server is at 192.168.10.2 and the domain name is abccorp.local, what command would you
type at the nslookup prompt to attempt a zone transfer?
Options
Q: 7
MX record priority increases as the number increases. (True/False.)
Options
Q: 8
John, a professional hacker, targeted CyberSol Inc., an MNC. He decided to discover the loT devices
connected in the target network that are using default credentials and are vulnerable to various
hijacking attacks. For this purpose, he used an automated tool to scan the target network for specific
types of loT devices and detect whether they are using the default, factory-set credentials. What is
the tool employed by John in the above scenario?
Options
Q: 9
You are tasked to configure the DHCP server to lease the last 100 usable IP addresses in subnet to.
1.4.0/23. Which of the following IP addresses could be teased as a result of the new configuration?
Options
Q: 10
Which of the following scanning method splits the TCP header into several packets and makes it
difficult for packet filters to detect the purpose of the packet?
Options
Question 1 of 10

